Amazon Security Lake is a purpose-built data lake that centralizes security data from AWS environments, SaaS providers, on-premises, and cloud sources. It converts incoming security data logs to the Open Cybersecurity Schema Framework (OCSF) open standard.
Supported Version(s)
-
Tested with AWS Security Lake in January 2024. Requires at least Graylog 5.1.10 or 5.2.3.
Stream Configuration
This technology pack includes one stream:
-
"Illuminate:AWS Security Lake Messages"
Index Set Configuration
This technology pack includes one index set definition:
-
"AWS Security Lake Logs"
Supported Log Types
The content pack parses out supported objects. Regardless of the source, if the data is present in the objects listed below, the pack will parse them out. Currently, we support these objects:
actor,anwers,api,attack,cloud,compliance,connection_info,cve,device,dns_answer,dns_query,email,endpoint,file,finding,http_request,http_response,identity,malware,metadata,process,resources,network_proxy,proxy,query,user,dst_endpoint,traffic,src_endpoint.
Log Format Example
Route53 logs
{"metadata":{"product":{"version":"1.100000","name":"Route 53","feature":{"name":"Resolver Query Logs"},"vendor_name":"AWS"},"version":"0.26.1"},"cloud":{"account_uid":"67654654","region":"ap-northeast-1","provider":"AWS"},"src_endpoint":{"vpc_uid":"vpc-02c62c77516baa087","ip":"172.31.12.120","port":37554,"instance_uid":"i-018c0e79fa98b93f3"},"time":"1676953179000","query":{"hostname":"motd.ubuntu.com.","type":"A","class":"IN"},"rcode":"NOERROR","answers":[{"type":"A","rdata":"34.243.160.129","class":"IN"},{"type":"A","rdata":"54.217.10.153","class":"IN"},{"type":"A","rdata":"34.254.182.186","class":"IN"},{"type":"A","rdata":"54.171.230.55","class":"IN"},{"type":"A","rdata":"54.247.62.1","class":"IN"}],"connection_info":{"protocol_name":"UDP","direction":"Lateral","direction_id":3},"dst_endpoint":{"instance_uid":"None","interface_uid":"None"},"severity_id":"-1","severity":"Other","class_name":"DNS Activity","class_uid":"4003","category_name":"Network Activity","category_uid":"4","rcode_id":"0","activity_id":"1","activity_name":"Resolved","type_name":"DNS Activity: Resolved","type_uid":"400301","unmapped":"None"}
Requirements
-
This content pack works together with a configured AWS Security Lake input and Graylog 5.2 or higher.
Configure AWS Security Lake Input
For configuration please consult the following documentation.
What is Provided
-
Parsing rules to extract AWS Security Lake logs into Graylog schema-compatible fields.
-
Categorization of the Security Findings, Account Change, Authentication, Network and DNS activities.
-
Dashboards for: Overview, Network, Alerts, Authentication, IAM and DNS Activities.
Security Lake Spotlight Content Pack
The Security Lake Spotlight content pack contains:
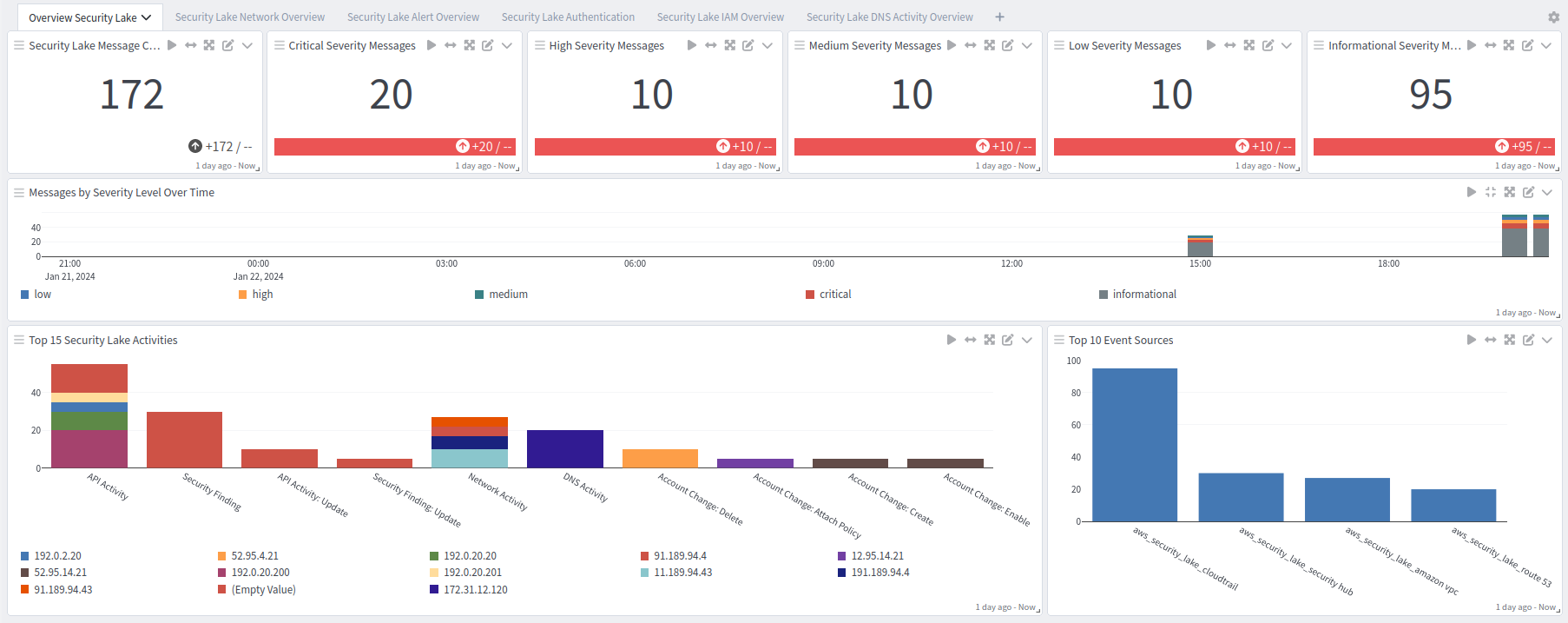
Security Lake Overview tab: Overview
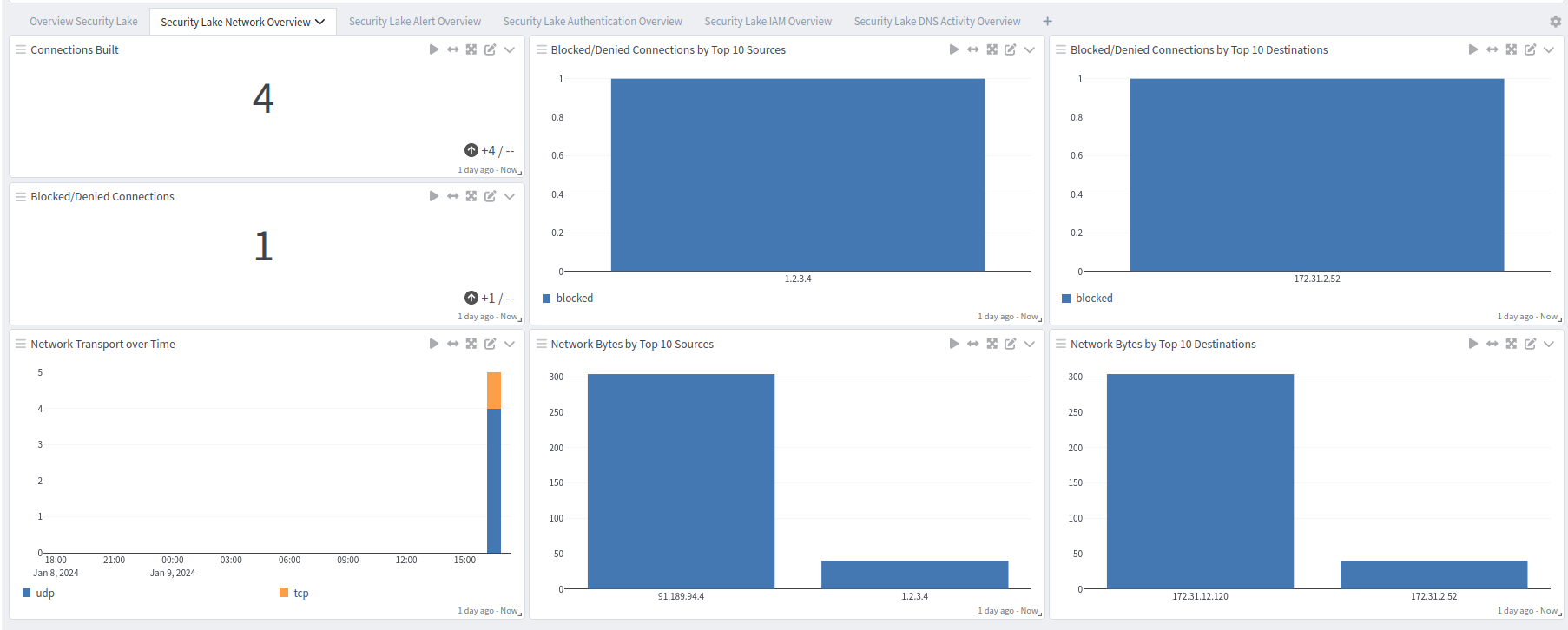
Security Lake Overview tab: Network
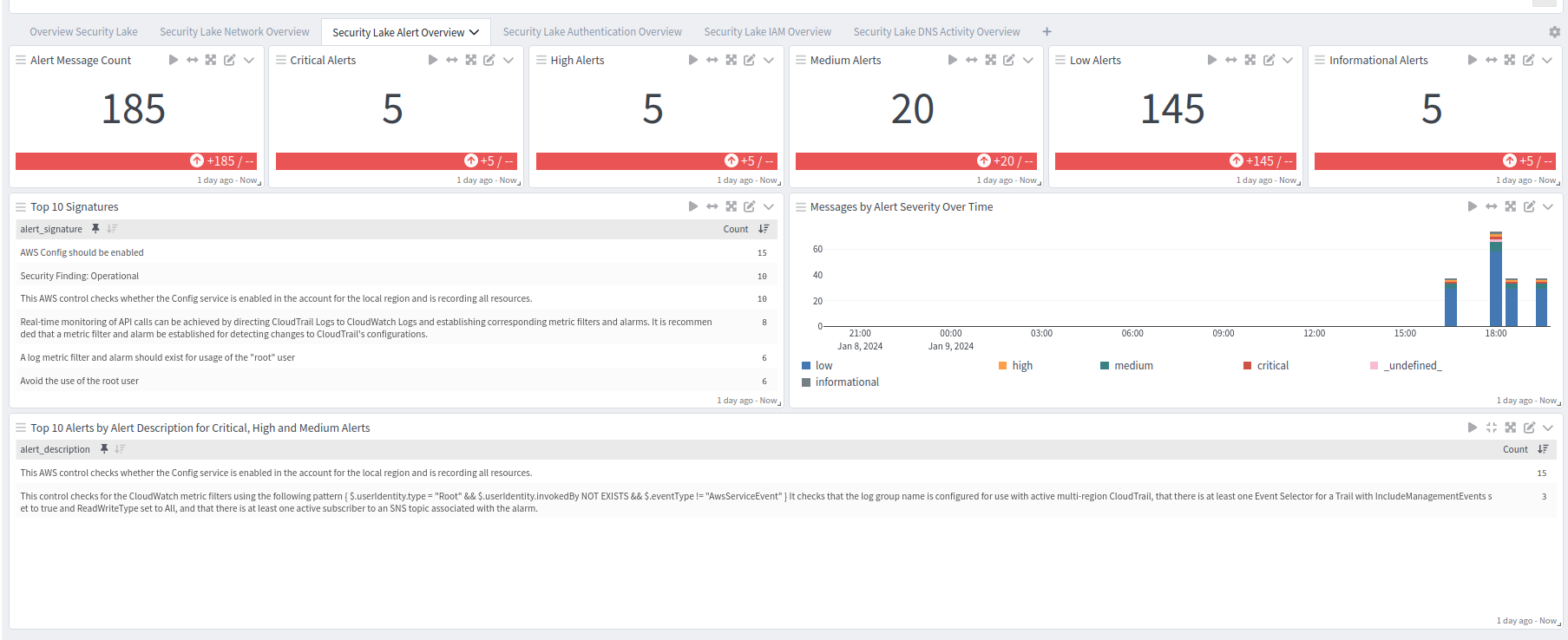
Security Lake Overview tab: Alerts
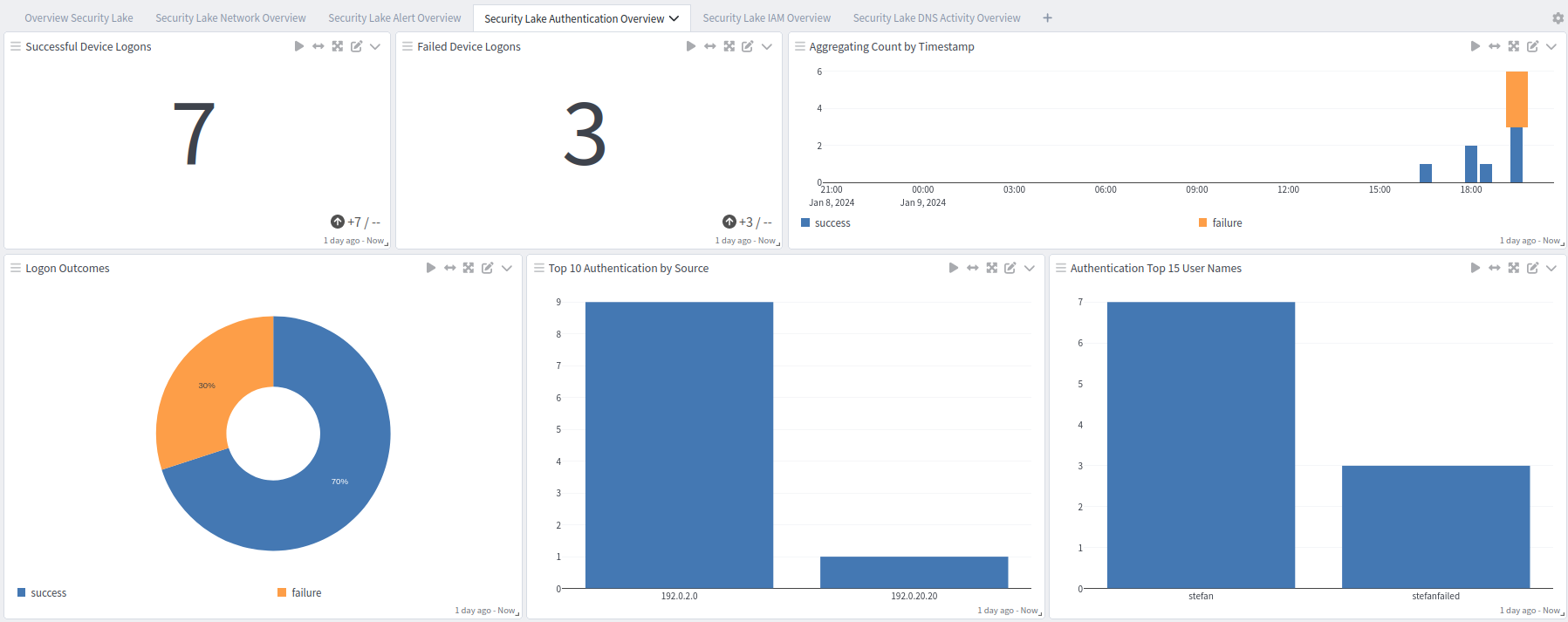
Security Lake Overview tab: Authentication Overview
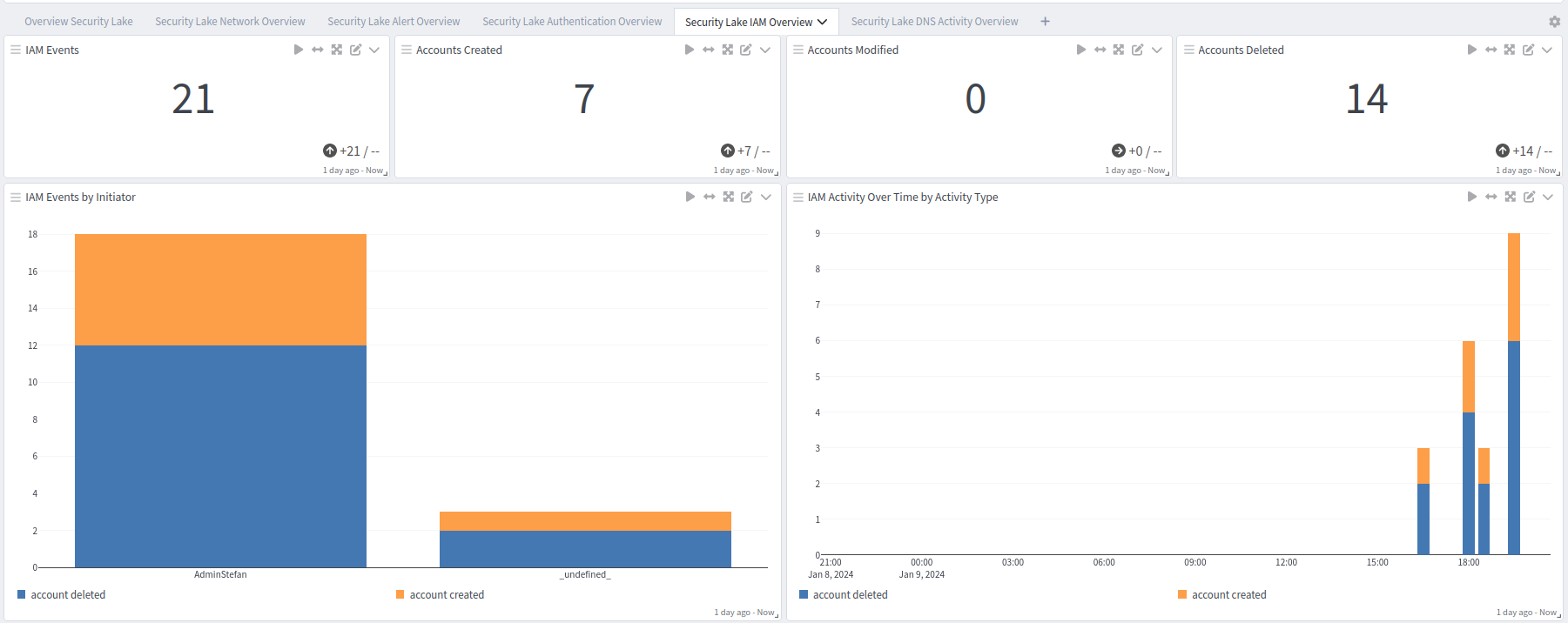
Security Lake Overview tab: IAM Overview
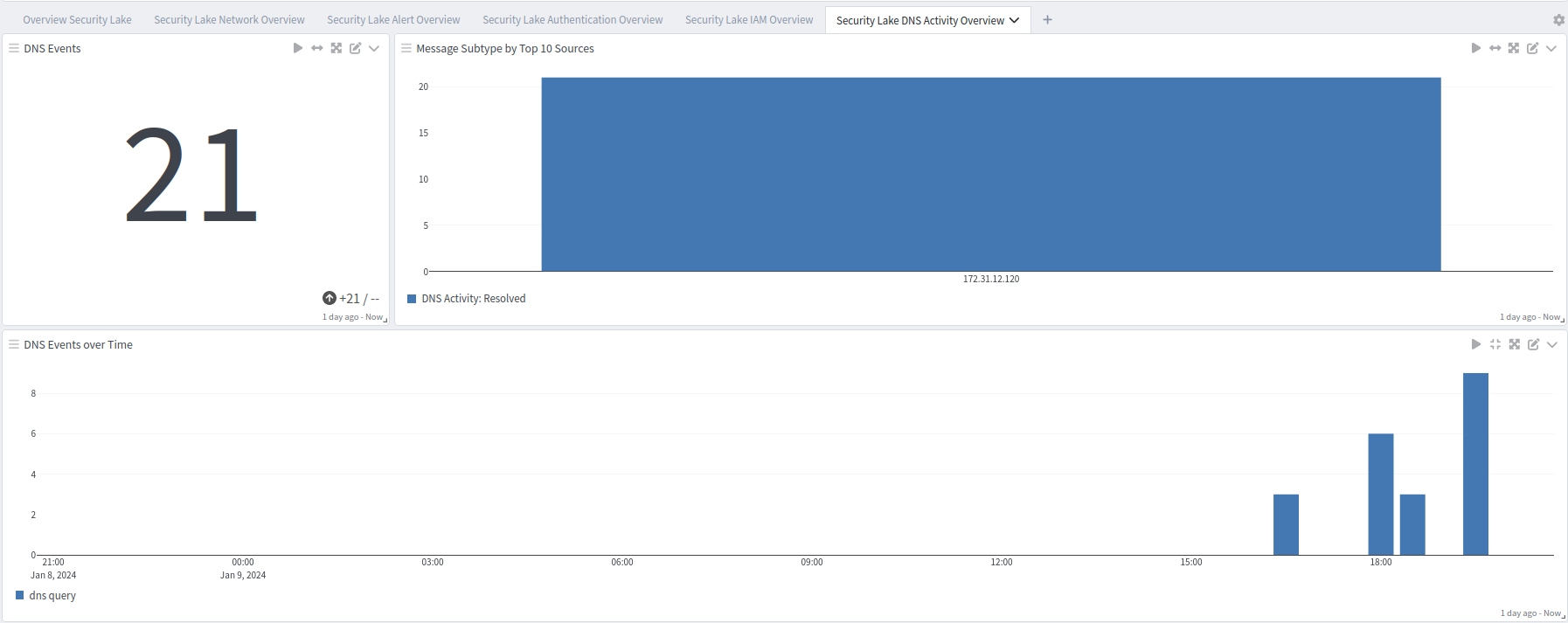
Security Lake Overview tab: DNS Overview