Security Interface
The Graylog Security interface provides you with an enhanced and unified view of all Graylog security components—security events, investigations, anomalies, sigma rules, and asset enrichment—in a single, accessible space. This unified view allows for seamless navigation through security functionality, utilizing widgets, metrics, notifications, and dashboards all from a central hub and eliminating the need to switch between different tabs.
Key Features
Unified Security Space
-
Centralized User Interface: All Security features are accessible from a single location, providing a holistic overview of Security components without the need to switch between various pages.
-
Optimized for Security Tasks: The dedicated Graylog Security layout is optimized to provide tools and features specifically for security analysis allowing for targeted investigation.
-
Integrated Widgets and Metrics: You can interact with Security data through widgets and metrics, allowing for real-time analysis and monitoring of security events.
Granular Control
-
Permission Settings: Assign and manage permissions with refined control over who can view or edit security-related information, ensuring compliance with organizational policies and practices.
-
Alert and Event Management: Enhance your response to alerts and events by utilizing tailored options designed to address distinct security scenarios more efficiently.
Dual Layout Interface
-
General vs. Security Layout: Switch between the default Graylog General layout and the Graylog Security layout, depending on role and security licensing permissions.
Navigate the Security Layout
To access the Graylog Security layout:
-
Log in to your Graylog instance with the necessary permissions.
-
On the top navigation bar, click the Change UI perspective drop-down menu located beside the Graylog logo on the top-left corner.
-
Select Security.
Upon switching to the Security layout, you are presented with a welcome page:
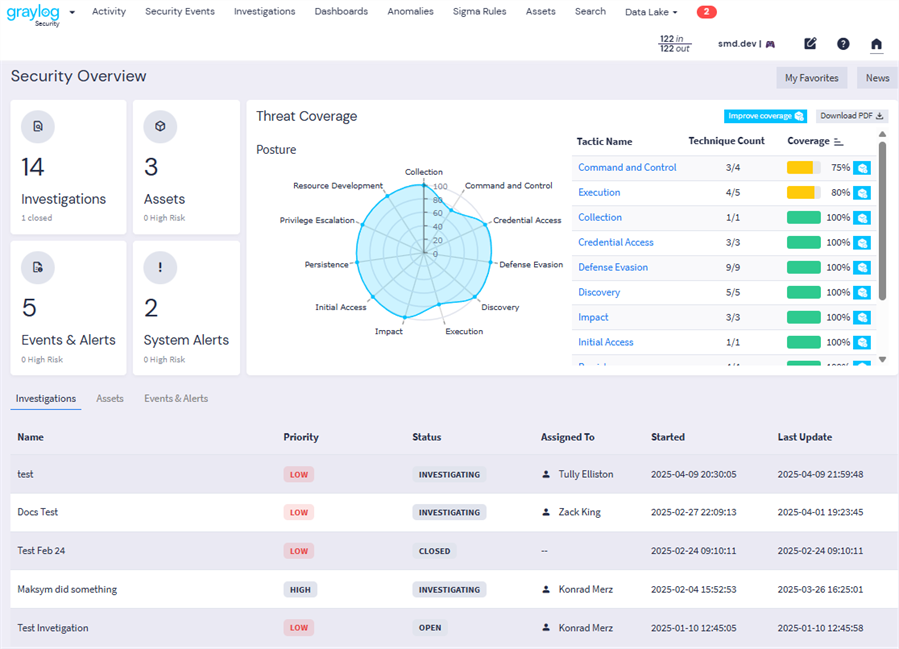
Explore Security Widgets
The following key widgets are included on the Security homepage:
-
Investigations: This widget shows the total number of active (not archived) investigations. The number of closed investigations is shown in small text. (Note that active investigations include closed investigations if they have not been archived.) Click the widget to navigate to the Investigations page.
-
Assets: This widget shows the total number of assets defined in your Graylog environment. A count of current High Risk assets is shown in small text. Click the widget to navigate to the Assets page.
-
Events & Alerts: This widget shows the total number of security events in your Graylog environment in the past day. A count of current High Risk events is shown in small text. Click the widget to navigate to the Alerts tab of the Security Events page.
-
System Alerts: This widget shows the total number of current Graylog system alerts, with High Risk alerts shown in small text. Click the widget to open a dialog box that lists all alerts. User this view to show more information about alerts and to dismiss alerts if appropriate.
-
Threat Coverage: This widget is a representation of your environment's threat coverage by Graylog as defined by the tactics and techniques listed in the MITRE ATT&CK Matrix.
The bottom section of the dashboard displays a list view table with three tabs:
-
Investigations: Track ongoing investigations with information such as status and priority of the investigation, providing for efficient management and resolution of security incidents. Click any investigation in the list to open the investigation drawer to see more detail about that investigation.
-
Assets: This view provides a list of your associated assets in Graylog along with their risk scores and other relevant information. You can toggle between machine and user assets. Click any asset in the list to open the asset drawer to see more detail about that asset.
-
Events & Alerts: This list provides real-time insights into your current security events from the past three days, enabling swift responses to detected threats. The Security interface allows for direct viewing of your security event and alerts via this widget. Click any alert in the list to open the detail pane to see more information about that event, such as associated assets and remediation steps.
At the top of the Security dashboard, find the following two buttons:
-
My Favorites: Provides quick-access to your saved favorite entities within Graylog.
-
News: Pops open the news pane, which provides the latest updates, news, and announcements from Graylog, keeping you informed about new features and best practices.

