Spamhaus (E)DROP Data Adapter
The Spamhaus (E)DROP data adapter is used to identify potentially malicious IP addresses and subnets based on the Spamhaus DROP (Don’t Route Or Peer) and EDROP (Extended DROP) lists. These lists are designed to prevent connections to networks known for abusive or malicious behavior, such as spamming, malware distribution, and botnet activity.
Prerequisites
Before proceeding, ensure that the following prerequisites are met:
-
Install the Spamhaus DROP - Threat Intel Plugin content pack, which is already included in the Graylog server installation package as a default plugin. This content pack installs the Spamhaus (E) data adapter, cache and lookup table.
-
Navigate to System > Content Packs.
-
Search for Spamhaus DROP - Threat Intel Plugin in the Filter box.
-
Click on the install button to Install the content pack.
-
-
Enable the Threat Intelligence Lookup plugin.
-
Navigate to System > Configurations.
-
From the left menu pane select Plugins.
-
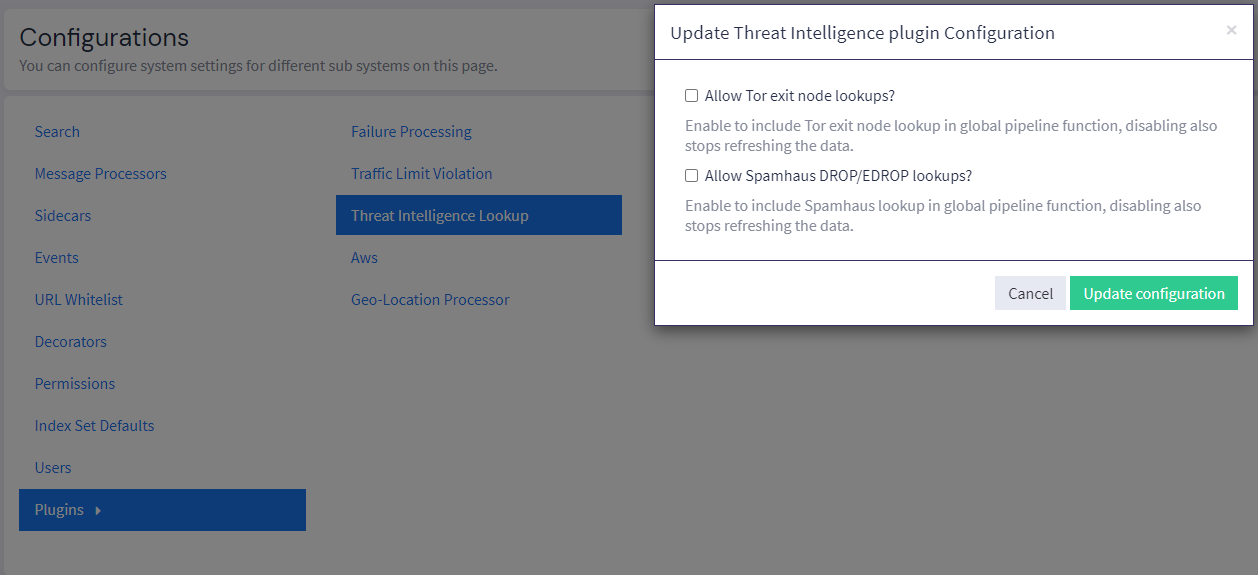
SelectThreat Intelligence Lookup and click on the Edit configuration button.
-
Check the Allow Spamhaus DROP/EDROP lookups checkbox.
-
Configure the Data Adapter
You can create a data adapter during the lookup table creation workflow, or they can be created separately on the Data Adapters tab. The following configuration options are available for this data adapter:
|
Title |
A short and unique title for this data adapter. |
|
Description |
Data adapter description. |
|
Name |
The name used to refer to this data adapter. This should be something unique and recognizable within your Graylog environment. |
|
Custom Error TTL |
Time-to-live for custom error messages in seconds. |
Example Spamhaus (E)DROP Pipeline Rule
This pipeline rule checks if an IP address from incoming logs is listed in the Spamhaus database:
rule "Check IP in Spamhaus EDROP"
when
// Check if the IP field is present in the message
has_field("src_ip") &&
// Perform a lookup in the Spamhaus EDROP adapter
lookup_value("spamhaus_edrop", to_string($message.src_ip)).single_value == true
then
// Add a tag to indicate the IP is flagged
set_field("spamhaus_flag", true);
// Add additional information about the match from the lookup
let lookup_result = lookup("spamhaus_edrop", to_string($message.src_ip));
set_field("spamhaus_sbl_id", lookup_result.multi_value.sbl_id);
set_field("spamhaus_subnet", lookup_result.multi_value.subnet);
// Route the message to a specific stream for flagged traffic
route_to_stream(name: "Flagged IPs Stream");
end
Further Reading
Explore the following additional resources and recommended readings to expand your knowledge on related topics:

