Tor Exit Node Data Adapter
The Tor Exit Node data adapter allows for the identification and management of log messages originating from Tor Exit nodes. These nodes, while essential for preserving user privacy on the Tor network, can also be exploited for malicious activities if left unmonitored. By incorporating Tor Exit node information into Graylog, you can enhance visibility into potential threats, proactively flagging and analyzing suspicious activity linked to these exit nodes.
Prerequisites
Before proceeding, ensure that the following prerequisites are met:
-
You need at least Java 8 (u101). The exit node information is hosted on a Tor website that uses Let's Encrypt for SSL and only Java 8 (u101 or newer) supports it.
-
Install the Tor Exit Node List - Threat Intel Plugin content pack, which is already included in the Graylog server installation package as a default plugin. This content pack installs the Tor Exit Node data adapter, cache, and lookup table. Navigate to System > Content Packs. Search for Tor Exit Node List - Threat Intel Plugin in the Filter box. Click on the install button to Install the content pack.
-
Enable the Threat Intelligence Lookup plugin before this data adapter can be used.
-
Navigate to System > Configurations.
-
From the left menu pane select Plugins.
-
SelectThreat Intelligence Lookup and click on Edit configuration.
-
Check the Allow Tor exit node lookups checkbox.
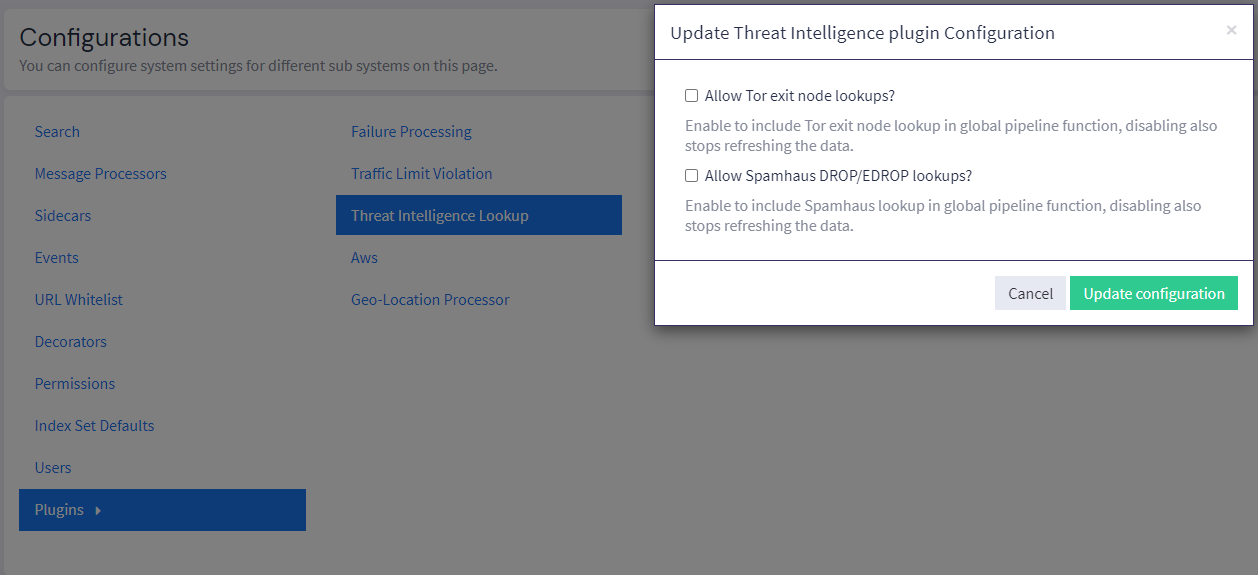
-
Configure the Data Adapter
You can create a data adapter during the lookup table creation workflow, or they can be created separately on the Data Adapters tab. The following configuration options are available for this data adapter:
|
Title |
A short and unique title for this data adapter. |
|
Description |
Data adapter description. |
|
Name |
The name used to refer to this data adapter. This should be something unique and recognizable within your Graylog environment. |
|
Custom Error TTL |
Time-to-live for custom error messages in seconds. |
Example Tor Exit Node Pipeline Rule
This pipeline rule checks if a message’s source IP (src_ip) is a known Tor Exit Node using the tor_exit_node_lookup data adapter. If it is, the rule enriches the message with details about that node, tags it with tor_exit_node: true, and routes it to a dedicated “Tor Exit Node Activity” stream for monitoring.
rule "Check IP for Tor Exit Node"
when
// Check if the src_ip field exists in the message
has_field("src_ip") &&
// Perform a lookup for the IP address in the Tor Exit Node data adapter
lookup_value("tor_exit_node_lookup", to_string($message.src_ip)).single_value == true
then
// Add a field indicating the IP is a Tor Exit Node
set_field("tor_exit_node", true);
// Retrieve additional information about the Tor Exit Node from the lookup result
let lookup_result = lookup("tor_exit_node_lookup", to_string($message.src_ip));
set_field("tor_exit_node_details", lookup_result.multi_value);
// Route the message to a specific stream for Tor-related activity
route_to_stream(name: "Tor Exit Node Activity");
endThese example results show that the source IP matched two known Tor Exit Nodes:
{
"single_value": "64D74AAA74F30DC2CFB36343CE5D4451B9A4DBA8, 522A80ECA8C846F60CEE617F243E3546D5219836",
"multi_value": {
"node_ids": [
"64D74AAA74F30DC2CFB36343CE5D4451B9A4DBA8",
"522A80ECA8C846F60CEE617F243E3546D5219836"
]
},
"string_list_value": null,
"has_error": false,
"ttl": 9223372036854776000
}
The single_value field lists both node IDs as a comma-separated string, while the multi_value section provides them as an array for structured access.
The lookup completed successfully (has_error: false) and the very large ttl value indicates that the result is stored indefinitely or for a very long time.
Further Reading
Explore the following additional resources and recommended readings to expand your knowledge on related topics:

