CrowdStrike Falcon is a cutting-edge endpoint security solution with advanced capabilities. Leveraging Artificial Intelligence (AI) and threat intelligence, Falcon empowers organizations to proactively defend against cyber threats, detect malicious activities in real-time, and respond swiftly to secure their endpoints with unmatched precision and agility.
This technology pack will:
-
Process CrowdStrike Falcon logs, providing normalization and enrichment of those events.
Supported Version(s)
-
CrowdStrike Falcon 7.15.18514.0
Requirements
-
CrowdStrike Falcon version 7.15.18514.0
Stream Configuration
This technology pack includes one stream:
-
“Illuminate: CrowdStrike Falcon Messages”
Index Set Configuration
This technology pack includes one index set definition:
- “CrowdStrike Falcon Event Log Messages”
Log Collection
- Sending logs via Graylog’s CrowdStrike Input
Log Format Example
- {"timestamp":1693337449.649,"version":"1.1","host":"customer-id","short_message":"{\"UserId\":\"api-client-id\",\"UserIp\":\"10.1.1.1\",\"OperationName\":\"reveal_token\",\"ServiceName\":\"sensor_update_policy\",\"UTCTimestamp\":1688847014,\"Attributes\":{\"device_id\":\"6614e76223cc47699c09b18e84da6425\",\"message\":\"\",\"seedID\":\"101\"}}","full_message":"{\"metadata\":{\"customerIDString\":\"customer-id\",\"offset\":2802412,\"eventType\":\"UserActivityAuditEvent\",\"eventCreationTime\":1688847014000,\"version\":\"1.0\"},\"event\":{\"UserId\":\"api-client-id\",\"UserIp\":\"10.1.1.1\",\"OperationName\":\"reveal_token\",\"ServiceName\":\"sensor_update_policy\",\"UTCTimestamp\":1688847014,\"Attributes\":{\"device_id\":\"6614e76223cc47699c09b18e84da6425\",\"message\":\"\",\"seedID\":\"101\"}}}","_event_source_product":"crowdstrike_falcon","_vendor_subtype":"UserActivityAuditEvent","_vendor_version":"1.0","_event_created":"2023-07-08T20:10:14.000Z"}
What is Provided
- We provide categorization for the following log types:
DetectionSummaryEventEppDetectionSummaryEventXdrDetectionSummaryEventAuthActivityAuditEvent
- All messages sent via the CrowdStrike API to the Graylog CrowdStrike input will be parsed but not all will receive categorization or normalization.
- We provide parsing rules to normalize and enrich CrowdStrike Falcon log messages.
| Log Type | GIM Category | GIM Subcategory |
|---|---|---|
| detection | detection | detection.default |
Input Configuration
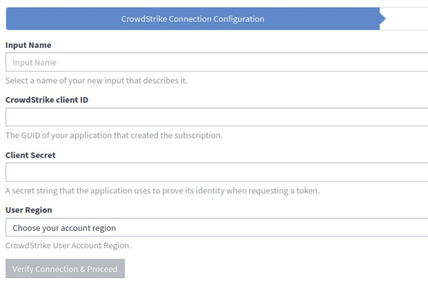
- To successfully connect your CrowdStrike Falcon device to the Graylog CrowdStrike input, you will need your CrowdStrike client ID and your Client Secret.
- Once connected, your CrowdStrike logs should successfully be coming into your Graylog instance.
Events Processed by This Technology Pack
The CrowdStrike Falcon content pack supports parsing for all fields and GIM categorization for the CustomerIOCEvent, DetectionSummaryEvent, and UserActivityAuditEvent events.
CrowdStrike Spotlight Content Pack
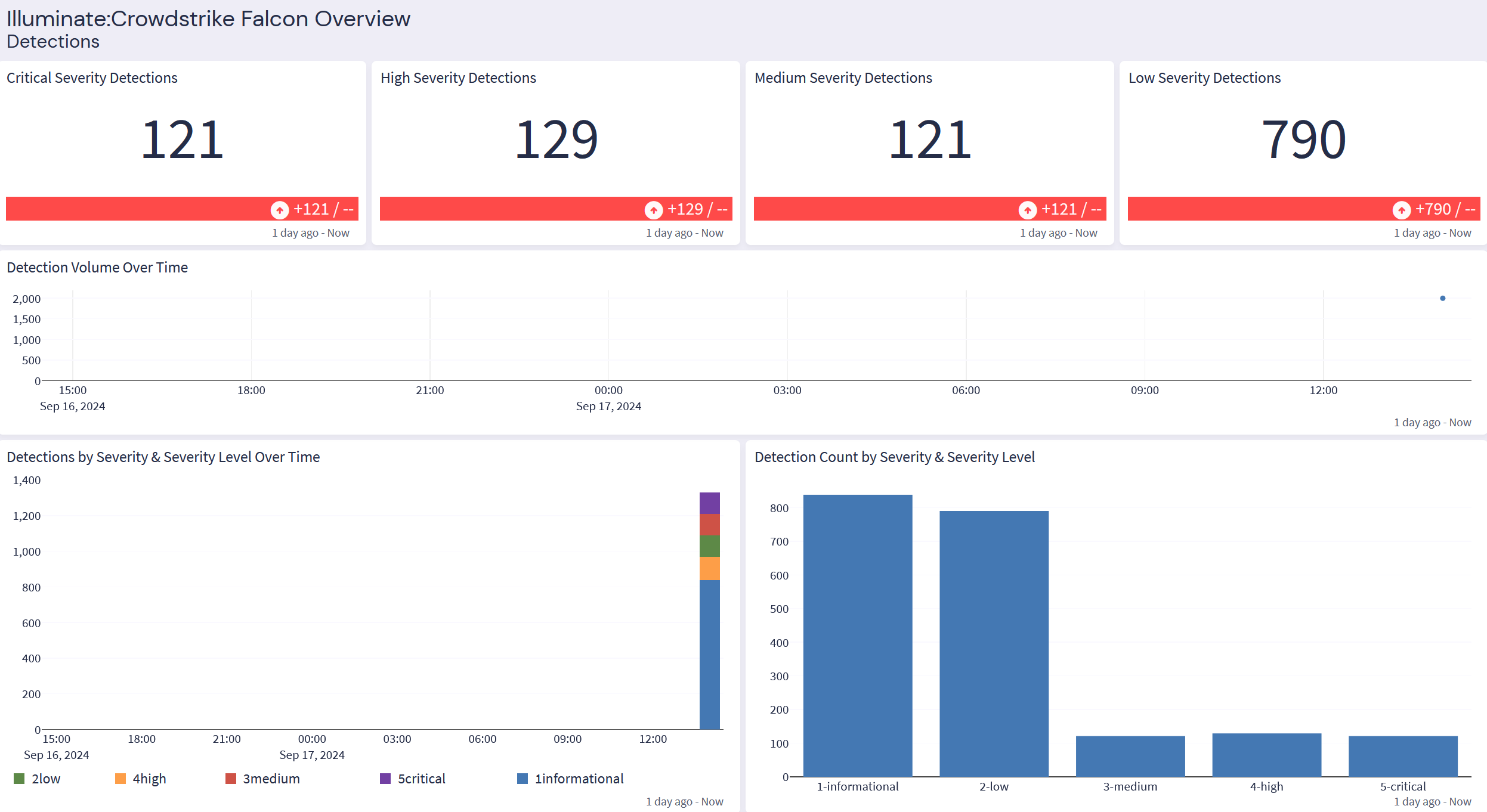
