The following content pack is available for use with a Graylog Illuminate license and Graylog Enterprise or Graylog Security. Contact sales to learn more about obtaining Illuminate.
This preview compliance pack provides targeted visibility into Identification and Authentication (IAC), Network (NET), and Endpoint (END) events that support control requirements shared across NIST SP 800-53 Rev 5, PCI DSS v4.0, and US CMMC 2.0 Level 1. The Spotlight includes dashboards and a daily report template with tailored widgets for compliance reporting.
Supported Frameworks
This pack currently supports a subset of controls from the following compliance frameworks:
-
NIST SP 800-53 Rev 5
-
PCI DSS v4.0
-
US CMMC 2.0 Level 1
Requirements
-
Graylog 6.1.6+ with a valid Security license
-
Graylog Illuminate 6.3.0 or later
What is Provided
-
Graylog Compliance: Unified Visibility (Preview) dashboard
-
Graylog Compliance: Unified Visibility Report (Preview) report template
Using This Content Pack
GIM Categorization
This compliance pack uses events that have been categorized using Graylog Information Model (GIM) categorization codes and in some cases additional schema-defined fields. It is not restricted to a specific product. Illuminate content that leverages Core enrichment will assign GIM categories automatically where applicable. Custom packs and pipeline rules can manually assign GIM categories as well for inclusion in this pack's dashboard widget searches.
Refer to the event messages documentation for a complete list of GIM categorizations, and the enrichments documentation for more information on Illuminate enrichments.
