Asset History
Asset History enables tracking of asset changes by creating a dedicated stream and index set to store historical entries. With this functionality, Graylog automatically records change history for asset operations such as create, update, delete, and risk score changes.
Each entry captures the complete state of the asset after an update or immediately before deletion, providing detailed visibility into asset modifications over time. These records include both the action and source of a change and are contained in standard log messages which are searchable using Graylog search tools.
This article defines asset history, describes change operations and sources, and explains custom fields, snapshots, and snapshot configurations.
Prerequisites
Before proceeding, ensure that the following prerequisites are met:
-
You must have a valid Graylog Security license.
-
Assets must be imported and configured in your Graylog instance. See Import and Configure Assets.
How It Works
When asset-related changes occur, such as updates to metadata, risk scores or custom fields, Graylog automatically generates a history entry for that asset. These entries are stored in a dedicated index and routed to the Asset History stream.
In the Graylog interface, you can view these entries by searching in the Asset History stream on the Search page. Each entry includes:
-
What happened (action, field e.g. update, delete, risk_score_change)
-
When it happened (timestamp)
-
How the change was made (source, e.g. manual, snapshot)
-
Which asset was affected (asset_id or asset_name)
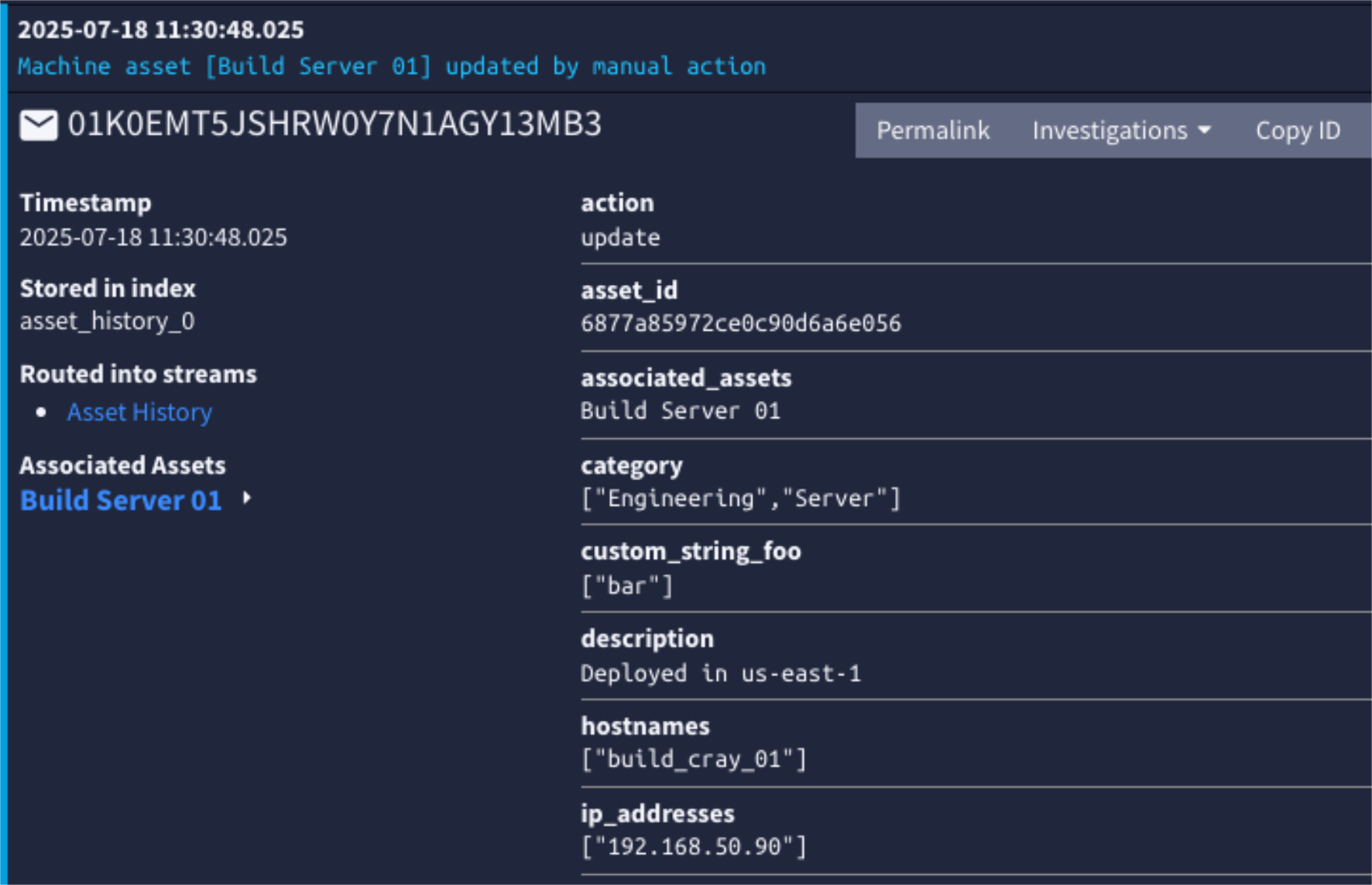
For example, when a user manually updates a machine asset, Graylog logs an entry showing the updated record and context. You can click into the log message to see detailed fields and metadata, investigate changes, or correlate activity with other events.
Sources and Actions
Each asset history entry captures fields for both the action and source of the change. By capturing both the action (what changed) and the source (who or what made the change), asset histories make it easier to trace specific changes over time. These asset history fields help you quickly identify the origin of modifications, audit activity, and filter queries in your search backend to focus only on relevant updates, which improves troubleshooting and security visibility.
Supported Actions
The action field specifies the type of operation performed on an asset, such as create, update, delete, or risk score change. This field is included in every asset history entry and serves as a key indicator for tracking changes over time. By filtering on the action field in your queries, you can isolate specific types of activity such as identifying all assets that were deleted or had risk scores modified, making it easier to audit changes, investigate incidents, and maintain asset oversight.
Below is a list of supported actions:
-
create: An asset was created.
-
update: An asset was updated.
-
delete: An asset was deleted.
-
risk_score_set: The risk score of an asset was set automatically after an event triggered.
-
snapshot: An asset snapshot was taken.
Supported Sources
The source field in an asset’s history indicates where the action originated or how it was initiated. This may include internal systems such as automated processes or user-initiated changes through the Graylog interface. By reviewing the source field, you can better understand the context of each change, distinguish between manual and automated actions, and enhance auditability and accountability across asset activity.
Below is a list of supported sources:
-
manual: Any manual update to an asset through the Graylog user interface or API.
-
snapshot_periodical: The scheduled snapshot task.
-
risk_score_security_event_fired: A security event initiated the update of an asset risk score.
-
risk_score_security_event_closed: A closed security event initiated the update of an asset risk score.
-
asset_source_import_ad: An asset import from Active Directory.
-
asset_source_import_ldap: An asset import from LDAP.
-
asset_source_import_m365: An asset import from Microsoft 365.
-
vulnerability_scan_defender: Vulnerability scan import from Microsoft Defender.
-
vulnerability_scan_nessus: Vulnerability scan import from Nessus.
-
pipeline_add_categories: Categories added from the Add Asset Categories pipeline rule.
-
pipeline_remove_categories: Categories removed from the Remove Asset Categories pipeline rule.
Custom Fields
Custom fields (available on machine assets only) are included in asset histories using the format custom_<field-type>_<field name>. If custom fields are defined for a machine asset, they will appear in that asset's history. For information on how to create custom fields, see Field Types.
These are the three supported custom field types:
-
string: Values are stored as a string array.
-
number: Values are stored as a number array.
-
date: Values are currently stored as a string array.
For example:
"custom_string_tags": [ "app-server", "managed" ],
"custom_number_device_id": [ 105 ],
"custom_date_purchase_date": [ "10-15-2018" ],Snapshots
In addition to recording individual asset changes, Graylog automatically generates daily asset snapshots to support time-based reporting and dashboard visualizations, including tracking changes in risk scores. A snapshot is a point-in-time capture of an asset’s full state, independent of whether any changes occurred. This ensures that you can review consistent historical asset records, even during periods of low or no activity.
By default, Graylog takes snapshots at midnight local time. These entries can be identified by the following fields:
-
action:snapshot
-
source:snapshot_periodical
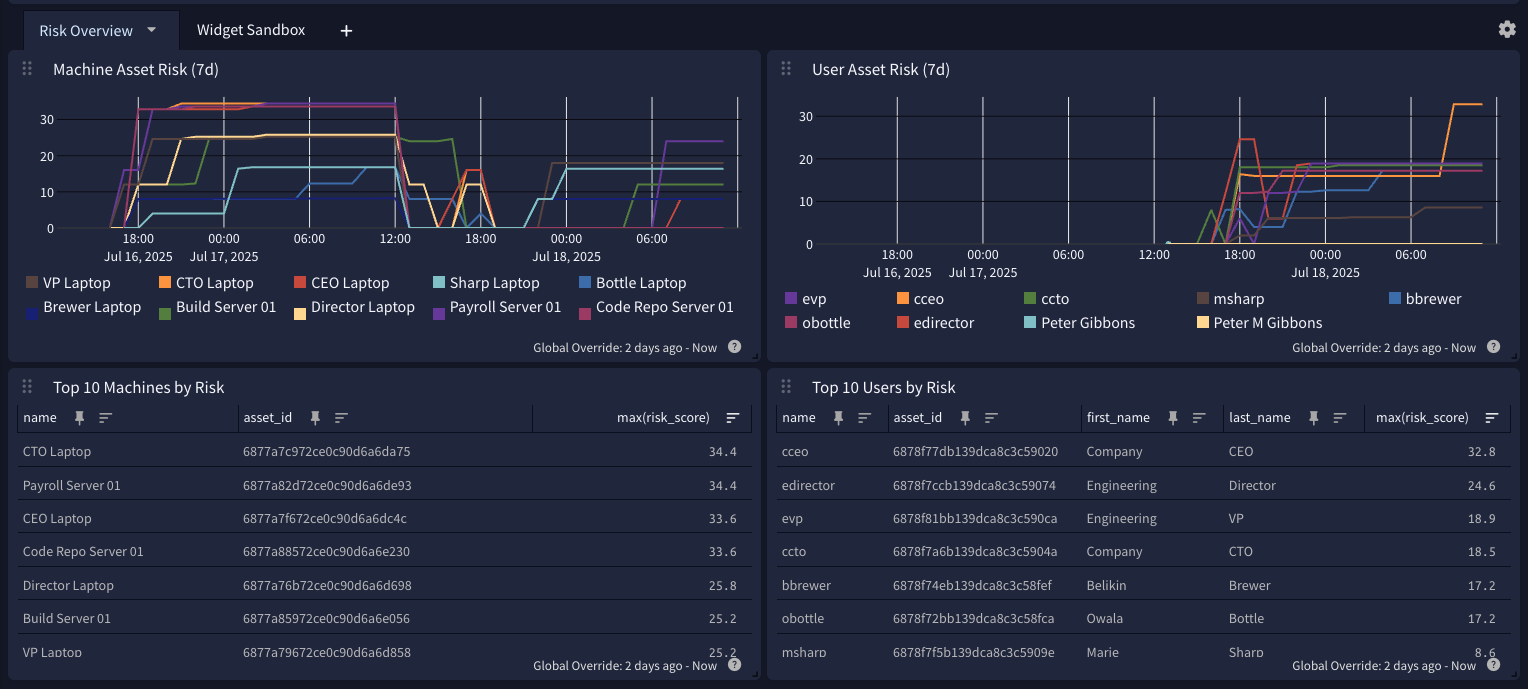
The daily snapshot interval provides a reliable baseline for analyzing asset trends over time. For example, snapshots can be graphed in Graylog dashboards to show how risk scores, ownership, or other asset properties evolve over time. This approach allows you to compare long-term trends alongside event-driven updates, giving a complete picture of asset health and risk progression.
For example, this dashboard, which groups the risk_score field by asset_id, monitors risk trends over time.
Snapshot Configuration
The interval at which the snapshots are taken can be adjusted with the assets_history_snapshot_interval server configuration property. The minimum supported value is one hour (1h). Snapshots can be disabled entirely by setting this interval to 0s.
With the default interval of 24h, snapshots are taken around midnight following the initial server startup. This setting minimizes the possibility of repeated daily snapshots being taken with multiple server reboots. Snapshots are taken shortly after server startup for any other custom interval.
Asset History Examples
Asset histories use a fixed schema, which represents specified asset properties in a flattened field structure. To aid with querying, several summary fields have been added.
Machine Asset Example
The following example shows a machine asset history entry generated from a manual update. It includes standard metadata, asset identifiers, custom fields, and vulnerability data to illustrate the structure and detail available in a machine asset history.
User Asset Example
The following example shows a user asset history entry generated by a scheduled snapshot. It captures identity details, risk score, priority, and other metadata relevant for tracking user asset activity over time.
Further Reading
Explore the following additional resources and recommended readings to expand your knowledge on related topics:

