Symantec Endpoint Protection is a security software suite that consists of anti-malware, intrusion prevention, and firewall features for server and desktop computers. This technology pack will process Symantec logs, providing normalization and enrichment of common events of interest.
Supported Version(s)
-
14.3.8268.5000
Requirements
-
Configure a TCP Syslog input on Graylog.
-
Configure Symantec Endpoint Protection Manager to transmit Syslog to your Graylog server Syslog input.
-
For SEPM output configuration, please refer to the official documentation.
Stream Configuration
This technology pack includes 1 stream:
- "Illuminate: Symantec Device Messages"
Index Set Configuration
This technology pack includes 1 index set definition:
- "Symantec Event Log Messages"
Event Types Supported
-
Server Administration
-
Application and Device Control
-
Server Client-Server Policy
-
Server System
-
Client Packet
-
Client Proactive Threat
-
Client Risk
-
Client Scan
-
Client Security
-
Client System
-
Client Traffic
Log Format Examples
Server Administration Admin
`WIN-TFB8L7BI77H SymantecServer: Site: My Site,Server Name: WIN-TFB8L7BI77H,Domain Name: Default,Admin: admin,Event Description: Administrator log on succeeded`
Application and Device Control
-Behavior
`WIN-TFB8L7BI77H SymantecServer: WIN-TFB8L7BI77H,172.16.14.42,Blocked, - Caller SHA256=e6b2c506042ff50415668cb9d0f24c34c2cf080f1023ca9565fdb846ccd39b53 - Target MD5=9a1d9fe9b1223273c314632d04008384 - Target Arguments='',Create Process,Begin: 2023-01-11 18:38:09,End Time: 2023-01-11 18:38:09,Rule: Rule 1 | Block anydesk.exe,10060,C:/Windows/explorer.exe,0,No Module Name,C:/Users/Administrator/Downloads/AnyDesk.exe,User Name: Administrator,Domain Name: WIN-TFB8L7BI77H,Action Type: ,File size (bytes): 399808,Device ID: SCSI\Disk&Ven_&Prod_ST500DM002-1BD14\4&37da426a&0&000000`
-Agent
`WIN-TFB8L7BI77H SymantecServer: Site: My Site,Server Name: WIN-TFB8L7BI77H,Domain Name: Default,The management server received the client log successfully,WIN-TFB8L7BI77H,Administrator,LocalComputer`
Server Client-Server Policy
`WIN-TFB8L7BI77H SymantecServer: Site: My Site,Server Name: WIN-TFB8L7BI77H,Domain Name: Default,Admin: admin,Event Description: Policy has been edited: Edited shared Firewall policy: Firewall policy,Firewall policy`
Server System
`WIN-TFB8L7BI77H SymantecServer: Site: My Site,Server Name: WIN-TFB8L7BI77H,Event Description: Failed to connect to the syslog server. External logging cannot proceed until the problem is resolved.`
Client Packet
`WIN-TFB8L7BI77H SymantecServer: WIN-Client,Local Host IP: 172.16.14.42,Local: 3,Remote Host IP: 172.16.14.10,Remote Host Name: ceredox-dc01.ceredox.comd,Remote: 3,Outbound,Application: ,Action: Blocked`
Client Proactive Threat
`WIN-TFB8L7BI77H SymantecServer: Security risk found,Computer name: WIN-Client,IP Address: 172.16.14.42,Detection type: Suspicious Behavior Detection,First Seen: Reputation was not used in this detection.,Application name: Microsoft® Windows® Operating System,Application type: Trojan Worm,Application version: 10.0.17763.1,Hash type: SHA-256,Application hash: 85dd6f8edf142f53746a51d11dcba853104bb0207cdf2d6c3529917c3c0fc8df,Company name: Microsoft Corporation,File size (bytes): 1652736,Sensitivity: 1,Detection score: 0,COH Engine Version: ,Detection Submissions No,Allowed application reason: Not on the allow list,Disposition: Good,Download site: ,Web domain: ,Downloaded by: ,Prevalence: Reputation was not used in this detection.,Confidence: Reputation was not used in this detection.,URL Tracking Status: Off,Risk Level: High,Risk type: BPE,Source: SONAR Scan,Risk name: SONAR.SuspPE!gen43,Occurrences: 1,c:\windows\system32\certutil.exe,,Actual action: Access denied,Requested action: Left alone,Secondary action: Left alone,Event time: 2023-01-11 01:29:36,Event Insert Time: 2023-01-11 01:31:24,End Time: 2023-01-11 01:29:36,Domain Name: Default,Group Name: My Company\\Test,Server Name: WIN-TFB8L7BI77H,User Name: Administrator,Source Computer Name: ,Source Computer IP: ,Location: ,Intensive Protection Level: 0,Certificate issuer: Microsoft Windows,Certificate signer: Microsoft Windows Production PCA 2011,Certificate thumbprint: AE9C1AE54763822EEC42474983D8B635116C8452,Signing timestamp: 1536994988,Certificate serial number: 33000001C422B2F79B793DACB20000000001C4`
