Amplify Risk Scores with Detection Chains
Graylog can amplify risk scores when it detects events that are part of known attacks or threat campaigns. These campaigns are tracked through linked events, called detection chains.
Consider that a single event might not seem significant by itself, especially if an event has a low risk score initially. However, when Graylog detects an event that is part of a detection chain, it can raise the risk score. Then, with each additional event in the chain that is detected, the score continues to amplify, raising its associated threat potential and indicating that it is a high priority for mitigation.
This article explains how detection chains work in Graylog, how to enable this feature in your environment, and how you can keep track of these threats in the web interface.
Prerequisites
Before proceeding, ensure that the following prerequisites are met:
-
Install the Illuminate Windows Detection Chains - Sigma Rules pack.
-
Familiarity with setting up and using Sigma rules in Graylog.
Track Detection Chains
Graylog tracks detection chains through Sigma rules, which are provided in the prerequisite Illuminate content pack. After you enable the content pack, you have access to all the Sigma rules it contains. Each Sigma rule looks for a specific event. Each event is one step in a detection chain.
However, keep in mind that a detection chain represents an attack that consists of multiple events. To fully track a detection chain that occurs in your environment, you must enable each relevant Sigma rule for the chain. As additional security events in the chain are triggered, they receive higher risk scores. You can set notifications for each security event so that you receive prompt notice when a possible threat is active.
Enable Detection Chains
To enable risk score amplification with detection chains, you must first ensure the Illuminate content pack is enabled, then you must review and enable the Sigma rules for the detection chains you want Graylog to detect.
To enable the Illuminate content pack:
-
Navigate to Enterprise > Illuminate in the General layout.
-
Locate Illuminate Windows Detection Chains - Sigma Rules content pack. You can search for Windows Detection Chains to filter the list to find this content pack.
-
Select the content pack check box, then click Install Packs.
-
Click Confirm in the pop-up dialog box.
Graylog installs and enables the content pack. When installation is complete, you are returned to the Illuminate Content Hub view.
To enable Sigma rules:
-
Navigate to Security > Sigma Rules in the General layout, or select Sigma Rules from the top menu in the Security layout.
-
Search for Detection Chain to filter the list to the content packs provided by the Illuminate Windows Detection Chains - Sigma Rules content pack. These Sigma rules all include Detection Chain in their title.
-
Review the list and enable rules you want to detect in your environment. When you review individual Sigma rules from the content pack, you can apply search filters as well as edit notifications. The other fields are not available to edit.
When you enable a Sigma rule, a corresponding security event is automatically created and enabled by default. See Sigma Rules for more information.
View Active Detection Chains
A detection chain is considered active if any of the Sigma rules in the chain are detected. When additional rules from the detection chain are triggered within a one-week period, the risk score is raised.
When a detection chain is active, you have several indications in the Graylog interface:
-
The risk score for related events goes up. If multiple events in a detection chain have been triggered, the risk score should rise above 75 and be shown in red on the Alerts list. Remember that you can sort this table by risk score to show highest-risk alerts first.
-
On the Alerts list, a
Detection Chainlabel appears next to the risk score for any event related to a detection chain. -
On the alert detail page, the active detection chain is shown at the top. Click the detection chain name to see the list of events from the chain. Any rules that have been triggered are highlighted, while those yet to be detected are grayed out.
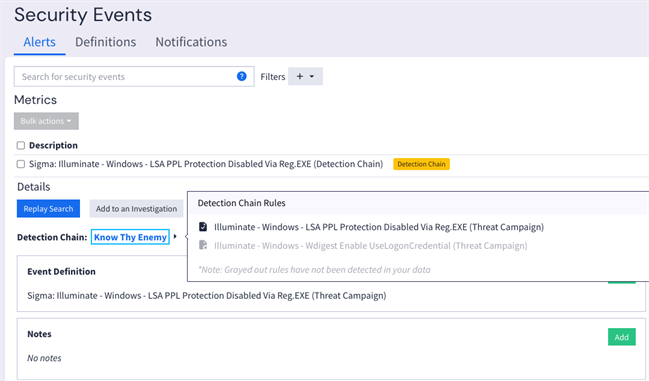 Hint: Use this view to ensure that all relevant Sigma rules are enabled. If you have a triggered event from a detection chain, make sure that you have enabled all other listed rules in that chain to receive best coverage and accurate risk scores.
Hint: Use this view to ensure that all relevant Sigma rules are enabled. If you have a triggered event from a detection chain, make sure that you have enabled all other listed rules in that chain to receive best coverage and accurate risk scores.
Further Reading
Explore the following additional resources and recommended readings to expand your knowledge on related topics:

