The Juniper SRX line of firewalls combine effective security, SD-WAN, routing, switching and WAN interfaces with next-generation firewall and advanced threat mitigation capabilities. It provides secure connectivity across distributed enterprise locations.
Requirement(s)
-
Juniper SRX devices running Junos OS 17.4. These should be configured to send sd-syslog formatted logs.
-
A Graylog Server with a valid Enterprise license that is running Graylog version 5.0.3 or later.
Graylog Server Requirement
-
This spotlight requires Graylog Server version 5.0.3 or higher. If an earlier version is used, fields will be improperly processed.
Not Supported
-
N/A
Stream Configuration
This technology pack includes one stream:
-
“Illuminate:Juniper Messages”
Index Set Configuration
This technology pack includes one index set definition:
-
“Juniper Logs”
Log Format Examples
<14>1 2023-08-02T06:20:55.496Z RT_FLOW - RT_FLOW_SESSION_CREATE [junos@2636.1.1.1.2.129 source-address="192.168.1.2" source-port="49158" destination-address="10.10.10.10" destination-port="80" connection-tag="0" service-name="junos-http" nat-source-address="172.16.1.2" nat-source-port="29479" nat-destination-address="10.10.10.10" nat-destination-port="80" nat-connection-tag="0" src-nat-rule-type="source rule" src-nat-rule-name="trust_Zone" dst-nat-rule-type="N/A" dst-nat-rule-name="N/A" protocol-id="6" policy-name="default-permit" source-zone-name="trust" destination-zone-name="untrust" session-id="6389" username="N/A" roles="N/A" packet-incoming-interface="ge-0/0/1.0" application="UNKNOWN" nested-application="UNKNOWN" encrypted="UNKNOWN" application-category="N/A" application-sub-category="N/A" application-risk="-1" application-characteristics="N/A" src-vrf-grp="N/A" dst-vrf-grp="N/A" tunnel-inspection="Off" tunnel-inspection-policy-set="root" source-tenant="N/A" destination-service="N/A"]
<14>1 2023-08-02T06:20:13.049Z RT_IDS - RT_SCREEN_TCP [junos@2636.1.1.1.2.40 attack-name="SYN flood!" source-address="192.168.1.1" source-port="40001" destination-address="192.168.1.2" destination-port="50010" source-zone-name="trustZone" interface-name="ge-0/0/1.0" action="drop"]
Requirements
-
Juniper SRX Logging
-
Junos OS must be configured to send log messages via the sd-syslog format.
When compared to standard syslog, the sd-syslog format is an overly structured system log file format. Information regarding this format can be found at:
What is Provided
Rules to normalize and enrich Juniper SRX log messages.
Juniper SRX Log Message Processing
The Illuminate processing of Juniper SRX log messages provides the following:
-
Field extraction, normalization and message enrichment for Juniper SRX log messages.
-
GIM Categorization of the following messages:
| Juniper SRX Log Type | GIM Category | GIM Subcategory |
|---|---|---|
RT_FLOW_SESSION_CLOSE
|
network | network.flow |
RT_FLOW_SESSION_CREATE
|
network | network.open |
IDP_ATTACK_LOG_EVENT
|
network | network.flow |
APPTRACK_SESSION_CLOSE
|
network | network.flow |
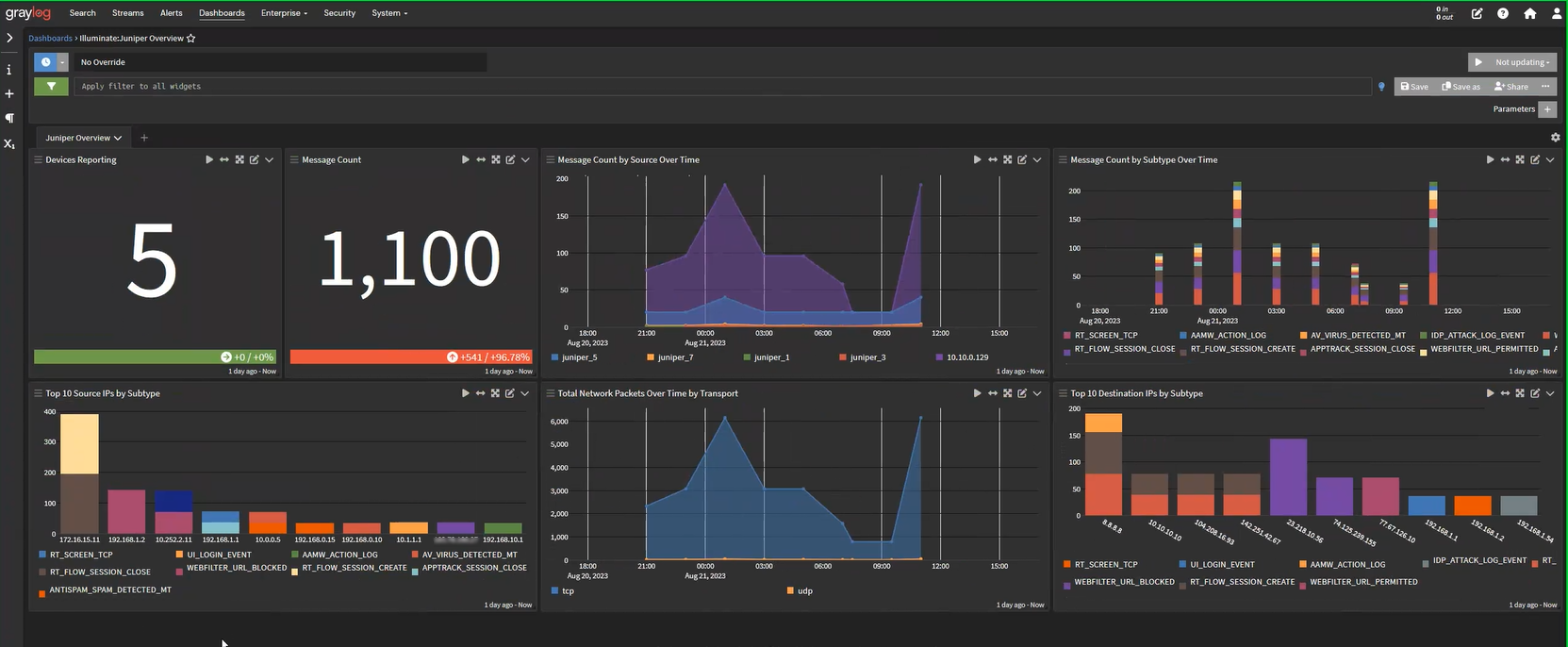
Juniper SRX Spotlight Content Pack
-
Dashboard: Illuminate:Juniper SRX Overview