Graylog Forwarder
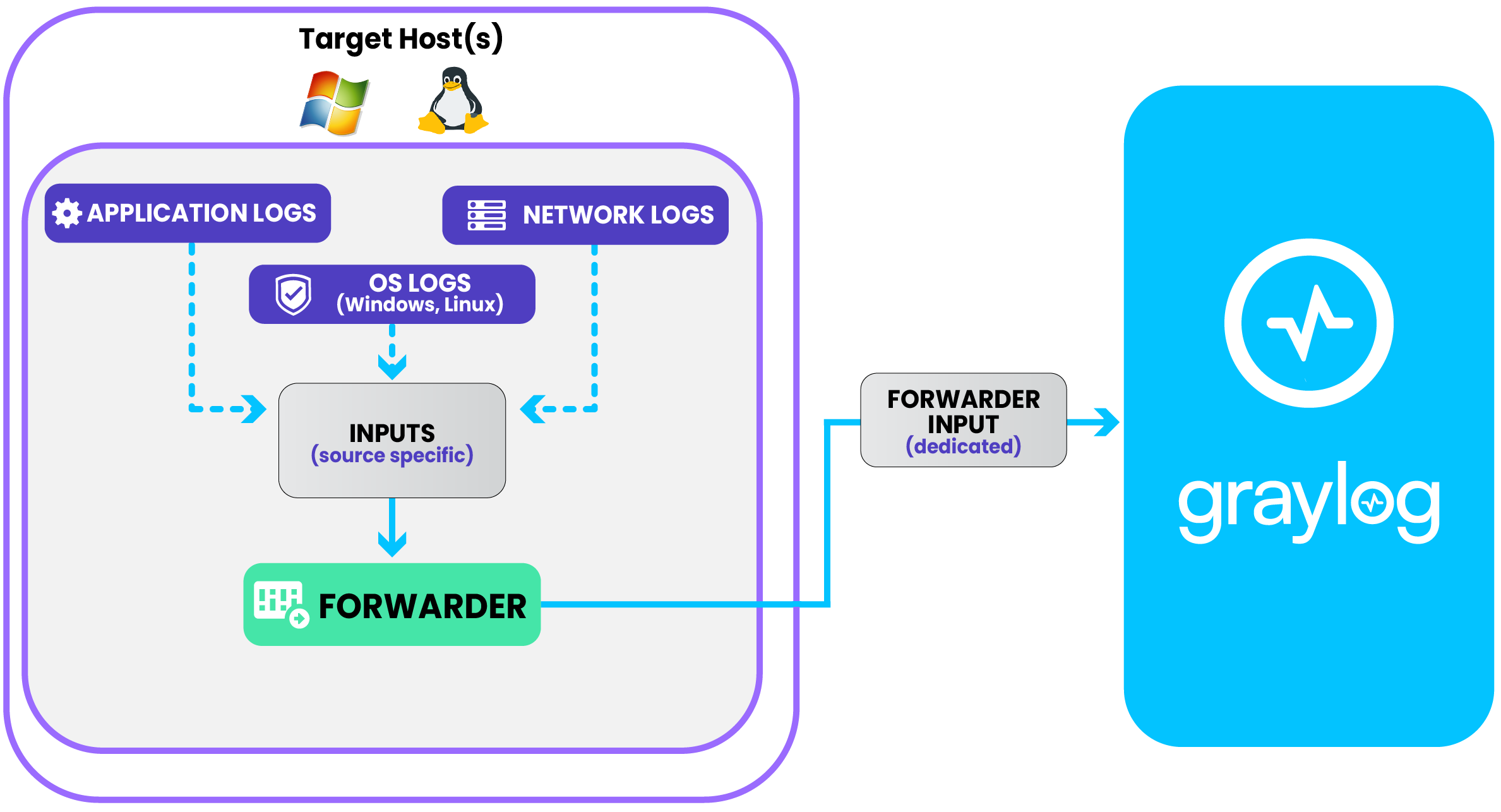
The Graylog Forwarder is a native log shipper designed for secure, efficient log collection in remote sites and distributed environments. It runs on Linux hosts or in containers and acts as a lightweight intermediary that gathers log data through local inputs and sends it to your Graylog cluster over a secure TLS connection. By operating directly on each host, the Forwarder provides a reliable, centralized mechanism for transporting logs from distributed systems back to Graylog.
