TLS-Secured Data Node Migration
This article will guide you through an in-place migration of your existing OpenSearch cluster secured with TLS to a Graylog Data Node cluster secured with TLS. If you are migrating to Data Node from an unsecured OpenSearch cluster, see Data Node Migration.
Prerequisites
Before proceeding, ensure that the following prerequisites are met:
- Your OpenSearch cluster must be running version 2.19 at the latest. OpenSearch 3.0 or later is not supported for this migration.
Conditions
Note that for this migration method, the following conditions must be true:
-
Your Data Node installation will be on the same hosts as existing OpenSearch nodes.
-
You have deployed Graylog directly on a physical host, not within containers or on virtual hosts, using the same parameters outlined in the installation documentation.
-
Your system has the ability to download and install the Graylog Data Node package from the remote repository.
-
You must have a "healthy" OpenSearch cluster (including one or more nodes) that are configured to use TLS via the OpenSearch Security Plugin. In this instance, "healthy" is defined as the ability to curl the OpenSearch API without using the
-kflag and return the proper output. For example: -
You have available (or can reproduce) the exact
securityadmin.shcommand and arguments used to initially secure the OpenSearch cluster.
Prepare Data Node Configuration File
To begin the migration process, prepare the Graylog Data Node configuration file by installing the service and updating key settings to align with your existing OpenSearch and MongoDB environments.
-
First install the Data Node service. The supported process for installation is described in the individual installation guides depending on your operating system and whether or not you will be running a single- or multi-node Data Node cluster. For example, the instructions for installing Data Node on Ubuntu 20.04 or 22.04 as a single-node installation may be found here. For a list of all available guides, see Install Graylog.
-
During installation, you will be prompted to modify the Data Node configuration file at /etc/graylog/datanode/datanode.conf. Ensure that the following key configuration properties are set as indicated:
-
Set the password_secret to the same value as the password_secret you set in Graylog’s server.conf.
-
Set the opensearch_data_location to the path.data value set in opensearch.yml.
-
Change the mongodb_uri to URL to connect to any existing MongoDB instance.
-
Leave the opensearch_http_port set to 9200 and opensearch_transport_port set to 9300. There should not be a port conflict with existing OpenSearch nodes as, at the first start of the Data Node service, Graylog can detect that new embedded OpenSearch is not configured yet, so only the Data Node API will be started on port 8999. It will not start the new embedded OpenSearch nodes until the migration wizard reaches a certain point.
-
-
As indicated in the installation guides, ensure you enable Data Node and start the service. For example:
Copysudo systemctl daemon-reload
sudo systemctl enable graylog-datanode.service
sudo systemctl start graylog-datanode
Migrate to Data Node
Now, to begin the migration, log in to the Graylog web interface and complete the following steps:
-
Navigate to System > Data Nodes > Data Node Migration.
-
Wait for all Data Nodes to be discovered. They should be listed with a status of UNCONFIGURED.
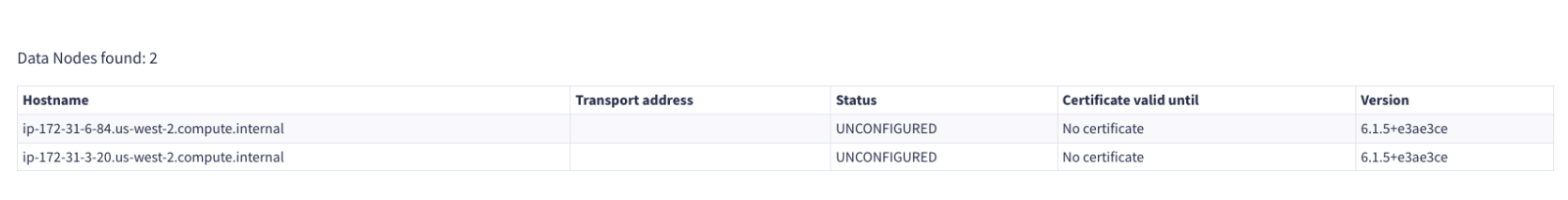
-
Click Next when all nodes are discovered.
-
Create a new CA when prompted by the interface.
-
Configure the renewal policy according to your preferences.
-
You should now be on the Migration Steps page. Carefully read the important information in the interface before proceeding.
Configure JWT Authentication
In order to prepare the indices from the existing OpenSearch cluster for migration, you must configure JWT (Java Web Token) authentication to give Data Node the proper authorization to import this data.
-
Create a base64-encoded version of your Graylog password_secret for use in setting up the JWT token:
Copyecho -n $(grep password_secret /etc/graylog/datanode/datanode.conf | cut -d' ' -f3) | base64 -w0 && echo -
Copy the JWT config below. Replace the value in signing_key with the base64-encoded string you just generated.
Copydescription: "Authenticate via Json Web Token"
http_enabled: true
transport_enabled: true
order: 1
http_authenticator:
type: jwt
challenge: false
config:
signing_key: "base64 encoded HMAC key or public RSA/ECDSA pem key"
jwt_header: "Authorization"
jwt_url_parameter: null
roles_key: "os_roles"
subject_key: null
authentication_backend:
type: noop -
Copy the updated configuration block into $OPENSEARCH_CONFIG/opensearch-security/config.yml under the existing jwt_auth_domain configuration block.
Hint: Copy the entire lines, including leading whitespaces. When pasting, place your cursor at the start of a new line to preserve correct indentation. -
You must either disable the existing jwt_auth_domain configuration or replace it completely.
-
Run the securityadmin.sh command with the same arguments you used when initially setting up OpenSearch Security Plugin.
-
To verify the JWT token has been applied successfully, copy and paste the contents of thisjwt.sh script into a local jwt.sh file.
-
Then, run the following command:
Copycurl -k -H "Authorization: Bearer $($(echo $SHELL) ./jwt.sh \
$(grep password_secret /etc/graylog/datanode/datanode.conf | cut -d' ' -f3))" \
https://localhost:9200 -
If successful, it will return the default output of the OpenSearch API root (
/) endpoint, as shown below:Copy{
"name" : "opensearch01.lab",
"cluster_name" : "graylog",
"cluster_uuid" : "7fHMidh5R36pTKE48a94Jw",
"version" : {
"distribution" : "opensearch",
"number" : "2.15.0",
"build_type" : "deb",
"build_hash" : "61dbcd0795c9bfe9b81e5762175414bc38bbcadf",
"build_date" : "2024-06-20T03:27:12.329408119Z",
"build_snapshot" : false,
"lucene_version" : "9.10.0",
"minimum_wire_compatibility_version" : "7.10.0",
"minimum_index_compatibility_version" : "7.0.0"
},
"tagline" : "The OpenSearch Project: https://opensearch.org/"
}
Directory Compatibility Check
Verify your directory compatibility with the new Data Node directory.
-
Return to the Data Node Migration page in Graylog.
-
Pause message processing on all Graylog nodes by navigating to Cluster Configuration and selecting Pause message processing from the More actions menu.
-
Stop the legacy OpenSearch service on your OpenSearch node:
Copysystemctl disable --now opensearch.service -
Change ownership on the OpenSearch data path:
Copychown -R graylog-datanode:graylog-datanode /var/lib/opensearch/ -
Navigate again to the Data Node Migration page and select Directory Compatibility Check.
Provision Data Nodes with Certificates
To provision Data Nodes with certificates:
-
Start by expanding each Data Node in the Graylog interface by selecting the node to see per-index information and compatibility.
-
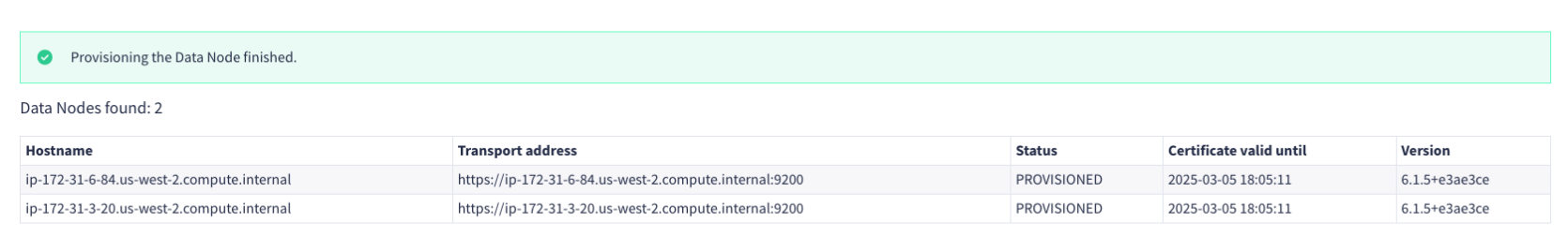
Click the Provision Data Nodes with certificates button.
You should see the following success message. Note that the Status field says Provisioned.
Journal Downtime Warning
Continuing in the Graylog migration interface, review and acknowledge the warning about message processing downtime and Graylog journal size. This information is essential for planning downtime and minimizing the risk of data loss.
Stop Message Processing
Confirm that message processing and all OpenSearch nodes are stopped.
-
Click Next to continue.
Update server.conf and Restart Graylog
-
Wait for all nodes to have a status of Available.
Hint: This process may take several minutes. During this time, you might see log entries in datanode.log that appear unusual, or the Data Nodes list in the interface may show nodes temporarily dropping. This behavior is normal. Investigate further if the logs show continuous Java stack trace errors in the logs or the Data Nodes list shows no discovered nodes for more than 60 seconds. -
Navigate to the Graylog configuration file on each Graylog node and comment out the elasticsearch_hosts property.
-
Restart the Graylog service:
Copysudo systemctl restart graylog-server.service -
Navigate back to theData Nodes page in the Graylog interface and verify that the nodes are green, indicating that the nodes are available.
The migration is now complete!
Verify Migration Success
Verify that your Data Node migration has completed successfully:
-
Open the Graylog Search page and confirm you see the expected results, including data from before the migration.
-
If you see this error message: OpenSearch exception [type=index_not_found_exception, reason=no such index []], then navigate to System > Indices and select Maintenance > Cleanup & recalculate all index ranges in the top-right.
-
If there are no errors, navigate to System > Overview and confirm:
-
There are no red notifications (relevant to migration).
-
Your OpenSearch cluster is green.
-
There are no processing or indexing failures.
-
-
Navigate to System > Nodes and verify that all nodes are processing messages and that their journal utilization is decreasing or at pre-migration levels.
-
In System > Indices, verify all existing index sets are still listed, as well as total shards is the same or greater than before. (These may be greater as index sets may have rotated during migration.)
Further Reading
Explore the following additional resources and recommended readings to expand your knowledge on related topics:

