The following article exclusively pertains to a Graylog Security feature or functionality. Graylog Security is a part of the Graylog centralized log management platform and requires a separate license. Contact the Graylog Sales team for more information on this product.
Graylog Security assigns risk scores to events based on the potential threat they represent to your system's security. Risk scores help you prioritize security events by quantifying and combining a variety of data points from the event definition and related assets.
This article describes the two types of risk scores in Graylog:
In addition, Graylog can raise event risk scores when it determines an event is part of a known threat campaign. When you enable this feature, event scores are raised for each event from the campaign, known as a detection chain, that Graylog recognizes. See Amplify Risk Scores with Detection Chains for more information.
Event Risk Scores
Event risk scores are a numerical assessment that represents the level of risk an event represents for your environment. This allows you to prioritize events with high risk factors for action, such as performing additional research or initiating a security investigation.
It is important to understand how risk scores are calculated as well as the user settings that affect these scores. Graylog event risk scoring is based on several factors, including log message severity, event priority, and asset priority. Not every factor is present for every event.
Event Risk Score Calculation
When a security event is created, Graylog uses three primary elements to calculate the risk score for that event:
-
Log message severity: This value comes from the GIM schema
alert_severity_levelfield. The higher the value in the log message, the higher the value that will be used in the calculation. If the log message includes noalert_severity_levelvalue, a low-severity value is used as the default. When an event is triggered based on an aggregation of multiple log messages, the average severity across all of those messages will be used in the calculation. -
Event priority: Events can created by event definitions, Sigma rules, or anomaly detectors. Graylog calculates the risk score for each type of event differently:
-
Event definitions: You set a priority value when you create an event definition. The risk-scoring algorithm assigns higher numeric values to higher priorities.
-
Sigma rules: Similar to event definitions, you can set a priority level as part of the Sigma rule definition. If not specified, the priority for a Sigma rule defaults to medium.
-
Anomaly detectors: The risk score calculation uses the
anomaly_scorevalue that is generated when an anomalous event is triggered. This value is based on theanomaly_gradeandanomaly_confidencefactors and is normalized to a value on the scale of 0-100. Refer to Anomaly Detection for more information.
-
-
Asset priority: If the event has an associated asset, the risk-scoring algorithm includes the asset priority value.
Ensure Effective Event Risk Scores
Make sure you assign your assets a priority value that reflects their risk level accurately. Values that the user sets form the basis for the calculation of risk scores. Factors such as event priorities and asset priorities directly impact the risk score calculation. Low priority event definitions will produce lower risk scores. If you create an event definition for "multiple failed logins that happen outside business hours" for example, it may be a mistake to assign a low priority. In fact, this kind of event calls for caution, and therefore the priority should be set to high. Assigning the wrong priority to your event definitions can lead to events being overlooked and risks not being addressed appropriately.
Additionally, ensure your logs are associated with related assets. An event risk score is not calculated unless there is an asset associated with the logs that triggered the event. You can associate your logs with assets by enabling the Assets pack in Illuminate or by using the set_associated_assets pipeline function in your custom processing pipelines.
-
Security event definition priority level: set or edited through the event definition wizard (Security Events > Definitions).
-
Sigma rules event priority: set or edited as part of the Sigma rule definition code (Sigma Rules > Rules).
-
Asset priority: set or edited on the Assets page for each type of asset.
-
Log-asset association: enabled with the Illuminate Assets pack or by using the set_associated_assets pipeline function
View Event Risk Scores
Risk scores are displayed on the Security Events page in the Security interface. In the list view of events, a risk score is attached to each event. You can also sort this list by the risk score column so that events with the highest risk appear at the top.
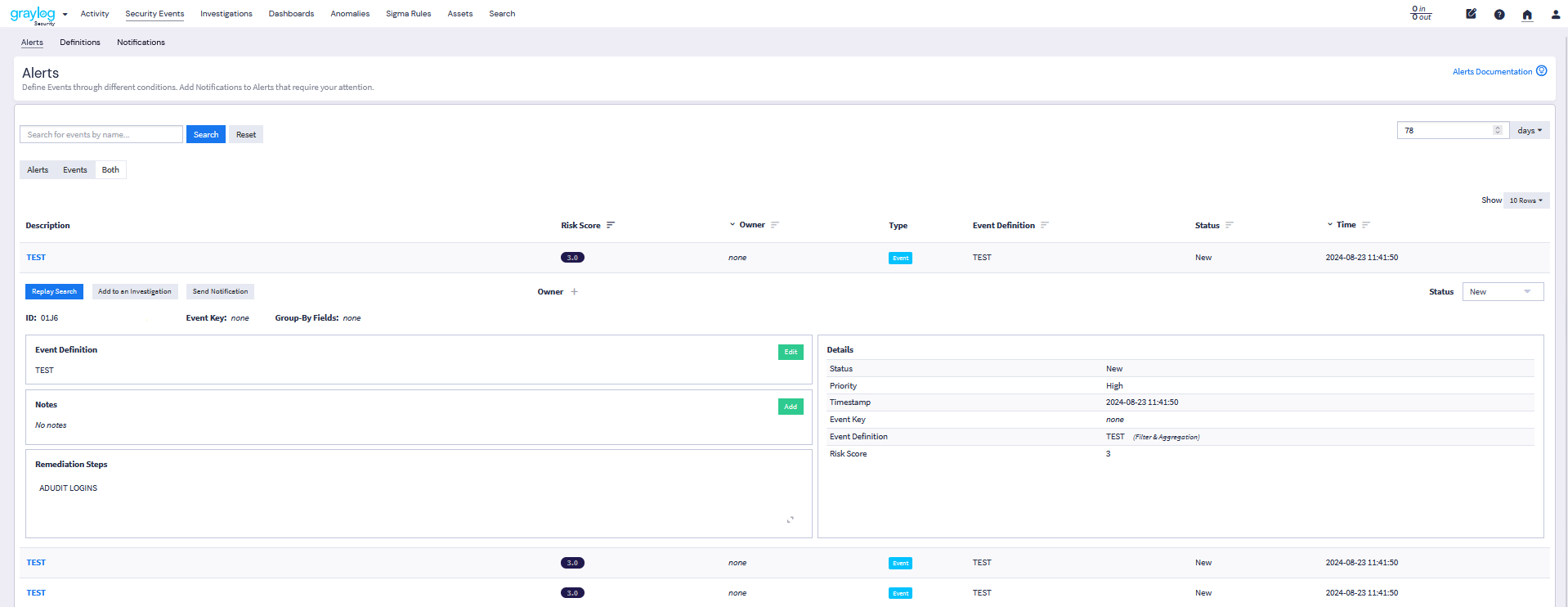
Asset Risk Scores
Triggered events are classified as "open." When an open event that has associated assets is detected, an asset risk score is calculated and assigned to those assets. The asset risk score is calculated separately from the event risk score, and so it may be different.
The asset risk score calculation is based on:
-
The highest open event risk score.
-
Any vulnerabilities imported from a vulnerability scanner and attached to a machine asset.
Asset risk scores focus on the asset itself rather than focusing specifically on a single security event. The goal is to provide you with security information about a specific asset so that you do not need to spend time searching through numerous security events to find which asset is at risk. You can begin an investigation more efficiently if the asset that needs attention can be pinpointed via a high risk score. See Asset Risk Score Calculation for more information about how security events and vulnerabilities affect asset risk score calculation.
An asset can be a user or a machine. Machine assets can have vulnerability scan data attached to them, but user assets cannot. When an asset risk score is calculated, vulnerabilities are taken into account for the machine asset.
View Asset Risk Scores
Asset risk scores may be viewed in:
-
The Graylog Security interface under the Assets tab.
-
The asset drawer that appears when you click on any asset on the Assets page.
Asset risk scores are color coded according to severity as seen in the screenshot below.
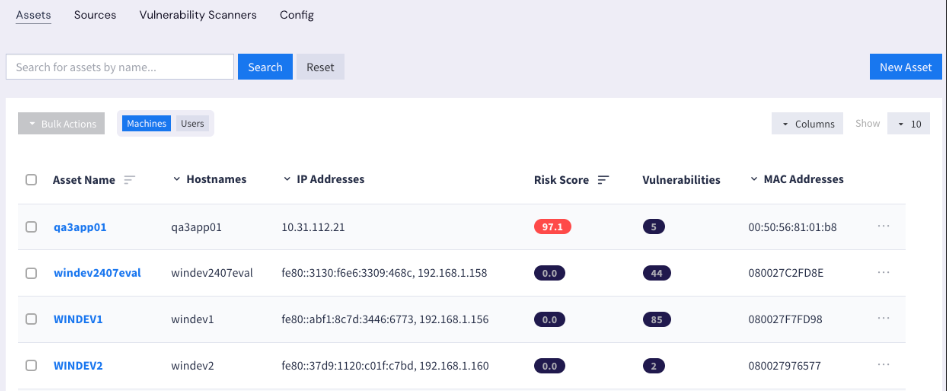
Asset Risk Score Calculation
Asset risk scores are calculated based on the highest open event risk score and any reported vulnerabilities. Because the event risk score is partially based on the event priority, user input has an important effect. The asset risk score reflects the degree of risk determined by the user when setting the event priority. See Ensure Effective Event Risk Scores for more information.
If events from multiple event definitions are associated with an asset, its risk score will be amplified to reflect the situation. When calculating the asset risk score, the event with the highest event risk score is used for the base calculation.
The asset risk score is calculated based on various factors including the alert_severity value taken from the source log data, asset priority, and asset vulnerabilities. The score is normalized to the range of 0-100, which makes it easier to interpret and compare risk scores.
An asset risk score gives you a snapshot of the current level of risk associated with an asset. Asset risk scores are calculated when events are detected and then recalculated when the events are closed. If there are no open events associated with an asset, the asset's risk score will be zero.
Ensure Effective Asset Risk Scores
Asset risk scores are based on vulnerabilities and event risk scores, which are affected by the event priority level set by a user.
If there are multiple open security events for an asset, the highest event risk score will be used when calculating the asset risk score. Therefore, the event risk score should be evaluated carefully.
Asset Risk Score Use Cases
These use cases demonstrate how the below factors affect the calculation of an asset risk score. Let's walk through a scenario for each category:
-
Asset priorities
-
Event risk scores
-
Vulnerabilities
Scenario 1
Trudy is a Tier 2 security operations center analyst at an IT company. A Tier 1 analyst has just triaged failed login attempts for two different assets. Trudy looks into the related assets. One is a company laptop and the other is the company database. Because the company database contains personally identifiable information (PII) related to all company employees, it has a high asset risk score. The laptop carries a low asset risk score. Trudy decides to start her investigation by initially focusing on the company database.
Scenario 2
Trudy notices two events with varying event risk scores. The first event involves "two failed logins to the system in under one minute." In the second event there have been "20 failed logins to the system in under one minute." Trudy deduces that the first event was most likely caused by user error, such as a user mistyping their credentials. She checks the event definitions to see that one has a low priority while the other has a high priority, but she does not assign the priorities after events have happened. In each case, the event risk score is reflected in the asset risk score.
Scenario 3
Trudy receives notifications about a possible attack targeting multiple company laptops. One of the laptops has a higher asset risk score. She sees that this laptop has vulnerabilities and has not been updated recently. Trudy focuses her attention on this vulnerable laptop.
Understand Different Scores
In some cases, the event risk score and asset risk score can be the same. When an asset risk score is not the same as an event risk score, these factors are in play:
-
Multiple associated events (e.g. an asset targeted by multiple attack tactics)
-
Vulnerabilities (e.g. machines that are not patched or updated, or other issues)
For example, a laptop that has been targeted multiple times and also has vulnerabilities has a higher asset risk score than its event risk score.
Further Reading
Explore the following additional resources and recommended readings to expand your knowledge on related topics:

