A Graylog security event may represent a critical incident or activities logged by the Graylog platform indicating possible threats to system integrity and security. These events range from failed login attempts and unusual network traffic to potential malware. You can define rules and criteria to detect these events and configure alerts to ensure prompt identification, triage, and investigation of suspicious or critical activities.
In this article we will discuss events and alerts as they pertain to the Graylog Security product and within the Security interface. To learn more about how event definitions and alerts work in the core Graylog application, see the general events documentation.
Manage Security Events
The Security Events tab contains Alerts, Definitions, and Notifications. These components work together to enhance your event monitoring and incident response capabilities.
Events in both the Graylog General and Security perspectives function much the same; however, alerts in the Graylog General perspective are static as they only provide information, while alerts received in the Security perspective are actionable and tailored to security-related operations, allowing you to create enhanced workflows for triage, investigation, incident management, and incident response.
To view and manage events in the Security Events tab:
-
Navigate to the Graylog Security interface.
-
Click on theSecurity Events tab.
Now, we will review some key terms helpful in understanding how security events work through the Graylog Security interface. It is highly recommended that you also review the event management documentation for a more comprehensive explanation of these terms.
Event Definitions
Event definitions are crucial for automating the detection of important events or anomalies that could indicate security incidents, operational issues, or other significant occurrences in your IT environment. For example, an event could be a change made to a firewall policy or a failed login attempt by a blacklisted IP address. Graylog Security helps you manage your security events by allowing you to define specific criteria for what constitutes an event and alerts you when your log data matches your defined condition(s).
There are two main ways to create a new event definition:
Event Types
When defining an event in Graylog, there are two types of event conditions: filter and aggregation and event correlation.
Filter and Aggregation
Filter and aggregation conditions in Graylog allow you to define events based on criteria that filter and aggregate log messages. This involves setting conditions that filter incoming messages and then aggregating them to determine if they meet specified thresholds or patterns.
For example, an aggregation event type might include:
-
Threshold-Based Events
-
Define an event that triggers when a certain number of log messages matching specific criteria are received within a defined time window. For example, trigger an event when over 100 failed login attempts occur within 5 minutes.
-
-
Pattern Recognition
-
Detect events based on patterns in log messages, such as a web request for a commonly exploited endpoint, indicating a potential attack.
-
Event Correlation
Event Correlation conditions allow you to create events based on relationships or sequences of log messages across multiple sources or streams. This involves defining conditions that identify patterns or sequences of events rather than simple aggregation.
For example, an event correlation type might include:
-
Sequence Detection
-
Trigger an event when a specific sequence of events occurs within a short time-frame across different logs or systems. For example, detect a sequence of network access logs followed by firewall rule changes indicating a potential security policy violation.
-
-
Multi-Source Correlation
-
Combine logs from different sources (e.g. web server logs, database logs) to detect correlated events, such as a sudden spike in web traffic coinciding with a database performance degradation.
-
-
Anomaly Detection
-
Identify anomalous patterns or behaviors that span multiple log sources, such as simultaneous access attempts from geographically dispersed IP addresses, suggesting a coordinated attack.
-
Alerts
Alerts within the Graylog Security platform provide visibility into the status and progression of security incidents and allow you perform various actions directly from the alert. When an alert is triggered, it provides a detailed overview of the security event and enables various actions to streamline response efforts.
Search Panel
At the top of the page, you'll find a search bar designed to help you search through security events by using keywords. To further drill down on search results, you can use filters to find specific events or alerts.
Filters
Filters allow you to narrow down security events with precision, making it easier to focus on the data that matters most. By applying filters based on attributes like timestamp, priority, rule type, or MITRE ATT&CK techniques, you can quickly isolate relevant alerts for investigation or drill down on specific security events. This section explains how to use filters effectively to streamline threat detection and analysis within Graylog.
To filter security events:
-
Navigate to the Security layout in Graylog.
-
Go to Security Events > Alerts.
-
Click the + icon dropdown button next to Filters to view filter types:
| Filter Option | Purpose |
|---|---|
| Priority | Filters alerts by severity (e.g. Low, Medium, High). |
| Timestamp | Defines a specific time window to filter for alerts. Useful for incident review. |
|
Event Definition |
View only alerts triggered by specific detection rule sets. |
| Status | Filters based on the lifecycle stage of the alert (e.g. open, closed, investigating, false positive). |
| Type | Filters by type of security event which could either be and event or an alert. |
| Owner | Show alerts assigned to specific team members or owners. |
|
Tactic/Technique |
Map alerts to MITRE ATT&CK Tactics or Techniques (e.g. |
|
Part of Detection Chain |
Indicates if an alert is part of a broader multi-step detection chain. Useful in threat hunting and campaign tracking. |
When a filter is applied, it becomes visible as a tag next to the Filters dropdown menu. Multiple filters can be selected and combined for precision targeting.
Alert Actions
From the list of displayed alerts on the Alerts page, you can perform direct actions by clicking on a selected alert, and from the resulting expanded window you can:
-
Replay Search: Re-run the original search that triggered the event to investigate related activity.
-
Add to an Investigation: Add an alert/event into an existing or new investigation.
-
Send Notification: Trigger an alert to a Slack channel, email, or external system.
-
Assign an owner: Assign the alert or event to a team member for accountability.
-
Update Status: Change the status (Open, Investigating, Closed, etc).
-
Edit Event Definition: Modify the rule or condition that defined the alert.
-
Add notes: Add contextual notes or observations to the alert timeline.
Alerts Workflow Example
In this example, a security analyst wants to use the alert filters to identify specific alerts indicating unusual access patterns. The analyst could:
-
Set the filters to the following:
-
Tactic/Technique:
TA0001: Initial Access -
Priority:
High -
Timestamp:
Past 7 Days
-
-
Analyze the timeline to check for spikes in activity.
-
Drill into specific alerts for forensic data, logs, or assign ownership for follow-up.
Utilize the Security Events and Alerts Workflow
As log messages matching the criteria defined in your event definitions are received, Graylog evaluates them against the conditions specified and triggers an alert, if enabled. Let's explore a scenario that highlights the security events workflow, from creating an event definition to completing an investigation based on the alert notification.
Security Events and Alerts Example
In this scenario, Sally, a newly hired security analyst, is enhancing security event monitoring within her organization. As part of this effort, she has defined an event to monitor failed login attempts to detect potential brute-force attacks or unauthorized access attempts. This event definition triggers an alert when there are more than five failed login attempts from a single IP address within five minutes and sends an email notification.
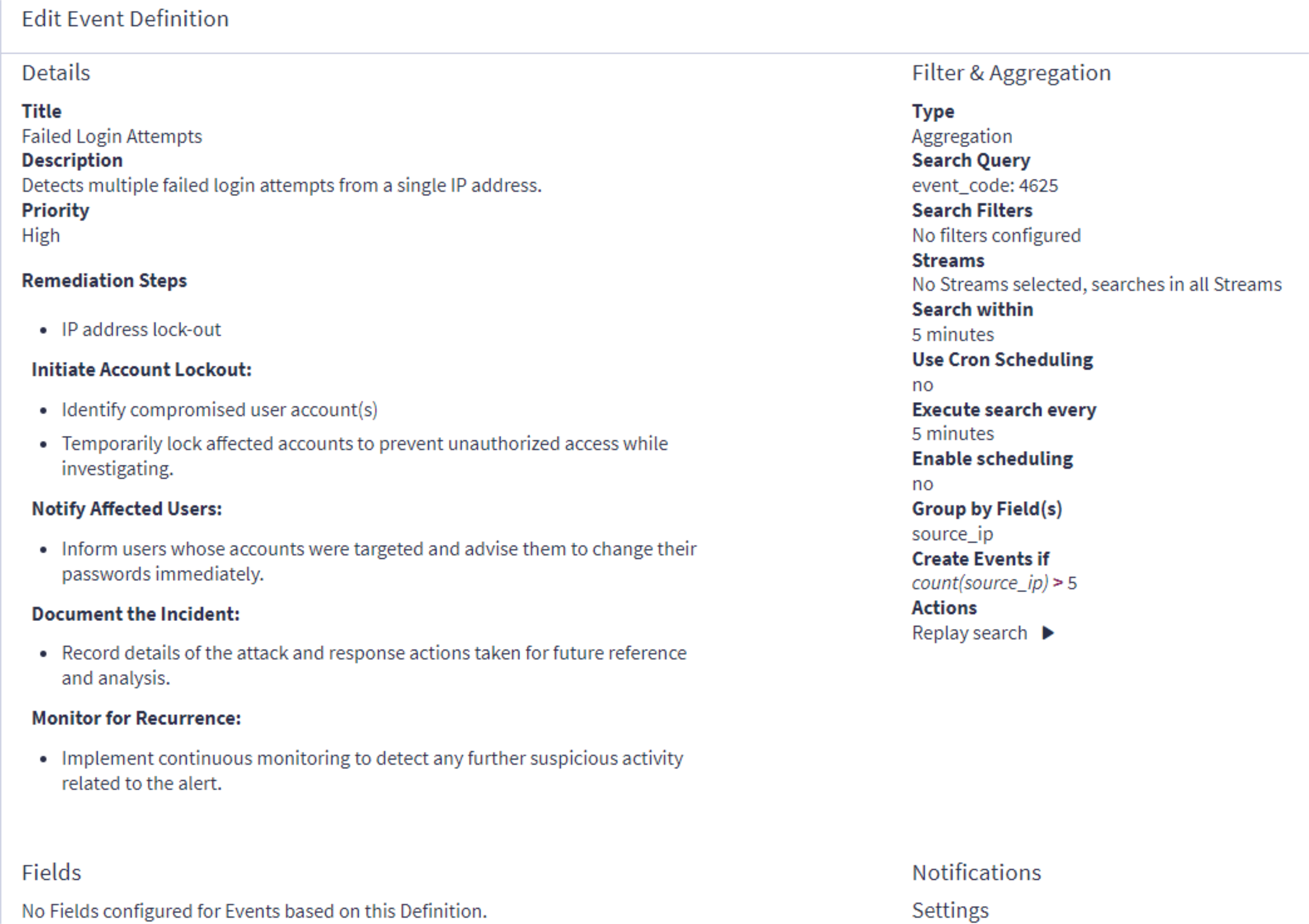
To set up this event definition, from the Graylog web interface, Sally navigates to Graylog Security > Security Events and clicks on the Create event definition button located on the top right corner of the Event Definitions page. Using the event definition wizard, Sally configures the event definition as follows:
-
Title: Failed Login Attempts
-
Description: Detects multiple failed login attempts from a single IP address
-
Remediation Steps (Optional): Lock out IP addresses
-
Priority: High
-
Event Type: Filter & Aggregation
-
Filter:
-
Search Query:
event_code: 4625 -
Search within the last: 5 minutes
-
Execute search every: 5 minutes
-
Create Events for Definition if: Aggregation of results reaches a threshold
-
-
Aggregation:
-
Group by Field(s) (Optional):
source_ip
-
-
Condition:
-
If count(source_ip) > 5
-
-
Notifications
-
Send email notification when this event is triggered.
-
The event definition is configured, and here is a summary of its details:
Then, Sally receives an email notification alert, triggered by the “Failed Login Attempts” event definition.
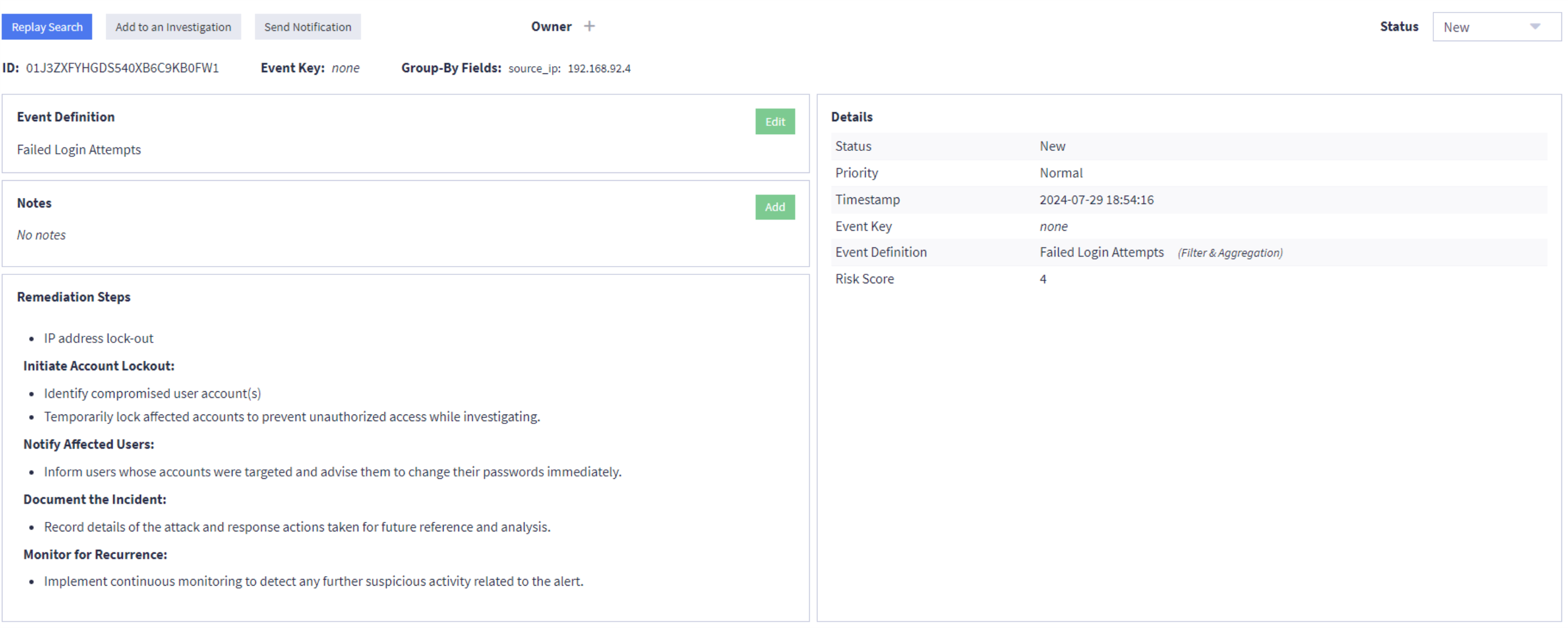
The alert indicates a high risk score, so she immediately prioritizes this alert, changes the status of the alert from New to Investigating, assigns the alert to herself as the owner, and creates an investigation from an alert by adding the alert to a new investigation. Sally then proceeds to send a notification to her team, by clicking on the Send Notification button within the alert as she reads the remediation steps and delves into investigating the issue.
To begin the investigation, Sally clicks on the Replay Search button located on the top left corner of the alert to run a search query on the event and dig into the log data. Now, Sally has contextual information about the nature of the alert, associated assets, the source of the event, usernames, and other important pieces of information relevant to the investigation.
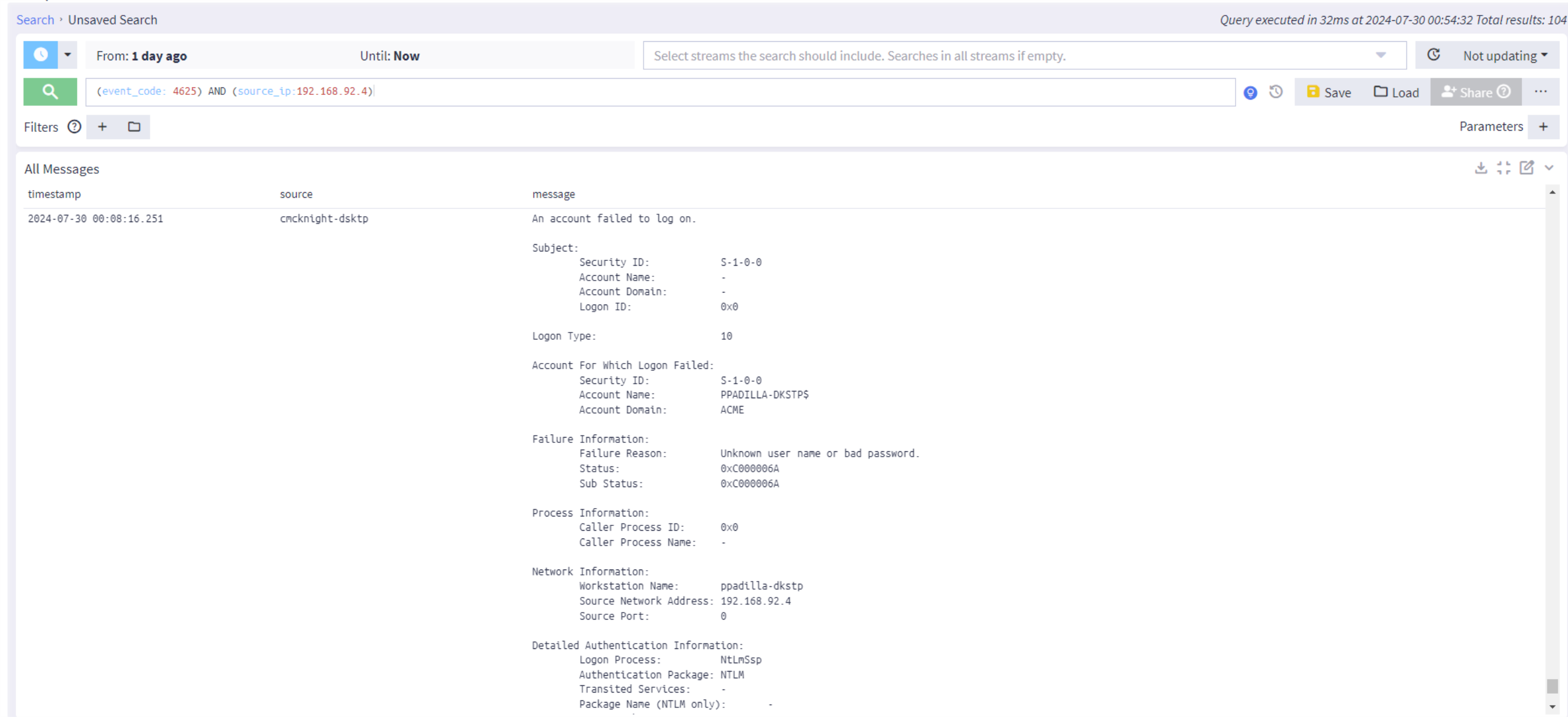
Sally utilizes her organization's incident response playbook on dealing with potential brute force attacks in addition to remediation steps contained in the alert to investigate the security event and successfully blocks the brute force attack.
Once the investigation is concluded, and Sally updates the status of the alert to "Closed," this concludes the workflow.

