Symantec Endpoint Detection and Response is used to detect advanced attacks using machine learning and global threat intelligence to minimize false positives and help ensure high levels of productivity for security teams.
Supported Version(s)
- Symantec EDR Appliance 4.8
Requirements
-
Symantec Endpoint Security Complete subscription
-
Symantec Endpoint Security Manager
-
OAuth Client to interact with Graylog input
-
Minimum of Graylog 6.0+ with a valid Enterprise license
Stream Configuration
This technology pack includes one stream:
- Illuminate:Symantec Endpoint Detection and Response Messages
Index Set Configuration
This technology pack includes one index set definition:
- Symantec Endpoint Detection and Response Logs
Log Collection
- Symantec Endpoint Detection and Response (EDR) utitlizes the Graylog Symantec EDR Events input that ingests event and incident logs in JSON format (as seen below).
Configuration Example
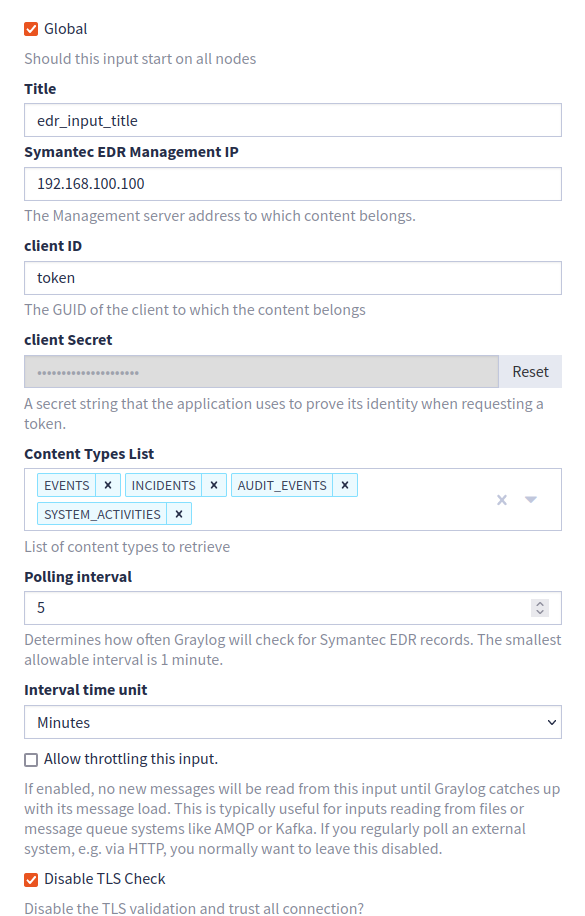
See the Graylog Symantec EDR Events input documentation for configuration details.
Log Format Example
{"type_id":8001,"severity_id":1,"device_time":"2024-04-24T00:02:35.215Z","log_time":"2024-04-23T11:47:49.747Z","device_uid":"3fb76a67-874f-4cd1-8d96-aeba1d20bbaf","device_name":"WIN-ABCD","device_ip":"192.168.1.1","device_ipv6":"fe80:0000:0000:0000:071b:8ecb:abcd:efgh","device_os_name":"Windows Server 2019 ","user_name":"SYSTEM","user_domain":"NT AUTHORITY","user_sid":"S-1-5-18","device_domain":"domain.com","operation":1,"event_actor":{"pid":756,"uid":"DEDEA815-FD16-F1EE-8DB5-60ABC5EF1DD4","cmd_line":"C:\\Windows\\system32\\services.exe","start_time":"2024-04-18T00:02:17.522Z","signature_level_id":60,"integrity_id":6,"user":{"name":"SYSTEM","sid":"S-1-5-18"},"file":{"name":"services.exe","md5":"2d072114fa0b9e2b51830510fa5f0f69","modified":"2022-11-05T18:59:47.734Z","path":"c:\\windows\\system32\\services.exe","normalized_path":"CSIDL_SYSTEM\\services.exe","signature_company_name":"Microsoft Windows Publisher","signature_value_ids":[3,5],"sha2":"751cd7ab78b18a2d8a55c47ca75b90a14234ac974d81be5f198d301b59183873","original_name":"services.exe"}},"process":{"pid":13896,"uid":"560F4CF9-01B7-F1EF-8DB5-98261F32744E","cmd_line":"C:\\Windows\\system32\\svchost.exe -k netsvcs -p -s wisvc","signature_level_id":60,"integrity_id":6,"user":{"name":"SYSTEM","sid":"S-1-5-18"},"file":{"normalized_path":"CSIDL_SYSTEM\\svchost.exe","name":"svchost.exe","md5":"4dd18f001ac31d5f48f50f99e4aa1761","modified":"2022-11-05T18:58:44.626Z","path":"c:\\windows\\system32\\svchost.exe","signature_company_name":"Microsoft Windows Publisher","signature_value_ids":[3,5],"sha2":"2b105fb153b1bcd619b95028612b3a93c60b953eef6837d3bb0099e4207aaf6b","original_name":"svchost.exe"}},"enriched_data":{"rule_name":"eGenericProcessLaunch","suspicion_score":0,"category_name":"Process Launch","category_id":2,"rule_description":"Generic process launch event"},"attacks":[{"technique_uid":"T1035","technique_name":"Service Execution","tactic_ids":[2],"tactic_uids":["TA0002"]}],"ref_uid":"9C863643-885C-45E8-A698-2C93FE50DD3F","uuid":"f467edf0-01cd-11ef-d990-0000000207ef","log_name":"epmp_events-fdr-2024-04-24"}
What is Provided
-
Rules to normalize and enrich Symantec Endpoint Detection and Response log messages via field extraction and message enrichment:
| vendor_subtype | vendor_subtype_name |
|---|---|
| 1 | Application Activity |
| 20 | User Session Audit |
| 21 | Entity Audit |
| 238 | Device Control |
| 239 | Device Control |
| 240 | Device Control |
| 502 | Application Control |
| 1000 | System Health |
| 4096 | Reputation Lookup |
| 4098 | Intrusion Prevention |
| 4099 | Suspicious File Detection |
| 4100 | SONAR Detection |
| 4102 | Antivirus Detection (Endpoint) |
| 4109 | Dynamic Adversary Intelligence from Endpoint |
| 4110 | Dynamic Adversary Intelligence from Network |
| 4112 | Deny List (IP/URL/Domain) |
| 4113 | Vantage Detection |
| 4115 | Insight Detection |
| 4116 | Mobile Insight Detection |
| 4117 | Sandboxing Detection |
| 4118 | Deny List (file) |
| 4123 | Endpoint Detection (file) |
| 4124 | Endpoint Detection (IP/URL/Domain) |
| 4125 | Email Detection |
| 4353 | Antivirus Detection (Network) |
| 8000 | Session Event |
| 8001 | Process Event |
| 8002 | Module Event |
| 8003 | File Event |
| 8004 | Directory Event |
| 8005 | Registry Key Event |
| 8006 | Registry Value Event |
| 8007 | Network Event |
| 8009 | Kernel Event |
| 8015 | ETW (Event Tracing for Windows) Event |
| 8016 | Startup Application Configuration Change |
| 8018 | AMSI (AntiMalware Scan Interface) Event |
| 8080 | Session Query Result |
| 8081 | Process Query Result |
| 8082 | Module Query Result |
| 8083 | File Query Result |
| 8084 | Directory Query Result |
| 8085 | Registry Key Query Result |
| 8086 | Registry Value Query Result |
| 8089 | Kernel Object Query Result |
| 8090 | Service Query Result |
| 8099 | Query Command Errors |
| 8103 | File Remediation |
| 8119 | File Remediation Errors |
-
GIM categorization of the following messages:
| Vendor Event ID | GIM Category | GIM Subcategory |
|---|---|---|
| 4096 | detection | detection.default |
| 4098 | detection | detection.default |
| 4099 | detection | detection.default |
| 4100 | detection | detection.default |
| 4102 | detection | detection.default |
| 4109 | detection | detection.default |
| 4110 | detection | detection.default |
| 4112 | detection | detection.default |
| 4113 | detection | detection.default |
| 4115 | detection | detection.default |
| 4116 | detection | detection.default |
| 4117 | detection | detection.default |
| 4118 | detection | detection.default |
| 4123 | detection | detection.default |
| 4124 | detection | detection.default |
| 4125 | detection | detection.default |
| 4353 | detection | detection.default |
Symantec Endpoint Detection and Response Spotlight Content Pack
Symantec Endpoint Detection and Response Spotlight Content Pack offers a dashboard with two tabs: Overview and MITRE ATT&CK Overview.
-
Overview tab
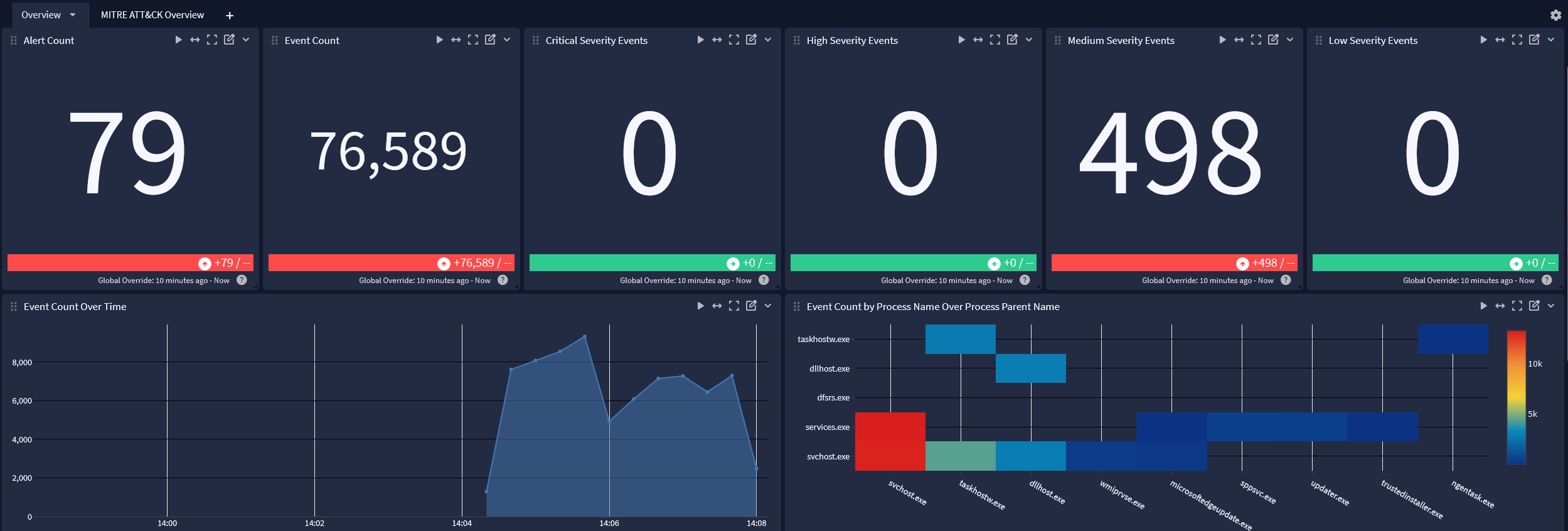
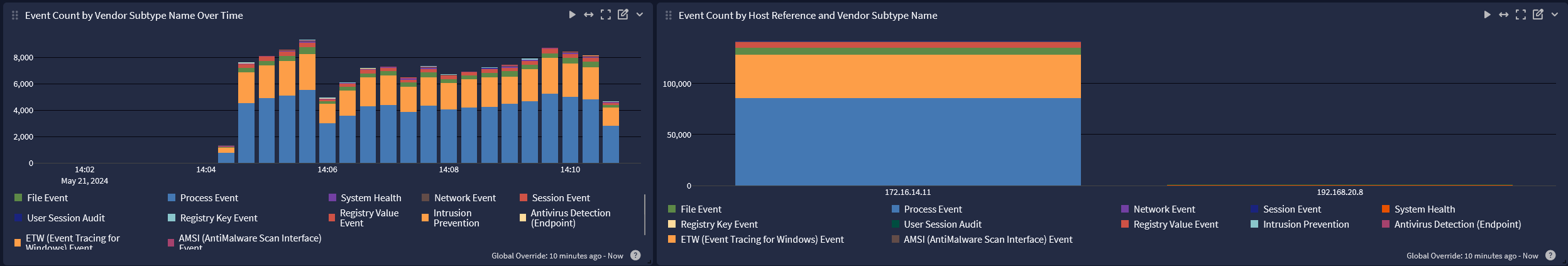
-
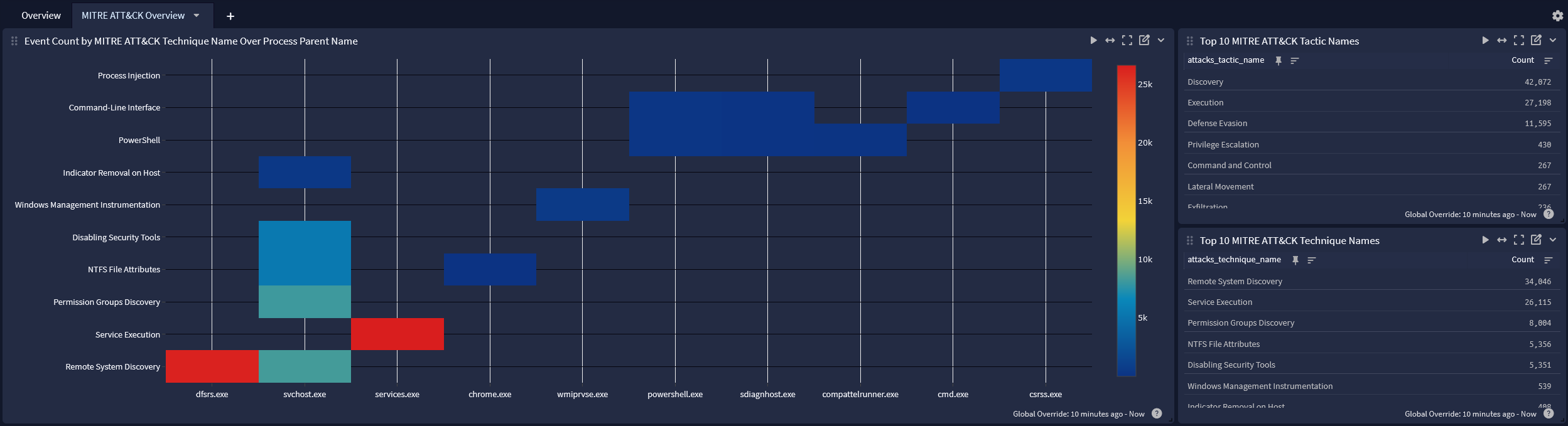
MITRE ATT&CK Overview tab