This article explains how to configure and manage the Forwarder using input profiles in Graylog and how it sends collected logs to the forwarder input in your Graylog cluster. It also provides guidance for both Graylog Cloud and on-premise deployments and describes how the Forwarder fits into your overall Graylog environment.
Forwarder Architecture
Forwarder architecture consists of three core components working together to collect and deliver log data.
Forwarder on Host
At the host level, the Forwarder runs as a service on Linux or inside a container. It uses assigned input profiles to determine which inputs should run on the host, and it supports many of the same input types available on the Graylog server, including Syslog, Beats, and others.
Forwarder Input
Within the Graylog cluster, the Forwarder sends its collected logs to a dedicated Forwarder input. Communication occurs over two ports: port 13301 for transferring log data and port 13302 for receiving configuration updates. This separation ensures reliable delivery while maintaining continuous synchronization with Graylog.
Graylog
Graylog provides the control layer for managing Forwarders. Administrators create tokens, input profiles, and configuration settings directly in Graylog, and the Forwarder regularly retrieves and applies these settings. Each Forwarder host is visible under System > Forwarders, offering centralized oversight and management.
Forwarder Tokens
A Forwarder token authenticates a Forwarder to the Graylog API. It is recommended that each host uses its own token, but this is not required. Tokens group hosts under a single entry in Graylog while keeping each host visible as a separate node. The setup wizard generates tokens. Tokens must be placed in forwarder.conf before the service starts.
Example
You might create a token named web-servers-prod and use it for all Forwarder agents on your production web hosts. Each agent registers with Graylog using that token. In Graylog, you see a single token group for web-servers-prod with each host listed individually under that group.
Input Profiles
Input profiles define which inputs a Forwarder runs on a host. Each profile includes one or more inputs, such as:
These inputs are activated when the Forwarder registers. Profiles also let you group inputs and reuse them across multiple Forwarder hosts. This provides a consistent, manageable way to control which inputs each Forwarder should run.
For more information on input profiles, see Configure Forwarder Input Profiles.
Example
To enable a Forwarder at a remote site to receive Syslog data from network devices and Beats data from Linux hosts, create an input profile named Remote Site A that includes the following inputs:
-
Syslog UDP input on port 5140
-
Beats input on port 5044
Assign the Remote Site A profile to the Forwarder. When the Forwarder connects, it activates the inputs defined in the profile and begins receiving data.
Forwarder vs. Sidecar
The Graylog Forwarder and Graylog Sidecar serve different roles within a Graylog environment. The Forwarder focuses on collecting logs from remote sources and securely transmitting them to your Graylog Server. It uses input profiles to determine which inputs to start, and it sends all gathered log data directly to the Forwarder input configured on the Graylog Server.
The Graylog Sidecar, by contrast, manages external log collectors such as Filebeat, Winlogbeat, or Auditbeat. It is installed directly on each log source and acts as a lightweight control agent. Sidecar regularly retrieves its configuration from Graylog and applies those settings to the underlying log collector, ensuring consistent and centrally managed log collection behavior.
Forwarder in Graylog Cloud vs. Self-Managed Deployments
The Forwarder operates differently in Graylog Cloud compared to self-managed environments. In Graylog Cloud, the Forwarder input is automatically provided, and a setup wizard guides the configuration process from start to finish. TLS is always required in Cloud deployments, but all necessary certificates are preconfigured, removing the need for manual certificate management. Cloud environments also do not expose standard collector input ports, since communication is routed securely through the platform.
In a self-managed (on-premises) deployment, the forwarder input must be created either manually or through the setup wizard. TLS is optional, allowing organizations to choose the security level appropriate for their environment. Port selection and certificate management are handled within the Graylog interface, giving you full control over how the Forwarder communicates with the system.
Versioning
The Forwarder uses a MAJOR.MINOR versioning scheme and is released independently from the Graylog server. We recommend updating the Forwarder regularly to the latest available release. Although older versions are generally supported, the Forwarder’s major version (for example, 7.x) should ideally match the server’s major version. Mismatched major versions may limit access to certain features, such as newly introduced inputs.
In most cases, older Forwarder versions will continue to function with newer Graylog server versions, although only the features available at the time of that Forwarder release can be expected to work. Older versions may become unsupported only in exceptional cases, such as when a version is significantly outdated and no longer maintainable.
Similarly, newer Forwarder versions are designed to remain compatible with older Graylog server versions, ensuring flexibility during upgrade cycles.
Further Reading
Explore the following additional resources and recommended readings to expand your knowledge on related topics:

