Snort is an open source network intrusion detection (IDS) and intrusion prevention system (IPS). This IDS/IPS system performs real-time traffic analysis and packet logging on Internet Protocol (IP) networks. It also can be used to detect semantic URL attacks, server message block probes, OS fingerprinting attempts, stealth port scans and buffer overflows.
Snort can be configured in three different modes: packet-capture mode, logging mode or IDS mode. This pack runs Snort in IDS mode and comes with predefined rules. Snort will apply the packet content coming over any network it is monitoring to each rule.
Sample Snort Rule
alert icmp any any -> any any (msg:"ICMP flood"; sid:1000001; rev:1; classtype:icmp-event; detection_filter:track by_dst, count 500, seconds 3;)
Supported Versions
Snort can run on Ubuntu and RedHat based Linux versions, FreeBSD, and Fedora.
Stream Configuration
This technology pack includes one stream:
-
"Illuminate: Snort IDS Messages"
Index Set Configuration
This technology pack includes one index set definition:
-
“Snort IDS Logs”
The default configuration file is /etc/snort/snort.com.
Please refer to Snort’s official website for an installation and configuration guide.
Requirements
In order to use this technology pack, Snort 3 should be configured to log in JSON format. Logging configurations such as alert_fast can be used but a JSON configuration is required to capture detailed event information.
The snort.lua file below can be used for both Snort alerts and AppID alerts. If AppID is not used, those settings can be ignored.
The recommended paths and file names are listed below. If these differ from an existing configuration, the paths and file names will need to be adjusted in the Filebeat configuration.
-
Snort:
/var/log/snort/alert_json.txt -
AppID:
/var/log/snort/appid-output.json
Additional information regarding AppID, installation, and usage can be found on the Snort documentation page. An example guide for installing and configuring AppID on Linux distributions can be found under the section Snort Setup Guides.
Snort 3 Configuration
snort.lua
alert_json =
{
fields = 'timestamp seconds action class b64_data dir dst_addr dst_port eth_dst eth_len eth_src eth_type gid icmp_code icmp_id icmp_seq icmp_type iface ip_id ip_len msg pkt_gen pkt_len pkt_num priority proto rev rule service sid src_addr src_ap src_port target tcp_ack tcp_flags tcp_len tcp_seq tcp_win tos ttl udp_len vlan b64_data client_bytes client_pkts flowstart_time server_bytes server_pkts',
file = true,
limit = 100,
}appid_listener =
{
json_logging = true,
file = "/var/log/snort/appid-output.json",
}Because Snort is configured to log in JSON format, a delivery system that can parse each field and deliver them to Graylog is required. This technology pack supports log delivery via Filebeat with a specific configuration of inputs and outputs, identifying logs for parsing and delivery to Graylog for Illuminate processing.
The paths and fields sections are required for this configuration. If the Snort logs are being stored in paths other than those in the following .yml file, these paths must be updated. The event_source_product: snort field is critical for proper identification and parsing of logs.
Filebeat Configuration
Additional information regarding the installation and configuration of Filebeat can be found below:
The following is the default configuration file which can be edited to configure Filebeat.
filebeat.yml
- type: filestream
id: snort-filestream
enabled: true
paths:
- /var/log/snort/alert_json.txt
- /var/log/snort/appid-output.json
parsers:
- ndjson:
target: "snort3"
add_error_key: true
overwrite_keys: true
fields:
event_source_product: snort3
fields_under_root: trueYou can find instructions for sending other syslog daemons into Graylog in this document.
Log Format Example
{ "timestamp" : "04/04-10:36:13.537364", "seconds" : 1680618973, "action" : "allow", "class" : "Attempted User Privilege Gain", "b64_data" : "DHWBgAABAAQAAAAAB3NvbngtZnALbWVkaWFzZWFyY2gHdmVyaXpvbgNjb20AAAEAAcAMAAUAAQAAAEQATDFhYjI2Y2NhMTI0Y2JhNGY1ZDg5Y2MwYzUwOWQ5MjY2NC01Y2U1NzM2MTU5NzEyOTc4A2VsYgl1cy1lYXN0LTEJYW1hem9uYXdzwCjAPQABAAEAAAA5AAQjrk20wD0AAQABAAAAOQAEIsacQcA9AAEAAQAAADkABDRHiMQ=", "dir" : "S2C", "dst_addr" : "192.168.1.1", "dst_port" : 44661, "eth_dst" : "B1:F1:51:71:31:31", "eth_len" : 227, "eth_src" : "81:B1:91:F1:01:01", "eth_type" : "0x800", "gid" : 1, "iface" : "ens34", "ip_id" : 24269, "ip_len" : 193, "msg" : "PROTOCOL-DNS Microsoft Threat Management Gateway heap buffer overflow attempt", "pkt_gen" : "raw", "pkt_len" : 213, "pkt_num" : 22551641, "priority" : 1, "proto" : "UDP", "rev" : 1, "rule" : "1:57878:1", "service" : "unknown", "sid" : 57878, "src_addr" : "192.168.1.2", "src_ap" : "192.168.1.2:53", "src_port" : 53, "tos" : 0, "ttl" : 61, "udp_len" : 193, "vlan" : 0, "b64_data" : "ABCLDKDDHDVBAERY3345112442JhNGY1ZDg5Y2MwYzUwOWQ5MjY2NC01Y2U1NzM2MTU5NzEyOTc4A2VsYgl1cy1lYXN0LTEJYW1hem9uYXdzwCjAPQABAAEAAAA5AAQjrk20wD0AAQABAAAAOQAEIsacQcA9AAEAAQAAADkABDRHiMQ=", "client_bytes" : 91, "client_pkts" : 1, "flowstart_time" : 1680618973, "server_bytes" : 227, "server_pkts" : 1 }
What is Provided
Rules to normalize and enrich Snort 3 log messages.
Snort 3 Log Message Processing
The Illuminate processing of Snort 3 log messages provides the following:
-
Field extraction, normalization, and message enrichment for Snort 3 log messages (IDS and AppID).
-
GIM Categorization of the following messages:
| Snort 3 Log Type | GIM Category | GIM Subcategory |
|---|---|---|
| ids | alert | alert.default |
| appid | network | network.default |
Use Cases
Snort is used to monitor networks for malicious packets and threats. Functioning as either an IDS or IPS, Snort can analyze and compare traffic against thousands of signatures and application detectors to provide a high-level overview of a network.
Examples of what can be monitored using this content pack: Unauthorized hosts or users, misconfigured devices (DNS, hostname, etc.), devices beaconing to malicious IPs, brute force attacks or policy violations.
Snort Spotlight Content Pack
The Snort Spotlight content pack contains:
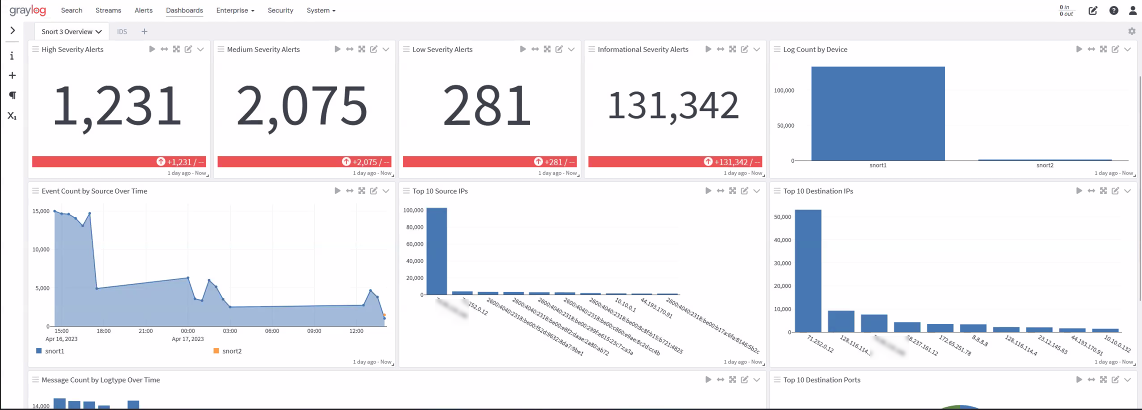
Snort 3 Overview
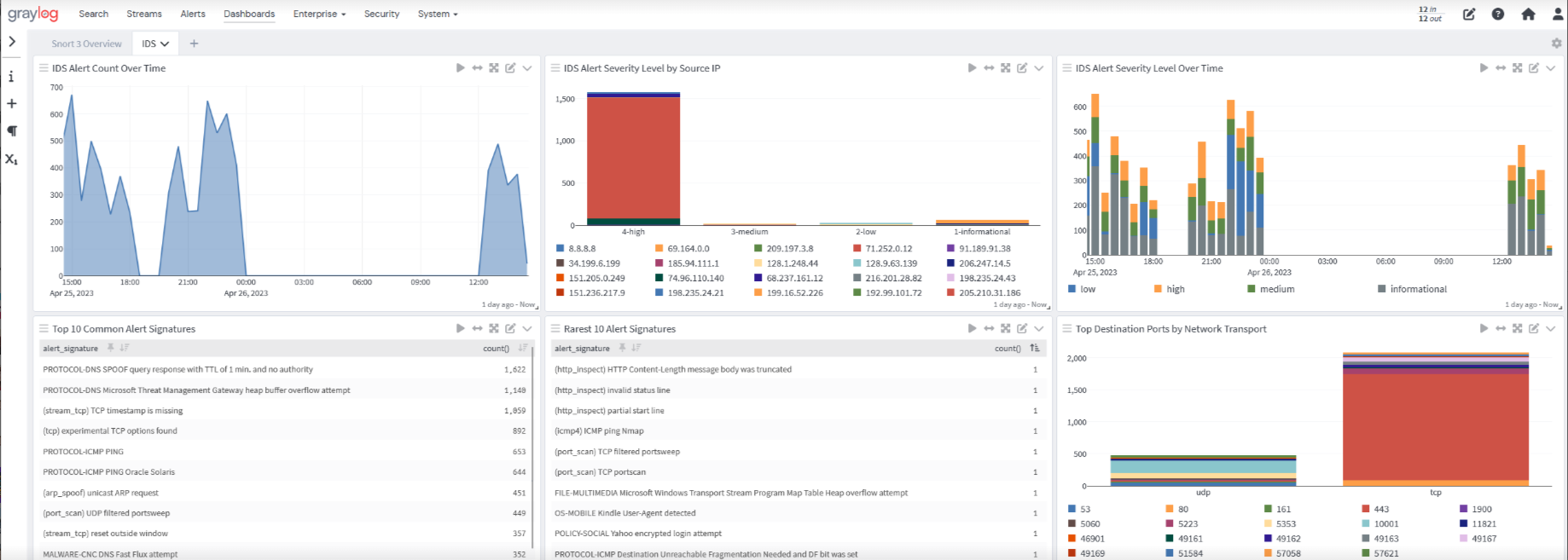
Snort IDS Overview
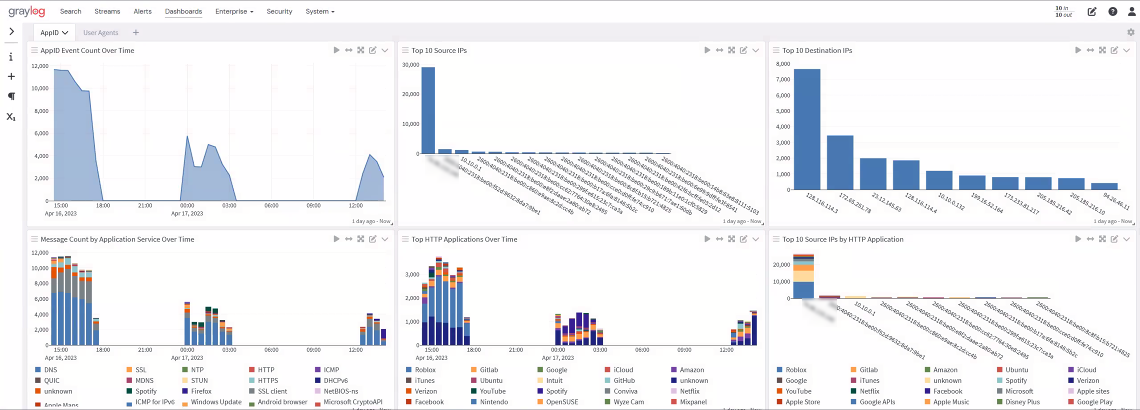
Snort App ID Overview