GIM Categorization and Enrichments Used
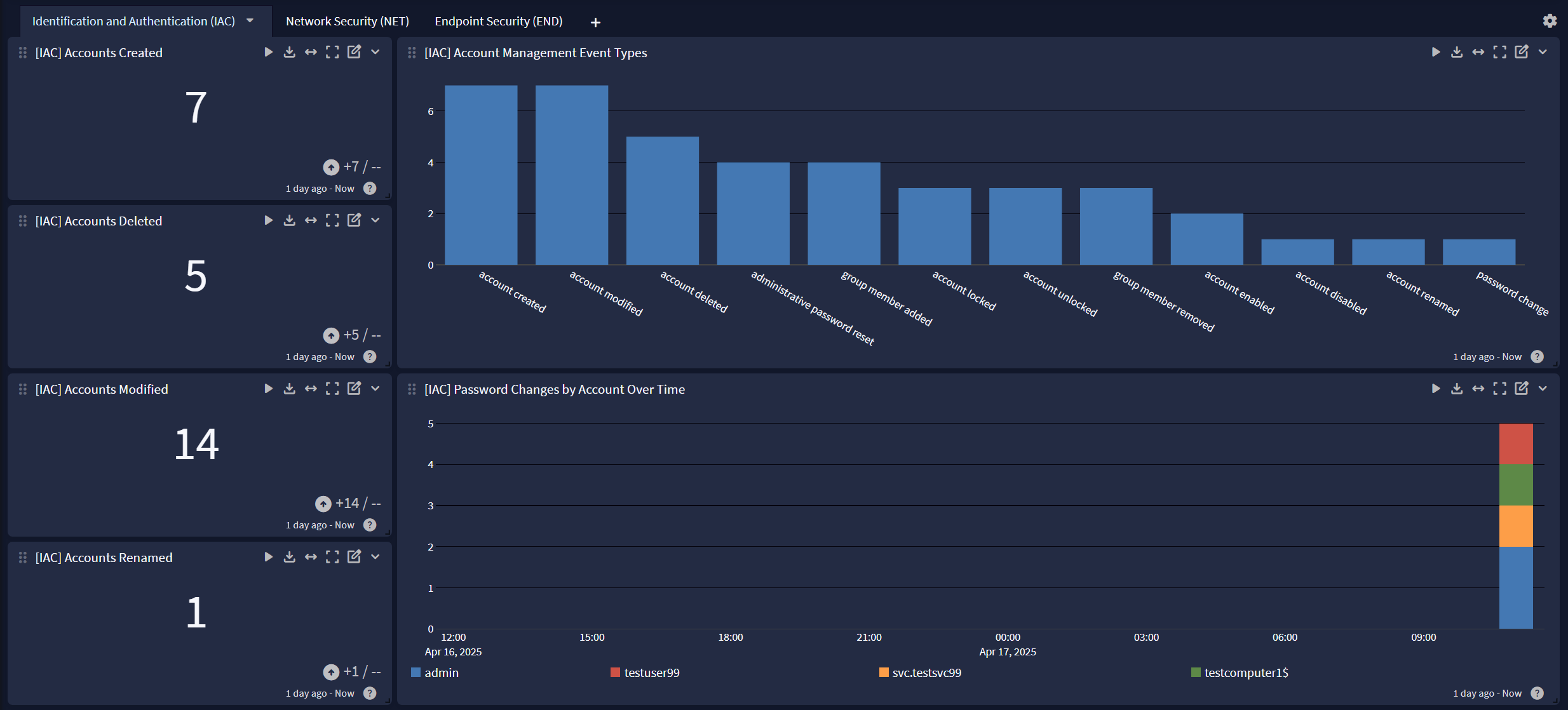
For widgets pertaining to Identification and Authentication (IAC) events, the following GIM event types are utilized:
- account created
- account deleted
- account modified
- account renamed
- account disabled
- account enabled
- account locked
- account unlocked
- group member added
- group member removed
- password change
- administrative password reset
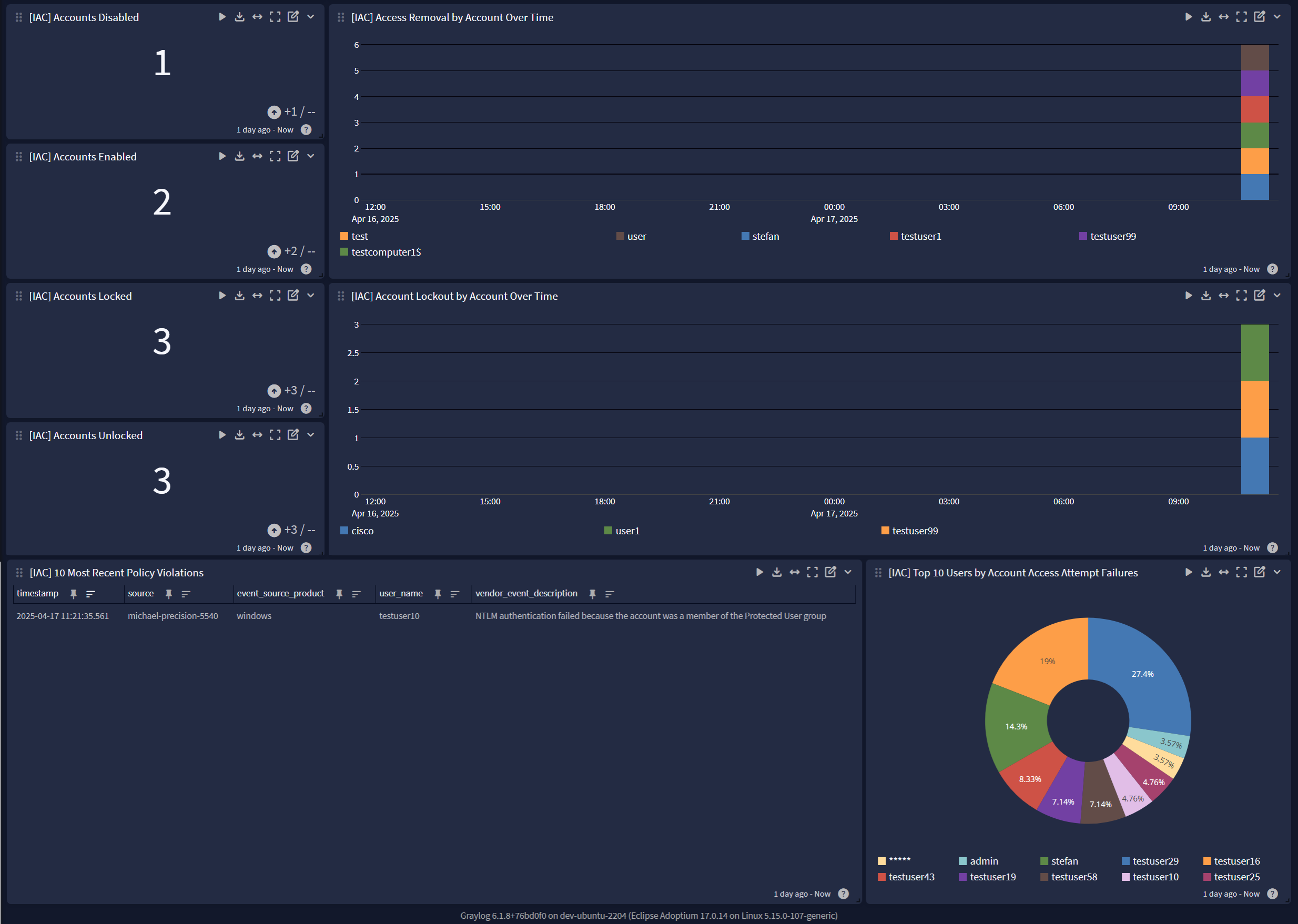
- access policy violation
- account policy violation
- credential validation
- logon
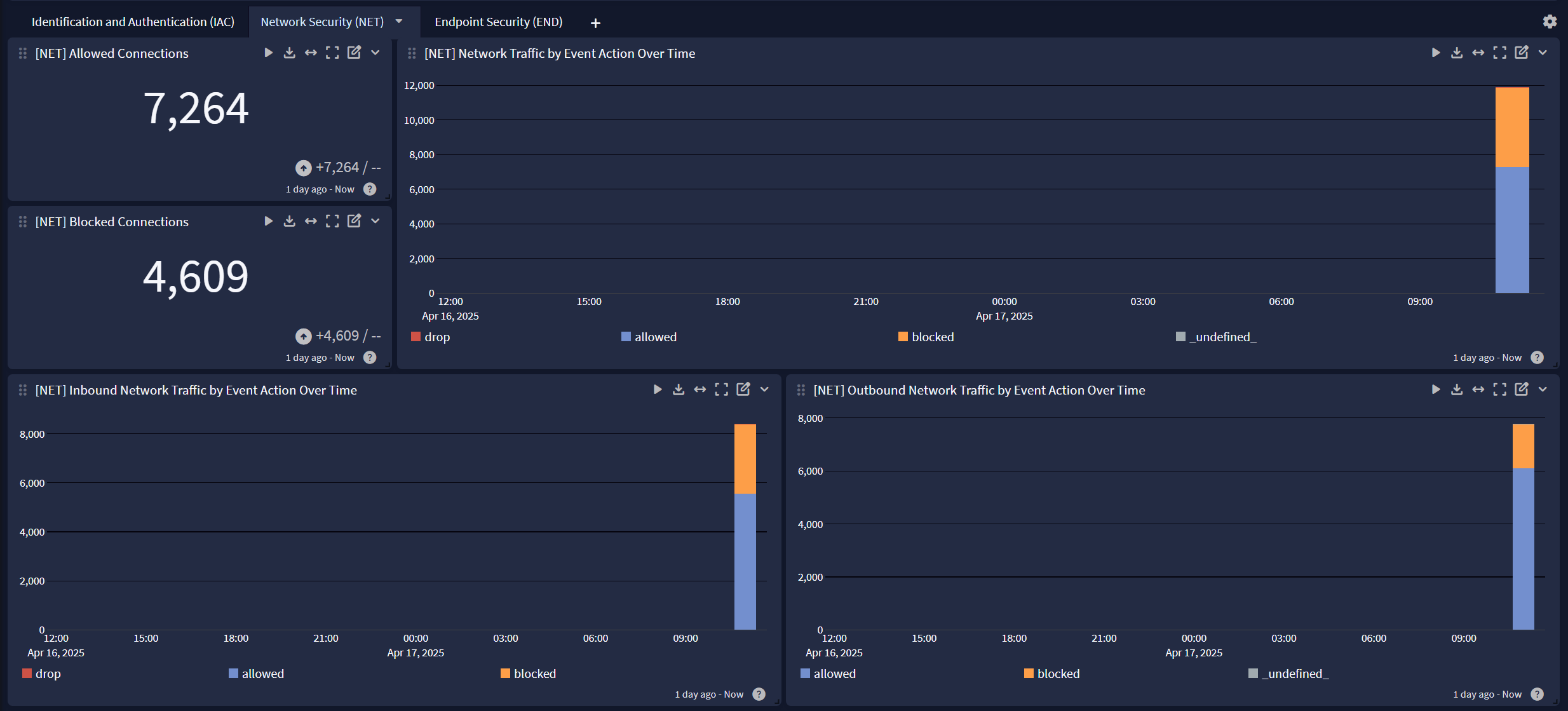
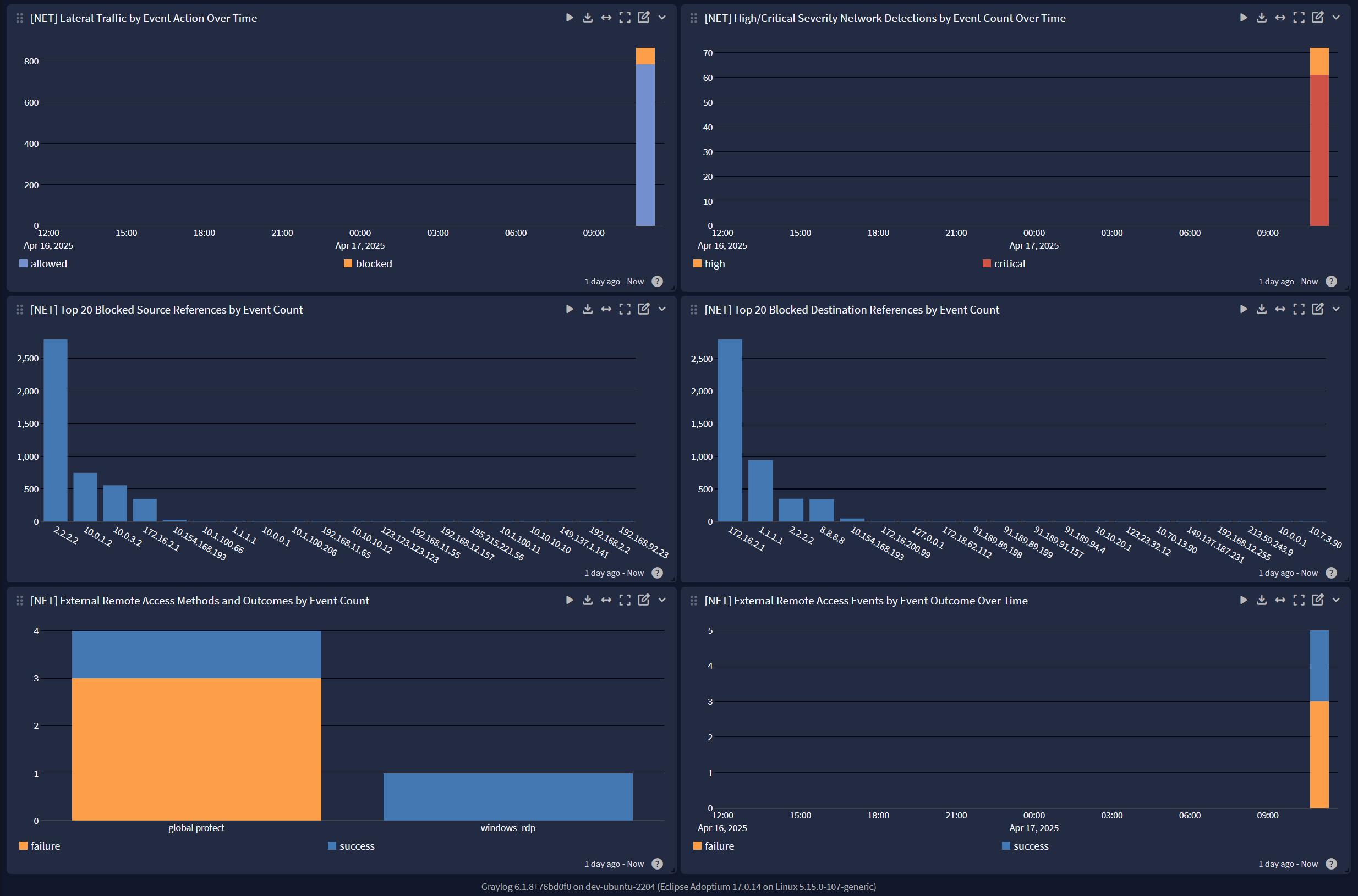
For widgets pertaining to Network (NET) events, the following GIM event categories are utilized:
- network
- authentication
For widgets pertaining to Network (NET) events, the following GIM tags are utilized:
remote_access(used in conjunction withgim_event_category: authentication)source_is_internaldestination_is_internal
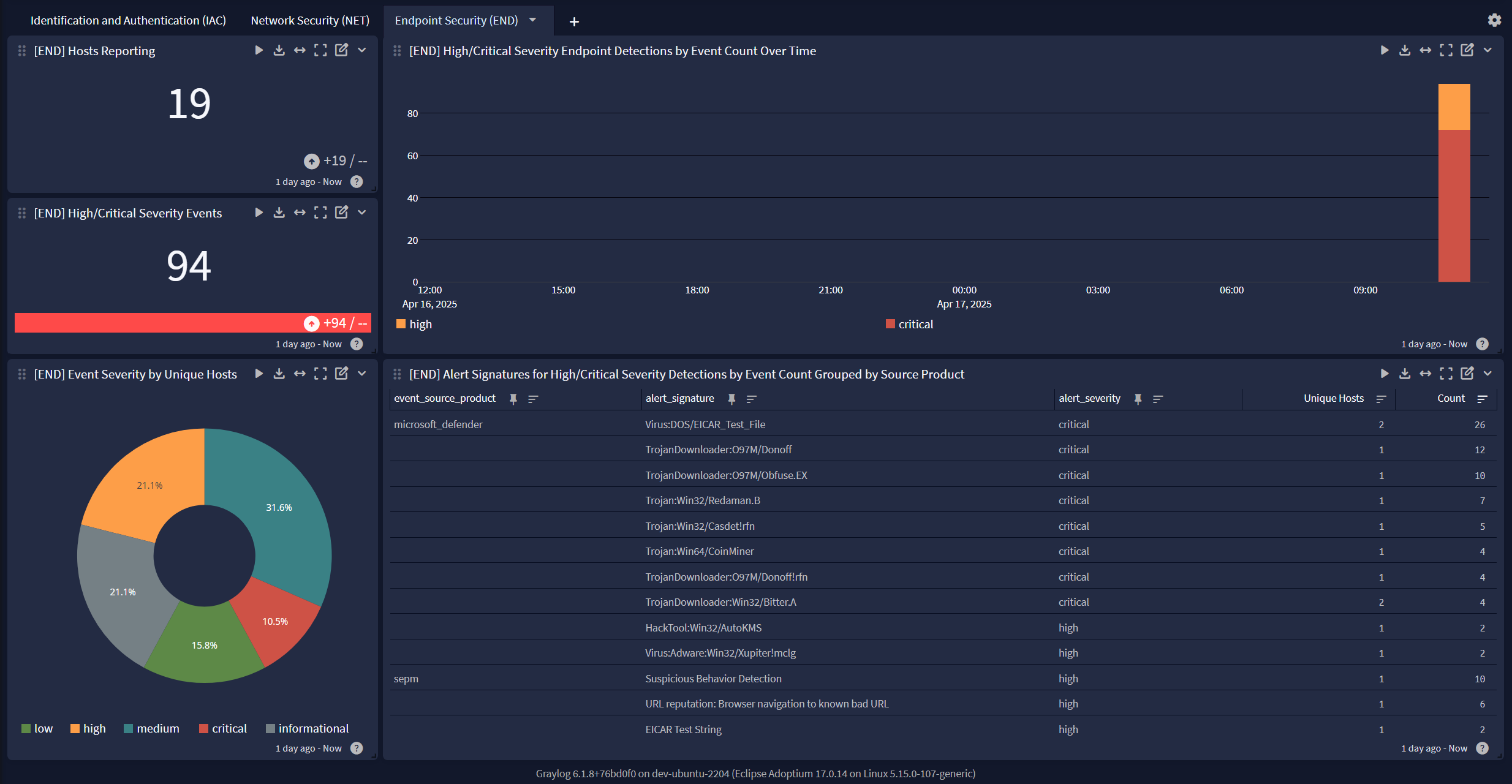
For widgets pertaining to Endpoint (END) events, the following GIM event categories are utilized:
- alert
- detection
Report Generation
This compliance pack includes a prebuilt report template for exporting dashboard data. The report can be scheduled for regular delivery via email in accordance with compliance requirements of continuous logging and monitoring and data storage over long periods of time.
Please view the reporting documentation for full details on report generation.
Scheduled compliance reports can be configured with the following example workflow in Graylog:
- Navigate to the Enterprise menu and select Reports.
- Locate the report Graylog Compliance: Unified Visibility Report (Preview).
- Open the Actions dropdown button to the right and select Edit.
- Navigate to the Delivery tab.
- Adjust any current settings as desired, such as the report delivery schedule.
- Add one or more recipients to the Email recipients input field.
- (Optional) Modify the report Content and Style to your specifications.
- Click the Update button to save the changes.
Compliance Unified Visibility Spotlight Preview
The Spotlight pack offers a dashboard with 3 tabs:
Identification and Authentication (IAC)
Network Security (NET)
Endpoint Security (END)