Client Risk
`WIN-TFB8L7BI77H SymantecServer: Virus found,IP Address: 172.16.14.42,Computer name: WIN-Client,Source: Auto-Protect scan,Risk name: EICAR Test String,Occurrences: 1,File path: C:\Users\Administrator\Downloads\eicar_com.zip,Description: ,Actual action: Cleaned by deletion,Requested action: Cleaned,Secondary action: Quarantined,Event time: 2023-01-12 12:25:36,Event Insert Time: 2023-01-12 12:27:05,End Time: 2023-01-12 12:25:36,Last update time: 2023-01-12 12:27:05,Domain Name: Default,Group Name: My Company\Test,Server Name: WIN-TFB8L7BI77H,User Name: Administrator,Source Computer Name: ,Source Computer IP: ,Disposition: Bad,Download site: [https://secure.eicar.org/eicar_com.zip,Web](https://secure.eicar.org/eicar_com.zip,Web) domain: [secure.eicar.org](http://secure.eicar.org/),Downloaded by: chrome.exe,Prevalence: This file has been seen by hundreds of thousands of Symantec users.,Confidence: This file is untrustworthy.,URL Tracking Status: On,First Seen: Symantec has known about this file for more than 1 year.,Sensitivity: ,Allowed application reason: Not on the allow list,Application hash: 2546DCFFC5AD854D4DDC64FBF056871CD5A00F2471CB7A5BFD4AC23B6E9EEDAD,Hash type: SHA2,Company name: ,Application name: eicar_com.zip,Application version: ,Application type: 127,File size (bytes): 184,Category set: Malware,Category type: Virus,Location: Default,Intensive Protection Level: 0,Certificate issuer: ,Certificate signer: ,Certificate thumbprint: ,Signing timestamp: 0,Certificate serial number:`
Client Scan
`WIN-TFB8L7BI77H SymantecServer: Scan ID: 1673417071,Begin: 2023-01-12 11:25:12,End Time: 2023-01-12 11:25:50,Completed,Duration (seconds): 38,User1: SYSTEM,User2: SYSTEM,Scan started on selected drives and folders and all extensions.,Scan Complete: Risks: 0 Scanned: 1102 Files/Folders/Drives Omitted: 0 Trusted Files Skipped: 748,Command: Not a command scan (),Threats: 0,Infected: 0,Total files: 1102,Omitted: 0,Computer: WIN-TFB8L7BI77H,IP Address: 172.16.14.42,Domain Name: Default,Group Name: My Company\Test,Server Name: WIN-TFB8L7BI77H,Scan Type: DefWatch`
Client Security
`WIN-TFB8L7BI77H SymantecServer: WIN-TFB8L7BI77H,Event Description: [SID: 60501] URL reputation: Browser navigation to known bad URL attack blocked. Traffic has been blocked for this application: C:\Program Files\Google\Chrome\Application\Chrome.exe,Event Type: Browser Protection event,Local Host IP: 0.0.0.0,Local Host MAC: 000000000000,Remote Host Name: ,Remote Host IP: 0.0.0.0,Remote Host MAC: 000000000000,Outbound,OTHERS,,Begin: 2023-01-12 12:21:33,End Time: 2023-01-12 12:21:33,Occurrences: 1,Application: C:/Program Files/Google/Chrome/Application/chrome.exe,Location: Default,User Name: Administrator,Domain Name: WIN-TFB8L7BI77H,Local Port: 0,Remote Port: 0,CIDS Signature ID: 60501,CIDS Signature string: URL reputation: Browser navigation to known bad URL,CIDS Signature SubID: 0,Intrusion URL: http:/[www.eicar.eu/,Intrusion](http://www.eicar.eu/,Intrusion) Payload URL: ,SHA-256: ,MD-5: ,Intensive Protection Level: Level 1,URL Risk: N/A,URL Category: Malicious Sources/Malnets* Client System
WIN-TFB8L7BI77H SymantecServer: WIN-Client,Category: 2,LiveUpdate Manager,Event Description: An update for Revocation Data was successfully installed. The new sequence number is 230112003.,Event time: 2023-01-12 15:29:51,Group Name: My Company\Test`
Client Traffic
`WIN-TFB8L7BI77H SymantecServer: DESKTOP-D2IQ7II,Local Host IP: 172.16.14.58,Local Port: 3,Local Host MAC: F8B156BAD2E9,Remote Host IP: 8.8.8.8,Remote Host Name: dns.google,Remote Port: 3,Remote Host MAC: 001AE3B5F444,ICMP,Outbound,Begin: 2023-01-12 16:59:58,End Time: 2023-01-12 16:59:58,Occurrences: 1,Application: ,Rule: Block all other IP traffic and log,Location: Default,User Name: admin,Domain Name: DESKTOP-D2IQ7II,Action: Blocked,SHA-256: ,MD-5:`
What is Provided
-
Parsing rules to extract Symantec logs into Graylog schema compatible fields
Categorized Events
-
Client Risk: alert message
-
Client Security: alert message
-
Client Proactive Threat: alert message
-
Server Administration (log on event): logon
-
Server Administration (log off event): logoff
-
Server Administration (log on failed): logon
-
Server Administration (admin password change): administrative password reset
alert_severity high.
SEPM supports three action types for the event types: Client Proactive Threat and Client Risk. The behavior is described as:
-
Actual action: The action SEP took to remediate the mentioned threat.
-
Requested action: This is the action SEP wants to perform and is usually the same as actual action.
-
Secondary action: Action to take in case the actual action does not work.
Graylog maps actual, requested, and secondary actions to:
-
Actual action:
vendor_event_action -
Requested action:
vendor_requested_action -
Secondary action:
vendor_secondary_action
The logs are identified by the keyword SymantecServer.
GIM Categorization
GIM categorization is provided for the following messages:
| event_category | gim_event_type_code |
|---|---|
| password_change | 111005 |
| log_out | 102500 |
| log_on | 100000 |
| log_on_failed | 100000 |
| alert_risk_pro_default | 309999 |
| alert_security_default | 309999 |
Symantec Endpoint Spotlight Content Pack
Introduced in Illuminate 3.4 the Symantec Endpoint Spotlight Content Pack comes bundled with the Symantec Endpoint Security Content Pack. See Installing Illuminate or Upgrading Illuminate for more information on Spotlight Content Pack selection. This additional pack contains the following dashboards:
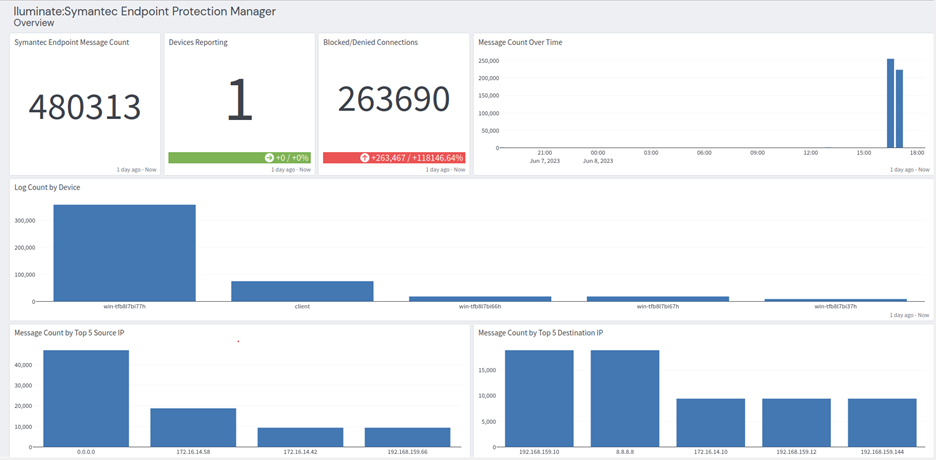
Symantec Endpoint Protection: Overview Tab
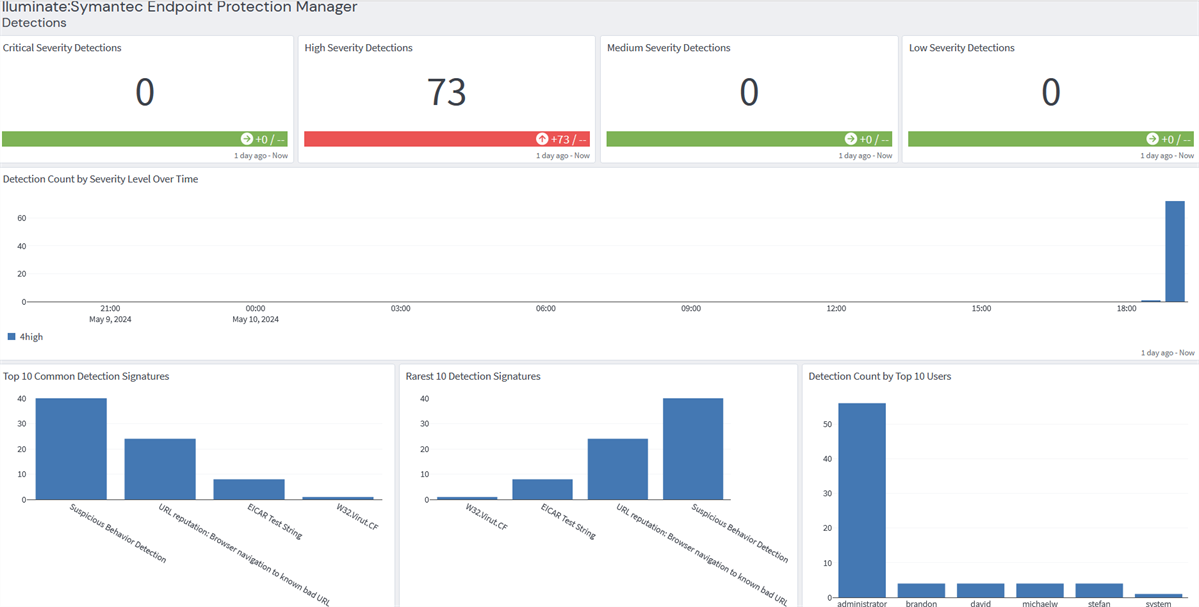
Symantec Endpoint Protection: Detection Tab
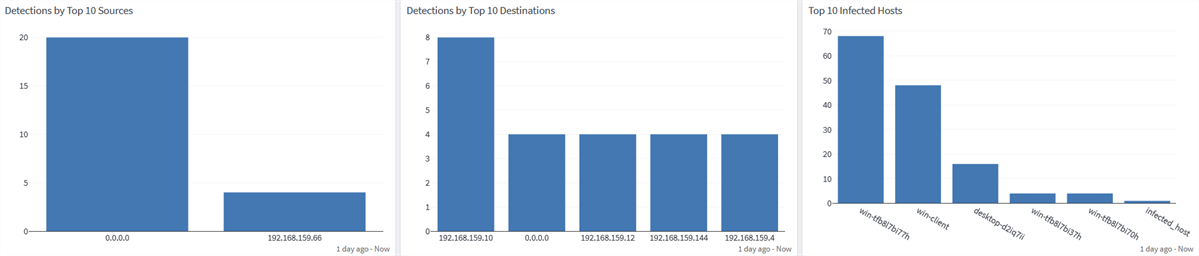
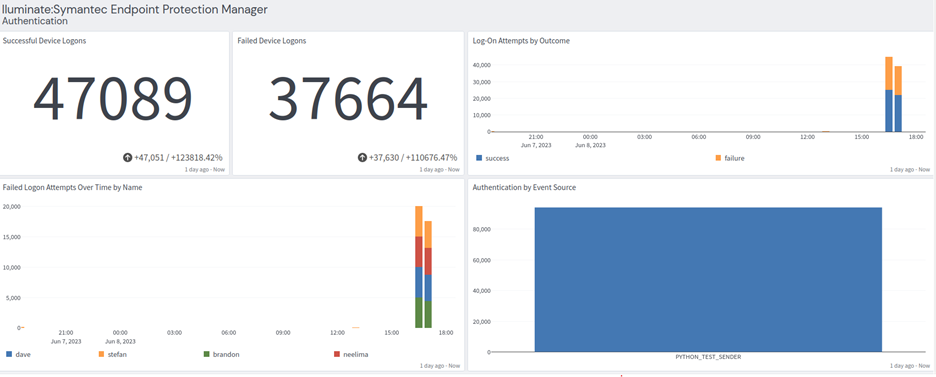
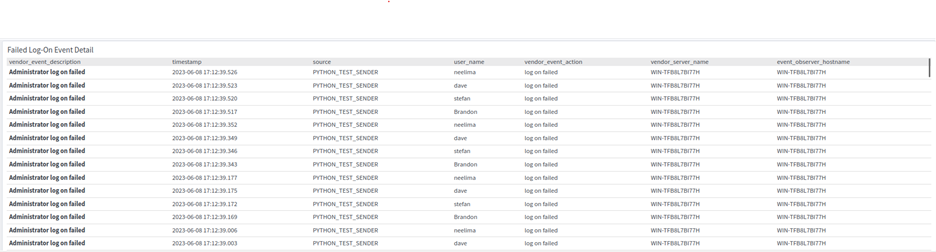
Symantec Endpoint Protection: Authentication Tab