Windows DNS Server is a core Windows Server role that provides domain name resolution services for internal and external network resources. This content pack enables comprehensive parsing of both Analytical and Audit DNS logs, offering deep visibility into query activity across clients, DNS resolution behaviors and metrics over time, and configuration changes. These logs are critical for detecting malicious use of DNS and maintaining infrastructure integrity.
Analytical logs, sourced from the Microsoft-Windows-DNSServer Event Tracing for Windows (ETW) provider, record every DNS query and response handled by the server. This high-volume telemetry is essential for monitoring name resolution patterns and identifying abnormal traffic such as DNS tunneling or data exfiltration. Designed for performance, ETW-based logging minimizes overhead even at high query rates.
Audit logs, captured from the Microsoft-Windows-DNS-Server/Audit channel, focus on administrative operations — changes to zones, resource records, DNSSEC, and server settings. These events are vital for detecting unauthorized modifications, maintaining an audit trail, and ensuring DNS infrastructure integrity.
Supported Version(s)
- Windows Server 2016 and later
Hint: Analytic logs from enhanced DNS logging are available on Windows Server 2012 R2 with Hotfix KB2956577 as well, but the Filebeat agent version required for this pack does not support Windows Server 2012.
Requirements
-
Graylog 6.1.0+ with a valid Enterprise license.
-
Windows DNS Server installed and DNS Analytic/Audit logs enabled on the system.
-
Filebeat agent version 8.13.0 through 8.19.x running standalone; see Log Collection for more information.
-
Illuminate Core: DNS Processing Add-on Pack (optional for some Spotlight widgets).
Stream Configuration
This technology pack includes one stream:
-
"Illuminate:Windows DNS Server Event Messages"
Index Set Configuration
This technology pack includes one index set definition:
-
"Windows DNS Server Event Messages"
Log Collection
This content pack requires a minimum Filebeat version of 8.17.0 and maximum version of 8.19.x for log collection due to the constraint that DNS Server Analytical logging exclusively relies on Event Tracing for Windows (ETW). Filebeat is one of the few log delivery agents that natively supports ETW through its ETW input module.
It is important to note that Filebeat must be run standalone, not bundled with Graylog Sidecar. The bundled Filebeat version does not include the required compatibility with ETW.
DNS Server Audit logs are enabled by default, but Analytic logs are not. Refer to the Microsoft documentation on how to enable the DNS Server Analytic event log.
Filebeat Standalone Configuration Example
Please refer to the official guide to installing and configuring Filebeat for Windows.
-
Create a Beats input in Graylog. Ensure that the option Do not add Beats type as prefix is disabled (unchecked).
-
See the following example Filebeat configuration:
Copy# Needed for Graylog
fields_under_root: true
output.logstash:
hosts: ["GRAYLOG_SERVER:5044"]
path:
data: C:\Program Files\Filebeat\data
logs: C:\Program Files\Filebeat\logs
tags:
- windows
filebeat.inputs:
- type: etw
id: etw-dnsserver
enabled: true
provider.name: Microsoft-Windows-DNSServer
session_name: DNSServer-Analytical # IMPORTANT for parsing to recognize Analytical events
trace_level: verbose
match_any_keyword: 0x8000000000000000
match_all_keyword: 0
- type: winlog
id: winlog-dnsserver-audit
enabled: true
name: "Microsoft-Windows-DNSServer/Audit"
ignore_older: 24hHint: Note that the parser for this pack requires the user-definedsession_nameto beDNSServer-Analytical(case-insensitive) in order to identify Analytic log events. -
Edit the Filebeat config to ship to your Graylog server IP or hostname.
-
Ensure that DNS Server Analytic and Audit logs are enabled for the system.
What Is Provided
-
Parsing rules to extract Windows DNS Server Analytic and Audit event logs into Graylog schema compatible fields
-
Field normalization and data enrichment for additional investigative context
-
Illuminate Spotlight dashboard to support DNS transactional and administrative activity monitoring, provide useful insights into DNS patterns across the network, and highlight potential security threats
Events Processed by This Technology Pack
The Windows DNS Server content pack supports the following events. Generic processing will be provided for any Event IDs not listed.
Event IDs
Analytic Events
| Event ID | Description |
|---|---|
| 256 | Query received |
| 257 | Response success |
| 258 | Response failure |
| 259 | Ignored query |
| 260 | Recursive query out |
| 261 | Response in |
| 262 | Recursive query timeout |
| 263 | Update in |
| 264 | Update response |
| 265 | IXFR request out |
| 266 | IXFR request in |
| 267 | IXFR response out |
| 268 | IXFR response in |
| 269 | AXFR request out |
| 270 | AXFR request in |
| 271 | AXFR response out |
| 272 | AXFR response in |
| 273 | XFR notification in |
| 274 | XFR notification out |
| 275 | XFR notify ACK in |
| 276 | XFR notify ACK out |
| 277 | Dynamic update forward |
| 278 | Dynamic update response in |
| 279 | Internal lookup CNAME |
| 280 | Internal lookup additional |
Audit Events
| Event ID | Description |
|---|---|
| 512 | Zone create |
| 513 | Zone delete |
| 514 | Zone updated |
| 515 | Record create |
| 516 | Record delete |
| 517 | RRSET delete |
| 518 | Node delete |
| 519 | Record create - dynamic update |
| 520 | Record delete - dynamic update |
| 521 | Record scavenge |
| 522 | Zone scope create |
| 523 | Zone scope delete |
| 525 | Zone sign |
| 526 | Zone unsign |
| 527 | Zone re-sign |
| 528 | Key rollover start |
| 529 | Key rollover end |
| 530 | Key retire |
| 531 | Key rollover triggered |
| 533 | Key poke rollover |
| 534 | Export DNSSEC |
| 535 | Import DNSSEC |
| 536 | Cache purge |
| 537 | Forwarder reset |
| 540 | Root hints |
| 541 | Server setting |
| 542 | Server scope create |
| 543 | Server scope delete |
| 544 | Add trust point DNSKEY |
| 545 | Add trust point DS |
| 546 | Remove trust point |
| 547 | Add trust point root |
| 548 | Restart server |
| 549 | Clear debug logs |
| 550 | Write dirty zones |
| 551 | Clear statistics |
| 552 | Start scavenging |
| 553 | Enlist directory partition |
| 554 | Abort scavenging |
| 555 | Prepare for demotion |
| 556 | Write root hints |
| 557 | Listen address |
| 558 | Active refresh trust points |
| 559 | Pause zone |
| 560 | Resume zone |
| 561 | Reload zone |
| 562 | Refresh zone |
| 563 | Expire zone |
| 564 | Update from DS |
| 565 | Write and notify |
| 566 | Force aging |
| 567 | Scavenge servers |
| 568 | Transfer primary key server |
| 569 | Add SKD |
| 570 | Modify SKD |
| 571 | Delete SKD |
| 572 | Modify SKD state |
| 573 | Add delegation |
| 574 | Create client subnet record |
| 575 | Delete client subnet record |
| 576 | Update client subnet record |
| 577 | Create server level policy |
| 578 | Create zone level policy |
| 579 | Create forwarding policy |
| 580 | Delete server level policy |
| 581 | Delete zone level policy |
| 582 | Delete forwarding policy |
GIM Categorization
GIM categorization is provided for the following messages:
| GIM Event Category | GIM Event Subcategory | GIM Event Type | GIM Event Type Code |
|---|---|---|---|
| name resolution | name resolution.dns request | dns query | 140000 |
| name resolution | name resolution.dns answer | dns response | 140200 |
| name resolution | name resolution.error | dns error | 140300 |
| name resolution | name resolution.default | dns message | 149999 |
Parsed Fields
This pack parses out the following fields. Note that this list is not comprehensive.
Common
| Field Name | Example Value | Field Type | Description |
|---|---|---|---|
| event_created | 2025-03-08T04:35:20.293Z | date | Date/time that the event occurred or was first read by the agent |
| event_reporter | dnssvr01 | keyword | The name of the agent that delivered the message |
| event_reporter_ip | 192.168.51.40 | keyword | IP address of the agent host |
| event_reporter_hostname | dnssvr01 | keyword | Hostname of the agent host |
| event_source | dnssvr01 | keyword | Hostname or IP of source system that generated the event |
| event_source_product | windows_dns_server | keyword | Identifier for Windows DNS Server log source |
| network_protocol | dns | keyword | The network protocol used |
Analytic Logs
| Field Name | Example Value | Field Type | Description |
|---|---|---|---|
| event_code | 257 | long | The Event ID representing the Windows DNS Server Analytic log message type |
| event_outcome | success | keyword | The outcome (success/failure) of the event action |
| event_uid | {0254B809-BB52-4B64-9C49-A00E452ECA56} | keyword | A globally unique identifier associated with the event, useful for tracking complete conversations |
| event_error_code | 2 | keyword | Assigned from query_result_code when the value is non-zero, indicating an error response |
| message | DNS Response success | text | A concise summary of the event |
| network_bytes | 875 | long | The size in bytes of the DNS packet data |
| network_transport | udp | keyword | The transport layer protocol used |
| policy_name | AllowedSubnet | keyword | The name of any policy applied to the DNS query |
| query_record_type | TXT | keyword | The DNS record type being requested (QTYPE) |
| query_record_type_code | 16 | keyword | The code of the DNS record type being requested (QTYPE code) |
| query_request | google.com | keyword | The name being resolved in the DNS request (QNAME) |
| query_response | _undefined_ | keyword | (NOT IMPLEMENTED) The name resolution answer, currently undefined for all events. Windows DNS Server Analytic logs do not include the query answers as explicit fields. A functionality to extract the answer data from the raw packet data is planned for a future iteration of this pack. |
| query_result | NOERROR | keyword | The DNS response status (RCODE name) |
| query_result_code | 0 | keyword | The DNS response code (RCODE) |
| source_ip | 192.168.19.121 | ip | IP address of the source from which the DNS query originated |
| source_port | 55344 | long | The port from which the DNS query originated |
| destination_ip | 8.8.8.8 | ip | IP address of the destination to which the DNS query is sent or the response is received |
| destination_port | 61893 | long | The port to which the DNS query is sent or the response is received |
| vendor_data_additional_info | VirtualizationInstance:. | keyword | Extra metadata related to the event |
| vendor_data_cache_scope | Default | keyword | The cache scope applied, such as if the response was retrieved from a local cache |
| vendor_data_dnssec | 0 | keyword | Whether DNSSEC was used in the transaction |
| vendor_data_elapsed_time | 2 | long | The time taken to process the request |
| vendor_data_flags | 33152 | keyword | DNS header information represented as a bitmask |
| vendor_data_header_flags | ["AA"] | keyword | Array of DNS header flags |
| vendor_data_interface_ip | 127.0.0.1 | keyword | The IP address of the network interface on the DNS server processing the transaction |
| vendor_data_forward_interface_ip | 10.50.1.253 | The IP address of the network interface used by the DNS server when forwarding a query to an upstream resolver | |
| vendor_data_packet_data | 0x000381800001000C0000000006676F6F67... | keyword | The raw DNS packet data in hexadecimal format |
| vendor_data_queries_attached | 0 | keyword | The number of queries attached to an event |
| vendor_data_xid | 11660 | keyword | The transaction ID |
| vendor_data_qxid | 4 | keyword | The query transaction ID |
| vendor_data_recursion_depth | 1 | keyword | The number of recursive lookups performed to resolve the DNS query |
| vendor_data_recursion_scope | . | keyword | The scope of recursion allowed in handling the DNS query |
| vendor_data_scope | Default | keyword | The DNS scope in which the query was processed |
| vendor_data_secure | 0 | keyword | Whether the transaction took place over a secure channel |
| vendor_data_zone | ..Cache | keyword | The DNS zone involved in the event |
| vendor_data_zone_scope | Default | keyword | The scope of the DNS zone involved in the event |
| vendor_domain_sld_tld | google.com | keyword | The combination of the question name's second level and top level domains (not eTLD) |
| vendor_domain_sld | keyword | The question name's second level domain | |
| vendor_domain_tld | com | keyword | The question name's top level domain (not eTLD) |
| vendor_event_category | LOOK_UP | keyword | The category of the Analytic event describing the task performed |
| vendor_event_category_code | 1 | long | The category code of the Analytic event describing the task performed |
| vendor_event_channel | 16 | keyword | Specific to Windows ETW event processing |
| vendor_event_description | Response success | keyword | Description of the Event ID associated with the Analytic message |
| vendor_event_outcome_reason | System | keyword | The reason for the DNS query outcome, often given for failed or ignored queries and timeouts |
| vendor_event_provider | Microsoft-Windows-DNSServer | keyword | The name of the Windows ETW provider |
| vendor_event_provider_guid | {eb79061a-a566-4698-9119-3ed2807060e7} | keyword | The GUID of the Windows ETW provider |
| vendor_event_session | DNSServer-Analytical | keyword | The name of the Windows ETW session |
| vendor_event_severity | information | keyword | The event severity rating derived from the source log level |
| vendor_input_type | etw | keyword | The input type, expected to be ETW for Windows DNS Server Analytic logs |
| vendor_opcode_code | 0 | keyword | Specific to Windows ETW event processing |
Audit Logs
| Field Name | Example Value | Field Type | Description |
|---|---|---|---|
| event_code | 516 | long | The Event ID representing the Windows DNS Server Audit log message type |
| event_log_name | Microsoft-Windows-DNSServer/Audit | keyword | The Windows event log channel from which the event originates |
| event_uid | 99 | keyword | The unique event record ID |
| message | A resource record of type 1, name ns2.example.com, TTL 1200 and RDATA 0x0A000210 was created in scope Default of zone example.com via dynamic update from IP Address 192.168.19.121. | text | The Audit event text |
| network_bytes | 4 | long | The total bytes transferred during the event |
| policy_name | AllowedSubnet | keyword | The name of any policy associated with the event |
| query_record_type | * | keyword | The DNS record type being requested (QTYPE) |
| query_record_type_code | 255 | keyword | The code of the DNS record type being requested (QTYPE code) |
| source_ip | 192.168.19.121 | ip | IP address of the source host |
| destination_ip | 8.8.8.8 | ip | IP address of the destination host |
| user_name | Administrator | keyword | Name of the user account associated with the event |
| user_id | S-1-5-21-313282886-420110098-1052476632-500 | keyword | SID of the user account associated with the event |
| user_domain | GRAYLOG-TESTLAB | keyword | Domain of the user account associated with the event |
| user_type | User | keyword | The type of user account associated with the event |
| vendor_event_action | create | keyword | The action described in the event |
| vendor_event_category | ZONE_OP | keyword | The category of the Audit event describing the task performed |
| vendor_event_category_code | 5 | long | The category code of the Audit event describing the task performed |
| vendor_event_description | Zone updated | keyword | Description of the Event ID associated with the Audit message |
| vendor_event_provider | Microsoft-Windows-DNSServer | keyword | The event log source |
| vendor_event_provider_guid | {eb79061a-a566-4698-9119-3ed2807060e7} | keyword | The GUID of the event log source |
| vendor_event_severity | information | keyword | The event severity rating derived from the source log level |
| vendor_input_type | winlog | keyword | The input type, expected to be Winlog for Windows DNS Server Audit logs |
| vendor_opcode | Info | keyword | The opcode defined by the event record |
| vendor_data_action | keyword | ||
| vendor_data_active_key | keyword | ||
| vendor_data_base64_data | keyword | ||
| vendor_data_child_zone | keyword | ||
| vendor_data_client_subnet_list | keyword | ||
| vendor_data_client_subnet_record | keyword | ||
| vendor_data_condition | keyword | ||
| vendor_data_criteria | keyword | ||
| vendor_data_crypto_algorithm | keyword | ||
| vendor_data_current_rollover_status | keyword | ||
| vendor_data_current_state | keyword | ||
| vendor_data_denial_of_existence | keyword | ||
| vendor_data_digest | keyword | ||
| vendor_data_digest_type | keyword | ||
| vendor_data_distribute_trust_anchor | keyword | ||
| vendor_data_key_record_set_ttl | keyword | ||
| vendor_data_key_signature_validity_period | keyword | ||
| vendor_data_ds_record_generation_algorithm | keyword | ||
| vendor_data_ds_record_set_ttl | keyword | ||
| vendor_data_ds_signature_validity_period | keyword | ||
| vendor_data_enable_rfc_5011_key_rollover | keyword | ||
| vendor_data_errors_per_second | keyword | ||
| vendor_data_event_string | keyword | ||
| vendor_data_file_path | keyword | ||
| vendor_data_forwarders | keyword | ||
| vendor_data_friendly_name | keyword | ||
| vendor_data_guid | keyword | ||
| vendor_data_initial_rollover_offset | keyword | ||
| vendor_data_ipv4_prefix_length | keyword | ||
| vendor_data_ipv6_prefix_length | keyword | ||
| vendor_data_is_enabled | keyword | ||
| vendor_data_is_key_master_server | keyword | ||
| vendor_data_key_id | keyword | ||
| vendor_data_key_length | keyword | ||
| vendor_data_key_master_server | keyword | ||
| vendor_data_key_or_zone | keyword | ||
| vendor_data_ksk_or_zsk | keyword | ||
| vendor_data_key_protocol | keyword | ||
| vendor_data_key_storage_provider | keyword | ||
| vendor_data_key_tag | keyword | ||
| vendor_data_key_type | keyword | ||
| vendor_data_last_rollover_time | keyword | ||
| vendor_data_leak_rate | keyword | ||
| vendor_data_listen_addresses | keyword | ||
| vendor_data_lookup | keyword | ||
| vendor_data_master_server | keyword | ||
| vendor_data_mode | keyword | ||
| vendor_data_name | keyword | ||
| vendor_data_NAME | keyword | ||
| vendor_data_name_server | keyword | ||
| vendor_data_new_friendly_name | keyword | ||
| vendor_data_new_property_values | keyword | ||
| vendor_data_new_scope | keyword | ||
| vendor_data_new_value | keyword | ||
| vendor_data_next_key | keyword | ||
| vendor_data_next_rollover_action | keyword | ||
| vendor_data_next_rollover_time | keyword | ||
| vendor_data_node_name | keyword | ||
| vendor_data_nsec3_hash_algorithm | keyword | ||
| vendor_data_nsec3_iterations | keyword | ||
| vendor_data_nsec3_opt_out | keyword | ||
| vendor_data_nsec3_random_salt_length | keyword | ||
| vendor_data_nsec3_user_salt | keyword | ||
| vendor_data_old_friendly_name | keyword | ||
| vendor_data_old_property_values | keyword | ||
| vendor_data_old_scope | keyword | ||
| vendor_data_parent_has_secure_delegation | keyword | ||
| vendor_data_processing_order | keyword | ||
| vendor_data_propagation_time | keyword | ||
| vendor_data_property_key | keyword | ||
| vendor_data_qname | keyword | Deliberately not mapped to query_request to avoid GIM "dns query" categorization which isn't always applicable in the Audit event context | |
| vendor_data_rdata | keyword | ||
| vendor_data_recursion_scope | keyword | ||
| vendor_data_replication_scope | keyword | ||
| vendor_data_response_per_second | keyword | ||
| vendor_data_rollover_period | keyword | ||
| vendor_data_rollover_type | keyword | ||
| vendor_data_rrl_exception_list | keyword | ||
| vendor_data_scavenge_servers | keyword | ||
| vendor_data_scope | keyword | ||
| vendor_data_scopes | keyword | ||
| vendor_data_scope_weight | keyword | ||
| vendor_data_scope_weight_new | keyword | ||
| vendor_data_scope_weight_old | keyword | ||
| vendor_data_secure_delegation_polling_period | keyword | ||
| vendor_data_seized_or_transfered | keyword | ||
| vendor_data_server_name | keyword | ||
| vendor_data_setting | keyword | ||
| vendor_data_signature_inception_offset | keyword | ||
| vendor_data_standby_key | keyword | ||
| vendor_data_store_keys_in_ad | keyword | ||
| vendor_data_subtree_aging | keyword | ||
| vendor_data_tc_rate | keyword | ||
| vendor_data_total_responses_in_window | keyword | ||
| vendor_data_ttl | long | ||
| vendor_data_type | keyword | ||
| vendor_data_virtualization_id | keyword | ||
| vendor_data_window_size | keyword | ||
| vendor_data_with_new_keys | keyword | ||
| vendor_data_with_without | keyword | ||
| vendor_data_zone | keyword | ||
| vendor_data_zone_file | keyword | ||
| vendor_data_zone_scope | keyword | ||
| vendor_data_zone_signature_validity_period | keyword | ||
| vendor_data_zone_name | keyword |
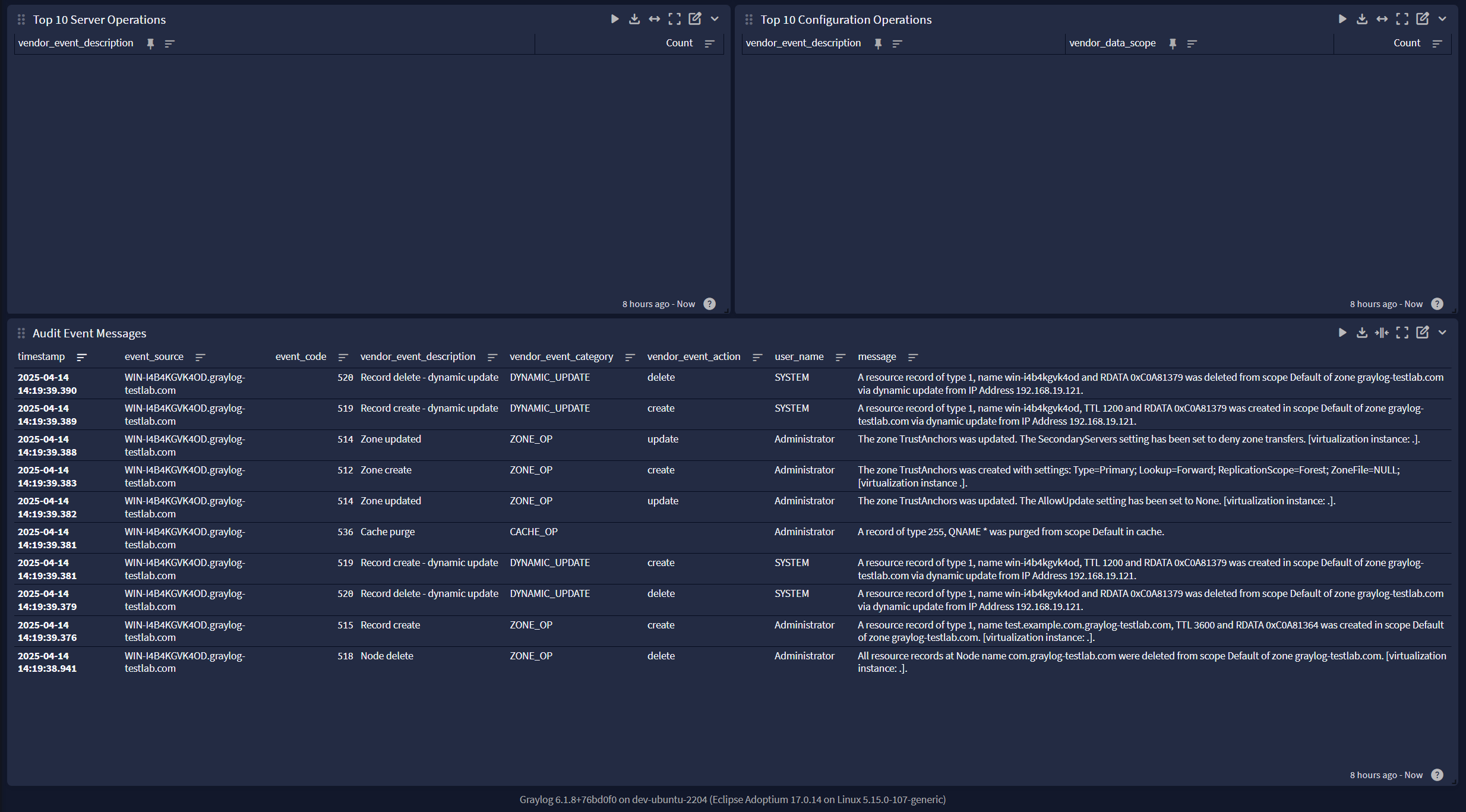
Windows DNS Server Spotlight Content Pack
Windows DNS Server Spotlight offers a dashboard with 3 tabs:
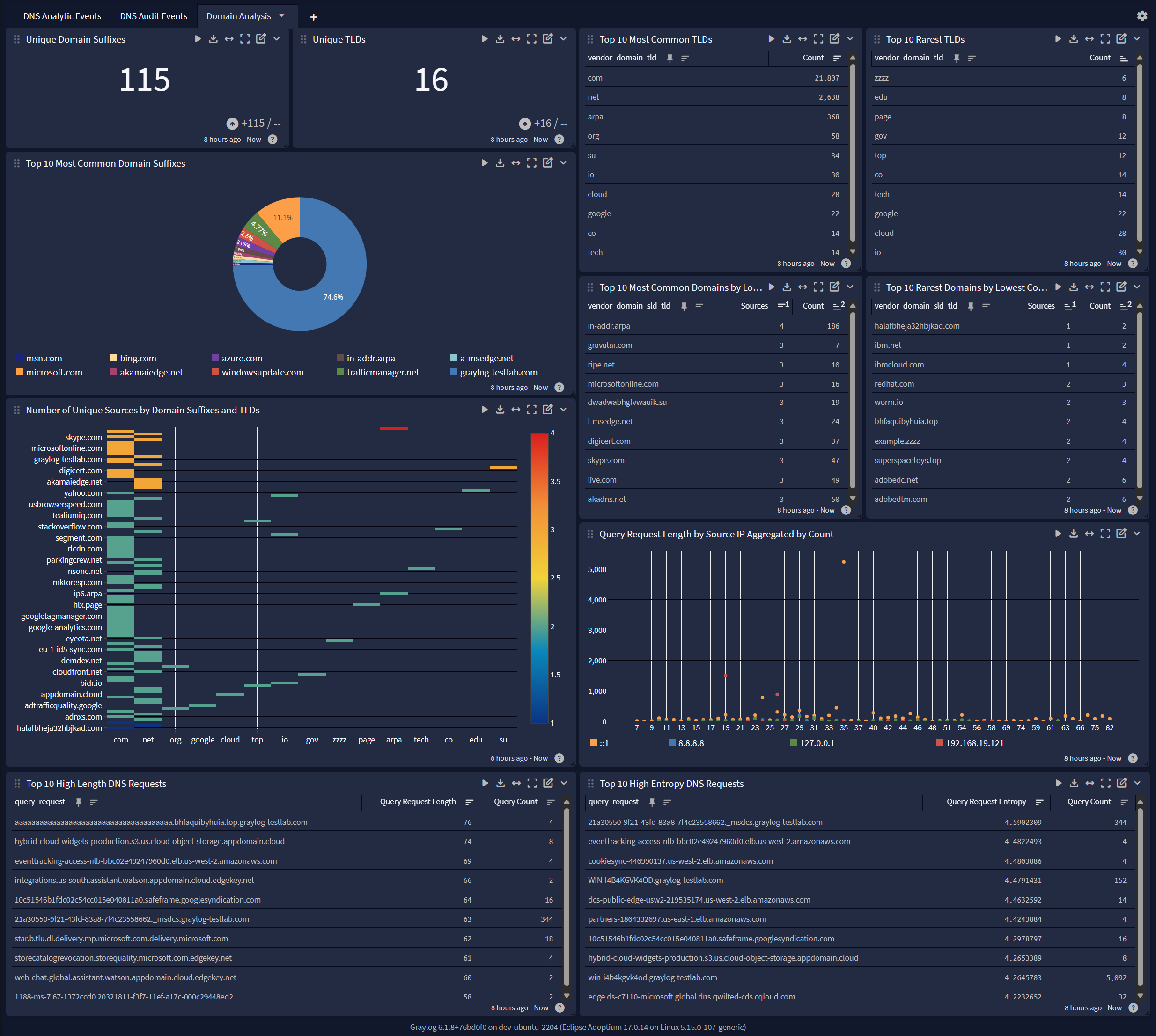
DNS Analytic Events
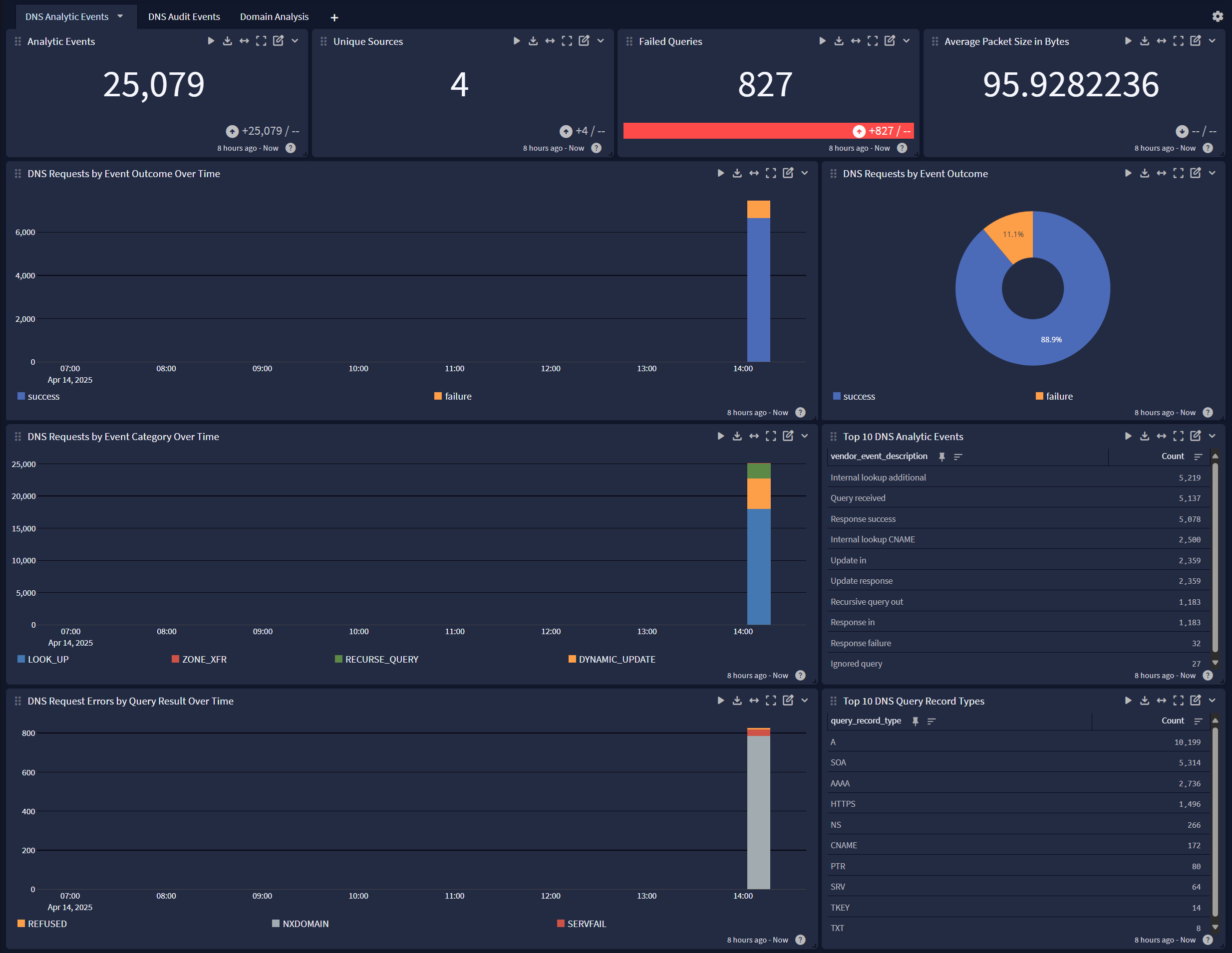
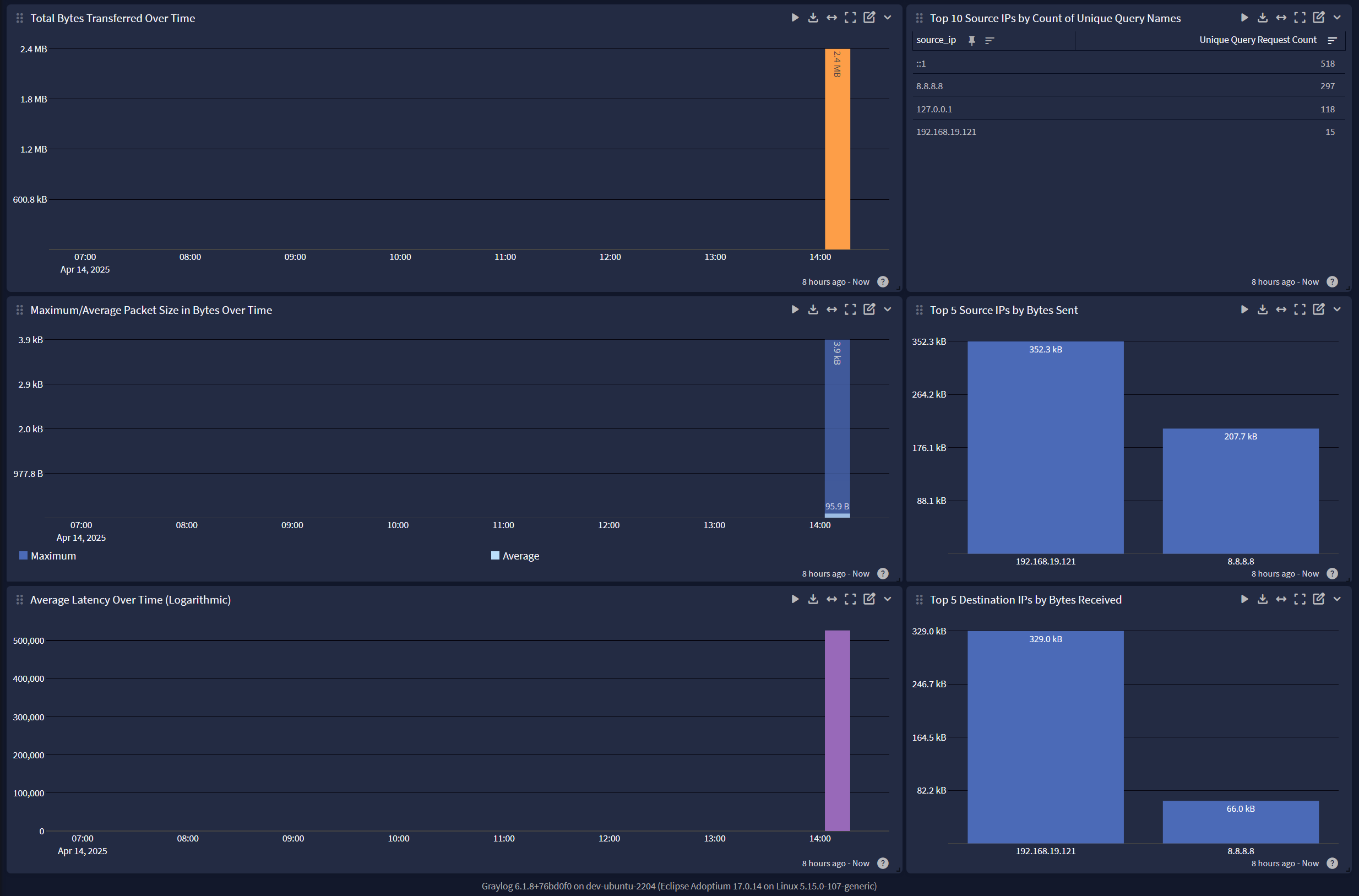
DNS Audit Events
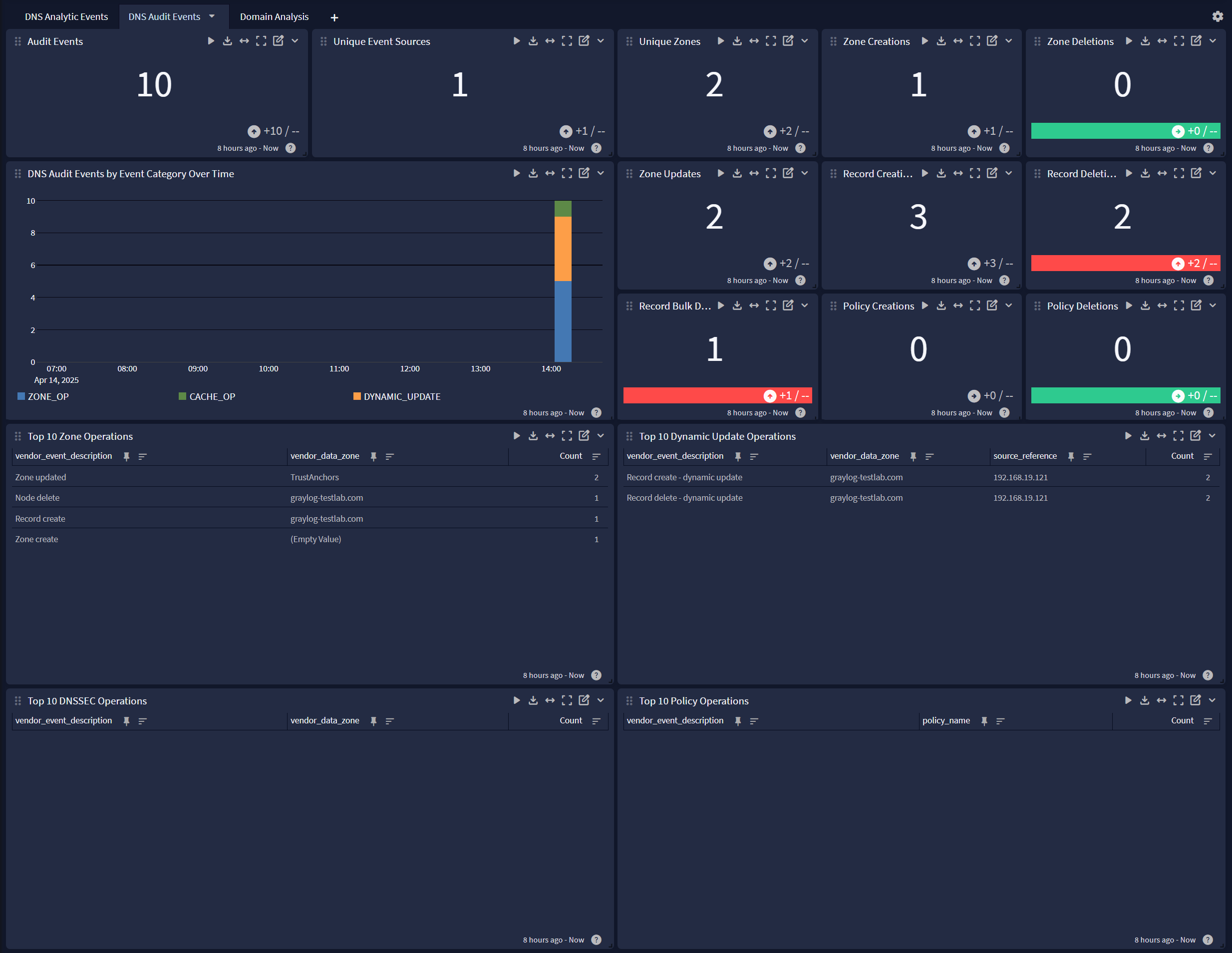
Domain Analysis