PowerShell is a task automation and configuration management program from Microsoft. This technology pack processes PowerShell logs.
Requirement(s)
-
Windows 10, Windows 11, or Windows Server 2023
-
PowerShell 5.1 or 7
-
Log delivery agent: Winlogbeat 7.11/8.8 or NXLog 3.2
-
Graylog Server with a valid enterprise license running Graylog version 5.0.3 or later
-
Illuminate 3.4+
Supported Logs/Event IDs
200, 300, 400, 403, 500, 501, 600, 800, 4100, 4101, 4102, 4103, 4104, 4105, 4106, 32784, 40961, 40962, 53504, 53506.
Supported Event Log Names
-
Microsoft-Windows-PowerShell/Operational
-
PowerShellCore/Operational
-
Windows PowerShell
This pack will normalize common fields for PowerShell if shipped to one of these three listed event log names.
Stream Configuration
This technology pack includes one stream:
-
“Illuminate:Powershell Messages”
Index Set Configuration
This technology pack includes one index set definition:
-
“powershell Logs”
Log Examples
These logs come from Windows Event Viewer as evtx files are not human readable.
Requirements
-
The pack works with Winlogbeat and NXlog.
-
(NXLog + Sidecar) NXLog's binaries need to be installed under
C:\Program Files (x86)\nxlogor the permissions for Sidecar file access has to be adjusted.
Graylog Sidecar Configuration
Please follow Graylog documentation to install Sidecar. You need to add the following paths in your Winlogbeat or NXLog configuration:
Winlogbeat (with Security logs):
winlogbeat:
event_logs:
- name: Security
- name: Microsoft-Windows-PowerShell/Operational
- name: PowerShellCore/Operational
- name: Windows PowerShellExample config file for NXLog (with Security logs):
<Input eventlog>
Module im_msvistalog
PollInterval 1
SavePos False
ReadFromLast True
<QueryXML>
<QueryList>
<Query Id='1'>
<Select Path='Security'>*</Select>
<Select Path='Windows Powershell'>*</Select>
<Select Path='PowerShellCore/Operational'>*</Select>
<Select Path='Microsoft-Windows-PowerShell/Operational'>*</Select>
</Query>
</QueryList>
</QueryXML>
</Input>Adjust the host IP and port accordingly to your Graylog server. Configuration files are key sensitive, and correct spacing is necessary. Installation of NXlogs binaries in C:\Program Files (x86)\nxlog is recommended, but if you choose a different location, you must adjust the Sidecar file permissions and define a new ROOT location. If you are not using PowerShellCore (PowerShell 6.x and higher), omit the PowerShellCore line. To capture remote PowerShell access, add path: Microsoft-Windows-WinRM/Operational (not supported by this pack).
-
Graylog Input: Beats with Beats type prefix
PowerShell Configuration
-
Not all PowerShell logs are logged by default. If needed, activate Script Block Logging (event ID 4104), Module Logging (event ID 4103), and others via group policy.
-
PowerShell version 5 (and lower) and PowerShellCore version 6.x (and higher) have separate policy and registry settings. If you want to log both versions, you need to adjust both keys.
-
PowerShellCore uses PowerShellCore/Operational as an additional log source.
Attention: Depending on your environment PowerShell logging might generate very large volumes of data.
What is Provided
-
Rules to normalize and enrich PowerShell log messages
-
Dashboards
PowerShell Message Processing
The Illuminate processing of PowerShell log messages provides the following:
-
Field extraction, normalization, and message enrichment for PowerShell log messages.
-
GIM Categorization of the following messages:
vendor_command_name GIM Event Type Code GIM Event Type Add-LocalGroupMember 111007 group member added New-LocalUser 110000 account created New-LocalGroup 110002 group created Enable-LocalUser 112001 account enabled Disable-LocalUser 111501 account disabled Remove-LocalUser 110500 account locked Remove-LocalGroupMember 111008 group member removed Remove-LocalGroup 110501 group deleted Rename-LocalUser 111003 account renamed Rename-LocalGroup 111009 group properties modified Set-LocalGroup 111009 group properties modified Set-LocalUser 111000 account modified Clear-EventLog 220000 audit log cleared Start-Process 190000 process started Stop-Process 190100 process stopped Start-Service 210000 service started Stop-Service 210100 service stopped Get-LocalGroupMember 119500 group membership enumerated
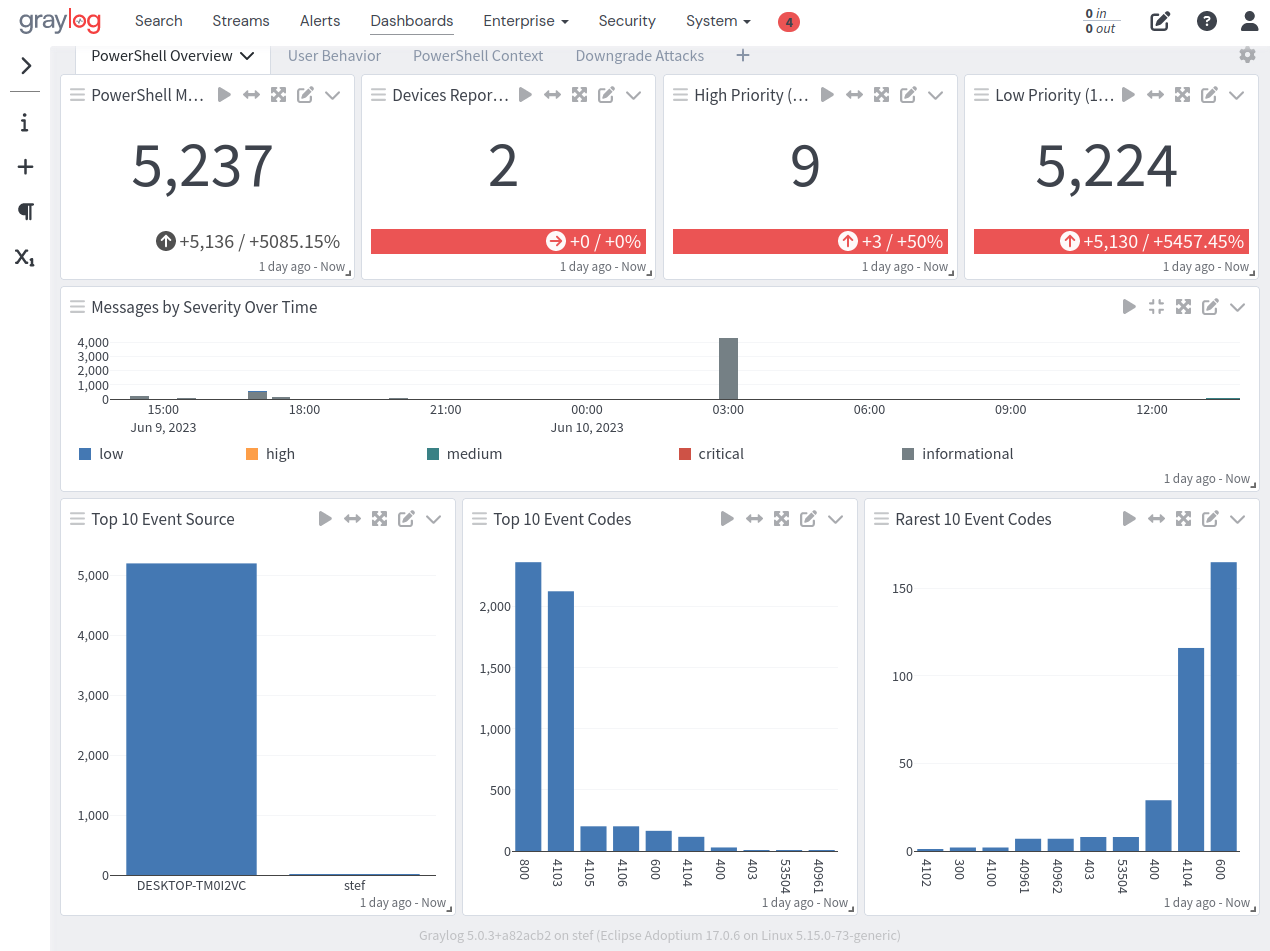
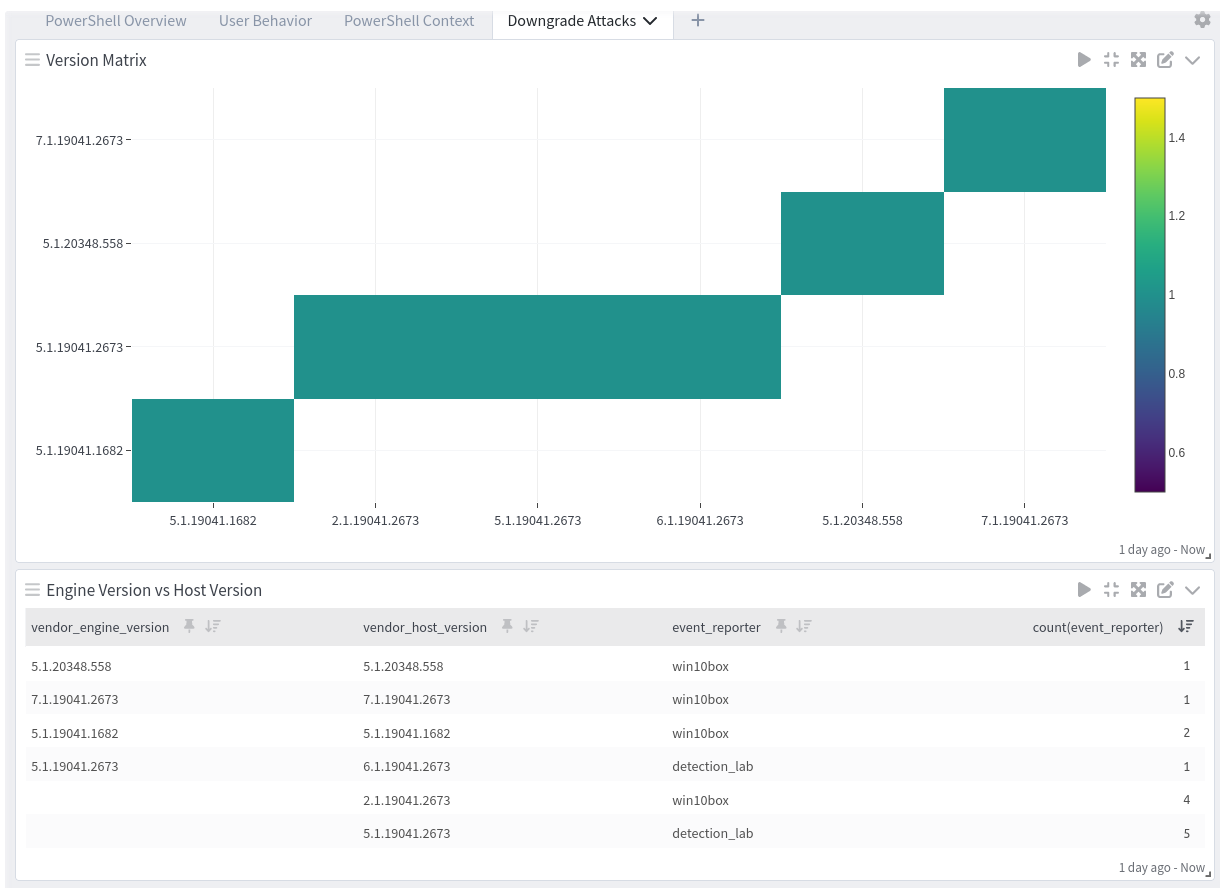
PowerShell Spotlight Content Pack
PowerShell offers one dashboard with four tabs. One overview dashboard and three dashboards around relevant data for sigma rules.