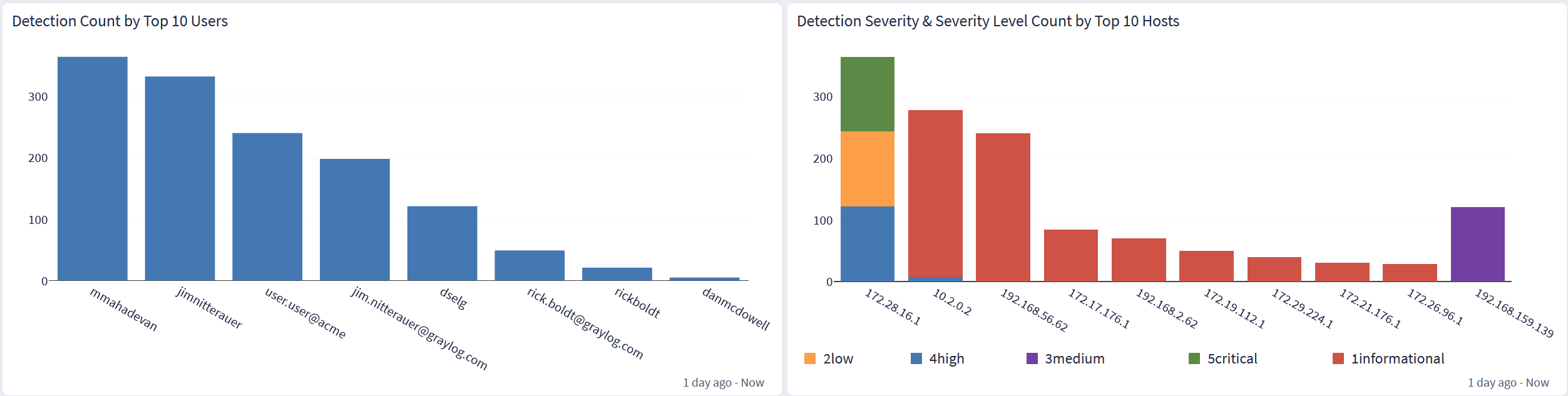
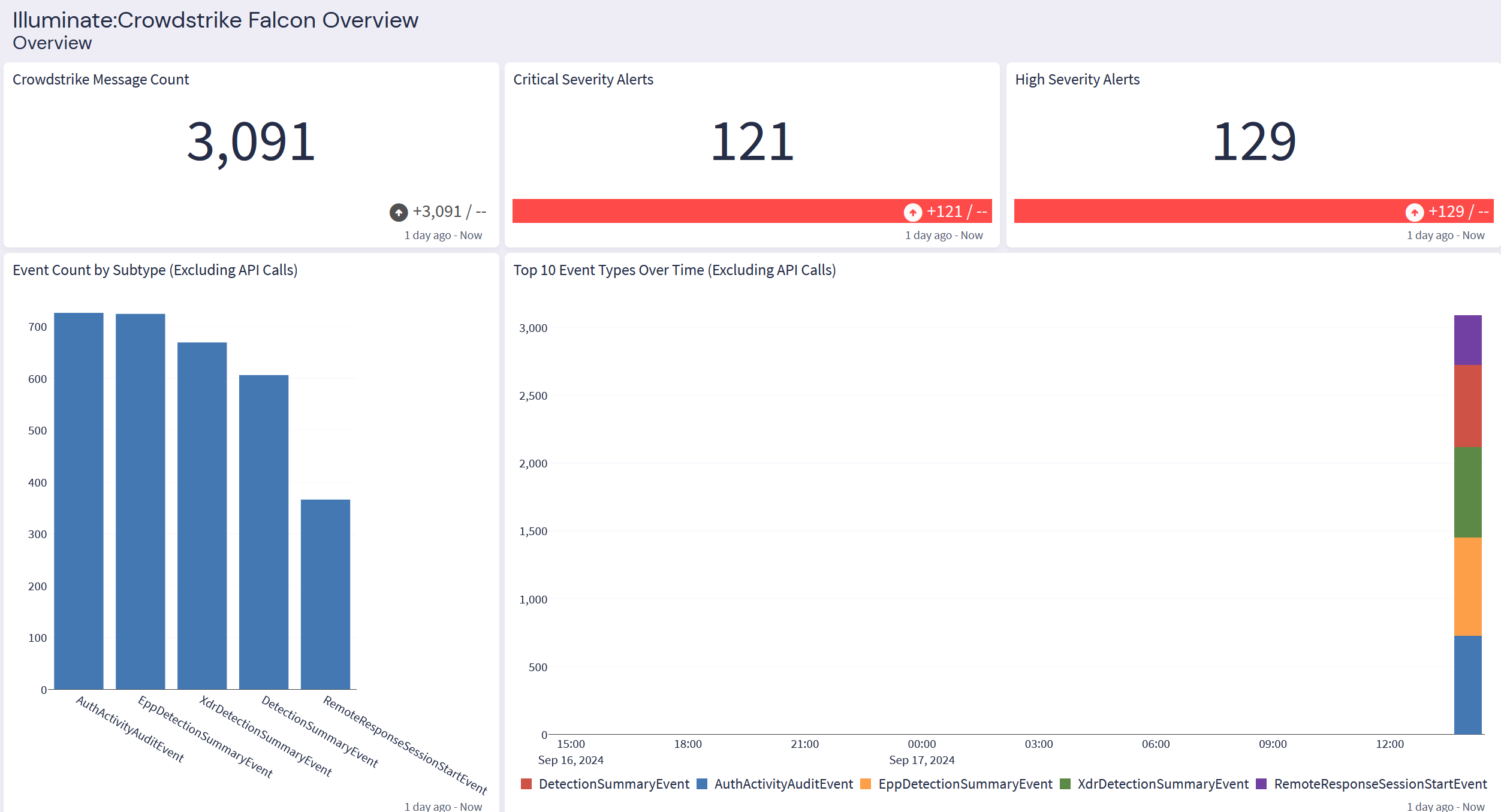
CrowdStrike Falcon: Overview Tab
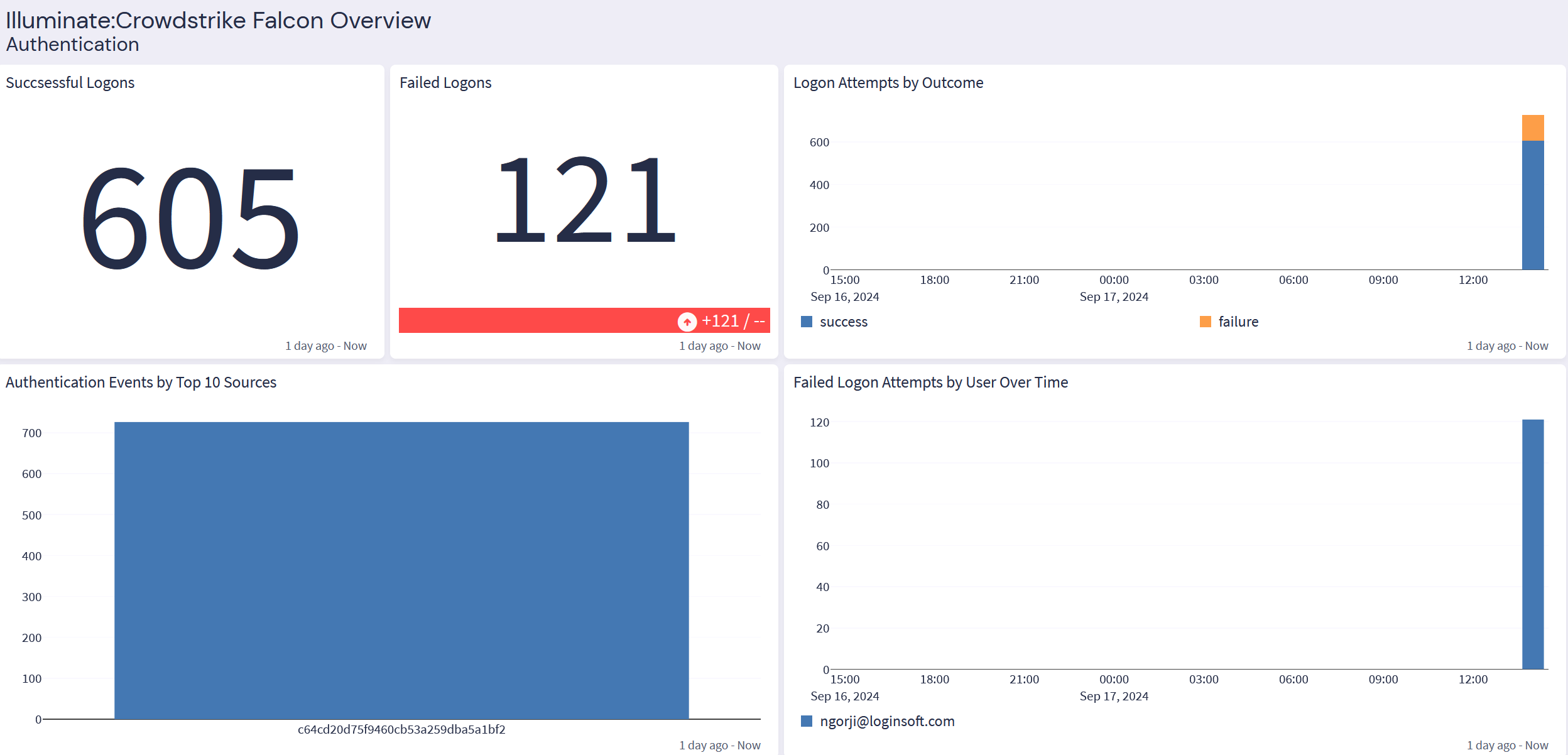
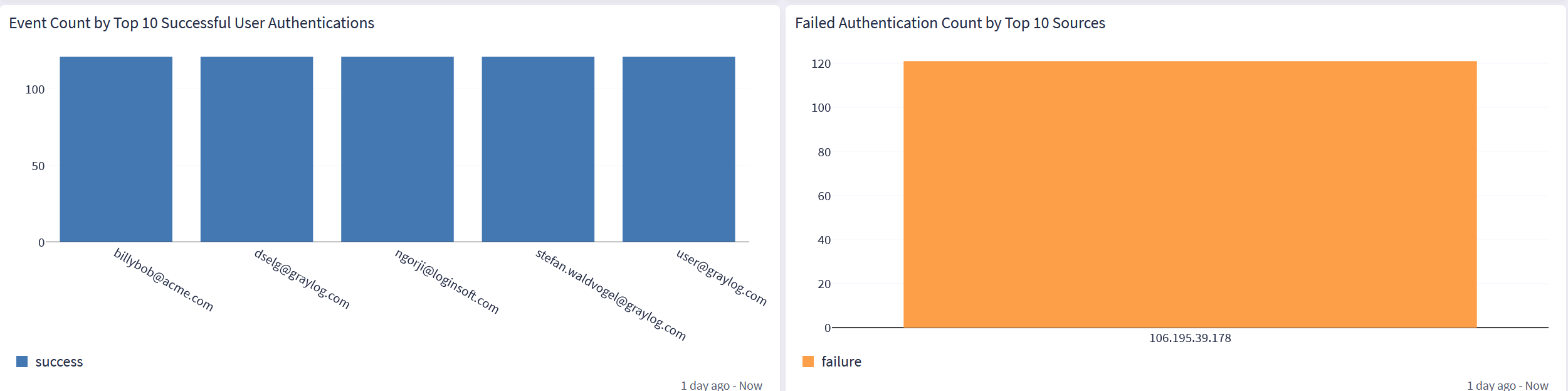
CrowdStrike Falcon: Authentication Tab
CrowdStrike Falcon: Alert Tab