Alerts are notifications that you can set up to inform you about an event. They can be created via the Create Notification selection on the Notifications page under Alerts or can be defined in the event definition workflow.
In this section, we explain how to create an alert and how to configure supported alert types.
Prerequisites
The following prerequisites are required before utilizing alerts with Graylog:
-
Alerts are triggered by defined events, therefore an event definition is required.
-
Graylog Enterprise is required for script and PagerDuty alerts.
Alerts can be created by selecting Notifications under the Alerts menu or by defining them in the event workflow.
Events and Alerts Page
The filter functionality on the Alerts & Events page in the General perspective allows you to quickly drill down into specific types of alerts by applying targeted filters. This helps narrow the scope of your active alerts, making it easier to focus on relevant data during monitoring or investigation.
Search Panel
At the top of the page, you'll find a search bar designed to help you search through events by using keywords. To further drill down on search results, you can use filters to find specific events or alerts.
Filters
Filters allow you to narrow down events or alerts with precision. Select the + icon dropdown next to Filters to view a list of available filter types:
| Filter Option | Purpose |
|---|---|
|
Type |
Filters by event category, either |
|
Priority |
Shows only events with selected severity levels: Low, Medium, High, Critical. |
|
Timestamp |
Defines a time window to filter events within a date/time range. Use this filter to pinpoint events for incident review. |
|
Event Definition |
View only events or alerts based on user-defined event condition types or predefined system event types. |
|
Aggregation time range |
Time window used for evaluating the event definition. This filter applies only against events triggered by event definitions defined with aggregations initially. System events are also excluded. |
|
ID |
Filter by specific event IDs, if known. |
When a filter is applied, it becomes visible as a tag next to the Filters dropdown menu. Multiple filters can be selected and combined for precision targeting.
Metrics Graph Widget
This widget plots the count of events over time. It helps quickly identify spikes or trends in event occurrences.
-
Blue Line (Events): Events are color-coded to blue and represent detected events.
-
Orange Line (Alerts): Alerts are color-coded to orange and highlights triggered alerts.
-
Interactive Axis: Hover over graph points for a summary of event counts at specific times. X-axis represents a timeline, and the Y-axis represents count.
-
Export: The chart can be exported using the download icon for reporting purposes.
-
Auto-refresh: Select update behavior by clicking the Not updating dropdown and choosing a timeframe ( e.g. 5 seconds, 10 seconds, 1 minute or 5 minutes) for real-time monitoring.
This widget is instrumental in identifying spikes in malicious behavior or assessing alert volumes over time.
If the message “No events have been found” is displayed, it means no event definition rules have triggered within the selected filters or timeframe. You may need to:
-
Expand the timestamp range.
-
Remove filters.
-
Confirm event generation on the backend is functioning.
Beneath the metrics graph, all your events and alerts are listed in a table, grouped into various columns, beginning with a description of the event/alert, priority, key, type, event definition, event definition type, timestamp and actions. Additional columns can be displayed or removed by clicking on the Columns dropdown button and selecting available column categories.
From the list of all displayed alerts and events, you can either click on an event or alert to expand and view its details or you can click the Details button in the Actions column. You can also add notifications to an event by clicking the More menu in the Actions column, then select Send Notifications.
Notifications Page
After you create alerts, they are displayed on the Notifications page. You can edit or delete existing notifications. This page also includes bulk actions. You can see if your alerts are active by selecting Test Notifications under More. A success or error message displays under the entity title.
You can also add collaborators to existing alerts by selecting Share. You can add the alert to a collection by selecting More > Manage collections, then choosing the collections the entity should be added to.
Alerts Page Example
You can troubleshoot failed inputs by filtering. For instance, an event like INPUT_FAILING: An input has failed to start is a critical system warning which surfaces in the alerts and events page. Filtering by Type = Event, Event Definition = System notificationevents and Priority = Low/High quickly isolates these kinds of events for response or escalation.
Create an Alert from the Alerts Menu
-
Navigate to the Alerts menu and select Notifications.
-
Select Create notification.
-
Complete the following fields:
Title
Create a unique title for your alert.
Description (optional)
Add additional details about your alert if desired.
Notification Type
Select the alert type from the dropdown.
-
Enter alert type details. When you select your Notification Type, additional fields based on the type appear. The alert types and key fields to configure for each are detailed in Alert Types.
-
(Optional) You can test your alert at this time by selecting Execute Test Notification. If required information is missing or incorrect, this test shows which fields need to be corrected.
-
(Optional) Enter any collaboration and sharing options. For details about adding collaborators and sharing, see Share a New Entity.
-
Click Create notification.
Create an Alert in the Event Definition Workflow
You can choose to create an alert while defining a new event.
-
In the New Event Definition workflow, select the Notifications tab.
-
Select Add notification, then select Create New Notification from the dropdown.
-
Complete the following fields:
Title
Create a unique title for your alert.
Description (optional)
Add additional details about your alert if desired.
Notification Type
Select the alert type from the dropdown.
-
Enter alert type details. When you select your Notification Type, additional fields based on the type appear. The alert types and key fields to configure for each are detailed in Alert Types.
-
(Optional) You can test your alert at this time by selecting Execute Test Notification. If required information is missing or incorrect, this test shows which fields need to be corrected.
-
(Optional) Enter any collaboration and sharing options. For details about adding collaborators and sharing, see Share a New Entity.
-
Click Add notification. Then, complete your event definition.
Metadata Available to Alerts
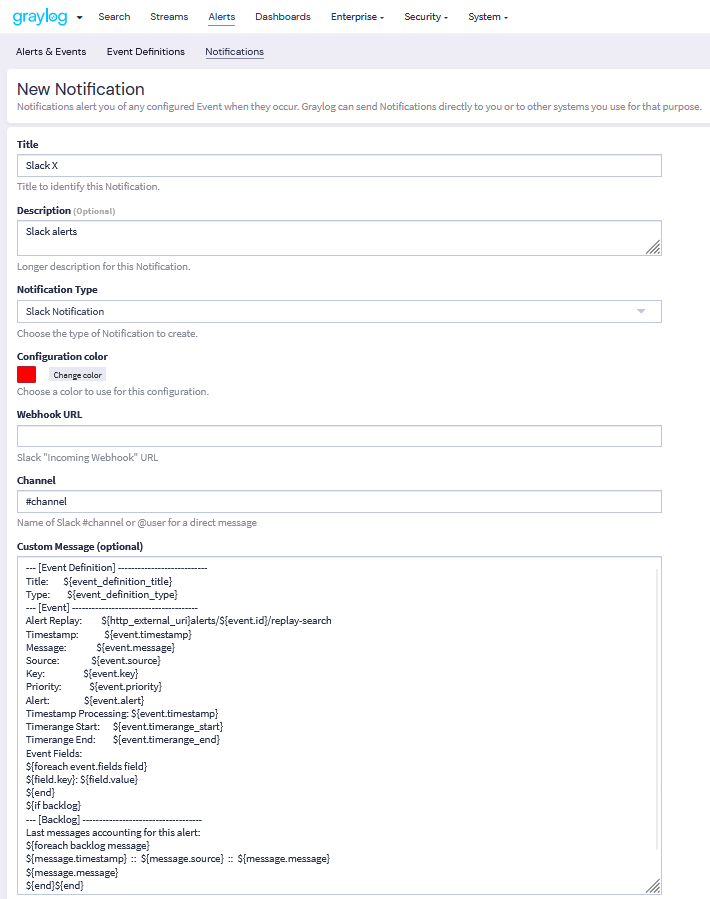
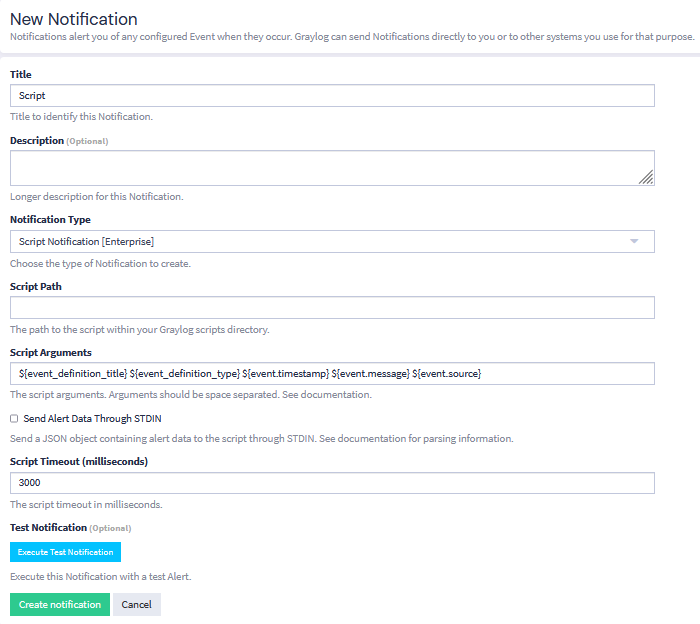
When creating alerts you can utilize metadata from the event definition, the event itself, and the event's backlog messages (if it is configured to retain a backlog). This metadata can be used when formatting email, Slack, and Microsoft Teams alerts or when providing arguments to a script alert.
For example, if you wish to include more information in your Slack alerts, you may add new fields to the Custom Message section. You may also remove any fields that you do not wish to see by deleting them from this section.
Or you could add arguments to a script alert to include more information in your alerts.
Fields that are available for each entity type are detailed below.
Event Definition Metadata
| Field | Type | Description |
|---|---|---|
|
String |
The database ID of the event definition |
event_definition_type
|
String |
The internal name of the event definition type (correlation-v1) |
event_definition_title
|
String |
The title set in the UI |
event_definition_description
|
String |
The description set in the UI |
|
String |
The internal job definition ID associated with a scheduled event definition |
job_trigger_id
|
String |
The internal ID associated with the current execution of the job. |
Event Metadata
| Field | Type | Description |
|---|---|---|
|
|
The event as it is stored in Graylog |
|
|
String |
The message ID of the stored event |
|
|
String |
The database ID of the event definition |
|
|
String |
The internal name of the event definition type ( |
|
|
String |
URN of the message or event creating this event (either |
|
|
DateTime |
The timestamp can be set to the underlying event or message (see |
|
|
DateTime |
The timestamp for when the event was created by Graylog |
|
|
DateTime |
The start of the window of data Graylog used to create this event (can be empty) |
|
|
DateTime |
The end of the window of data Graylog used to create this event (can be empty) |
|
|
String |
The list of stream IDs the event is stored in |
|
|
String |
The list of stream IDs the event pulled data from |
|
|
Boolean |
Whether this event is considered to be an alert; always |
|
|
String |
A human-friendly message describing this event |
|
|
String |
The host name of the Graylog server that created this event |
|
|
String |
The list of values making up the event’s key |
|
|
String |
The event’s key as a single string |
|
|
Long |
The event’s priority value |
|
|
Map |
The custom fields attached to the event |
Backlog Metadata
| Field | Type | Description |
|---|---|---|
|
|
The list of messages or events which lead to the alert being generated |
|
|
String |
The message ID |
|
|
String |
The name of the index the message is stored in; use together with |
|
|
String |
The |
|
|
String |
The |
|
|
DateTime |
The |
|
|
String |
The |
|
|
Map |
The remaining fields of the message (can be iterated) |
Delete Queued Alerts
If processing stops and event updates begin to pile up in the queue, then you might have unknowingly fired too many alerts. To avoid an influx of alerts, make sure to set an alert grace period for event definitions. The grace period enforces a rate limit on how many alerts are triggered for identical events. This effectively prevents queued event alerts. Without a grace period in place, too many event triggers can cause a backlog of alerts.
If you are faced with queued event alerts, there are two ways of clearing the alert queue.
Clear Alert Queue Manually
Clear the alert queue manually through the interface:
-
Navigate to the Events Definition menu by selecting Alerts > Event Definitions.
-
From the list of definitions available, click on the Information icon under Scheduling.
-
The event definition menu will expand. Here, you will see the number of queued alerts. If there are a lot of queued alerts, this typically suggests an abnormality. On the Queued alerts line, click on clear to clear queued alerts for the selected event definition.
Disable an Event
You can also clear the alert queue by disabling an event.
-
As in the previous example, navigate to the Events Definitions tab.
-
Next to your event definition, click the More drop-down button, and select Disable from the menu option for the event you wish to disable.
-
Upon selecting the Disable option, a pop-up dialog screen appears, prompting you to confirm the selection.
-
When disabled an alert is displayed confirming that the selected event definition has been disabled.

