Graylog Security enables you to view different types of assets across your environment and enrich logs with asset data. Assets can be associated with specific incoming log messages that match fields in the asset database, providing detailed asset information.
Asset enrichment is achieved through activating the Illuminate:Assets processing pack or implementing a series of pipeline rules. Consequently, these linked assets become searchable and can be utilized in generating alerts. See Create Pipeline Rules with Assets for details about the fields that are used to associate assets with messages.
For more information on how assets can be used in searches, see Enhance Search with Asset Enrichment.
Get Assets Into Graylog
There are two types of assets in Graylog: machine assets and user assets. Machine assets include different types of machines located across your network, such as servers, personal computers, and firewalls. User assets can be system and human user accounts across your environment.
Both asset types can be imported and synced at an interval to make sure that any updates in the external source are reflected in Graylog. See Schedule an Asset Source Sync for more details.
There are two ways to get assets into Graylog. You can:
You can import assets from an external source, such as LDAP, Active Directory, or Microsoft 365. Alternatively, you can manually create assets through the Graylog user interface. See Import and Configure Assets for more information.
View the Asset Drawer
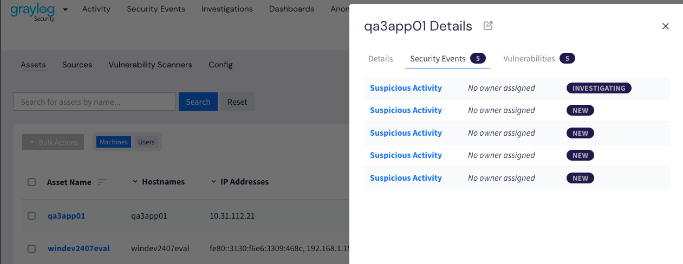
You can access an asset drawer for each asset listed under Assets in the Graylog Security user interface. The asset drawer provides details about an asset. It also provides an overview of any related security events and reported vulnerabilities. You can use this drawer to monitor your asset's standing, including the risk level and any related security events. Click on any asset to reveal its asset drawer.
The following information is displayed in an asset drawer:
-
Asset details: Asset-related details such as the asset risk score, machine or user details, geographical information, and any custom fields.
-
Asset risk scores: These scores are a useful indication of the risk associated with an asset. They are primarily based on the event risk score and any vulnerabilities. They can be used to triage security events. For more information, see Risk Scores.
-
-
Security events: You can gain access to details related to the event as well as a replay of the search.
-
Vulnerabilities: The number of associated vulnerabilities imported from an associated vulnerability scanner are displayed in the drawer. Vulnerability scores are available for machine assets only. For more information on vulnerabilities and how to enable vulnerability scanning reports, see Vulnerability Scanning.
View the Asset Drilldown Dashboard
You can access a pre-built dashboard for each asset that shows log sources and other details about the asset. The asset drilldown dashboard allows you to easily explore live data related to specific assets.
To access the dashboard, you have two options:
-
From the Assets page (General or Security perspective), click the More menu (ellipsis) in the table for any asset, then select Asset Dashboard.
-
From an asset drawer, click the Show Asset Dashboard icon beside the asset name.
The dashboard includes the following widgets:
-
Message Count
-
Top 15 Sources by Event Count
-
Top 15 Source Products by Event Count
-
Top 15 Source Products by Event Count Over Time
-
Asset Related Messages (message table)
You can replay searches and export data. You can also adjust the date/time range and apply filters to the displayed data, as with all dashboards. Because this is a pre-built dashboard, you cannot edit the widgets. However, you can select Save as at the top right to create a duplicate of the dashboard where you can edit and adjust settings for the widgets. The asset must have associated logs before the dashboard contains any useful information.
Further Reading
Explore the following additional resources and recommended readings to expand your knowledge on related topics:

