Symantec Endpoint Security is a cloud and hybrid-managed solution that provides the protection of SEP, attack detection of EDR, and other technologies to secure devices.
Requirement(s)
-
Symantec Endpoint Security Enterprise or Symantec Endpoint Security Complete license
-
Minimum of Graylog 6.0+ with a valid enterprise license
Not Supported
Please note the following categories are not supported in this content pack:
-
Evidence of Compromise
-
Information Protection
-
License
Stream Configuration
This technology pack includes one stream:
-
“Illuminate:Symantec Endpoint Security Messages”
Index Set Configuration
This technology pack includes one index set definition:
-
“Symantec Endpoint Security Logs”
Log Format Examples
{"device_os_type_id":100,"lineage":["C:\\Users\\user2\\AppData\\Local\\Microsoft\\Teams\\current\\Teams.exe"],"feature_uid":"1DF0351C-146D-4F07-B155-BF5C7077FF40","type":"event_query_results","seq_num":177,"ref_uid":"4D5B6F97-6101-4C7E-B922-930E25360417","legacy_product_uid":"d965a903-7d7a-7347-decb-101fd144c5bc","id":1,"product_uid":"31B0C880-0229-49E8-94C5-48D56B1BD7B9","feature_name":"DETECTION_RESPONSE","device_group":"Default","product_name":"Symantec Endpoint Security","version":"1.0.0","command_uid":"","device_ip":"192.168.1.3","device_vhost":1,"timezone":-330,"device_domain":"WORKGROUP","product_ver":"14.3.10148.8000","is_npvdi_client":false,"device_name":"DESKTOP-BP8KOJM","category_id":5,"device_networks":[{"ipv6":["2401:4900:1cb2:ea41:b45a:2aba:b9f5:c3ef","2401:4900:1cb2:ea41:c568:8e7a:5c3c:70aa","fe80:0000:0000:0000:af14:9b46:8337:5c4c"],"mac":"64:79:f0:cd:e9:02","ipv4":["192.168.1.3"]}],"device_os_name":"Windows 11 Professional Edition","type_id":8001,"actor":{"session_id":2,"pid":6932,"uid":"D157FA8E-DF80-F1EE-B896-84BC5A4C9DB5","tid":6468,"start_time":"2024-03-12T04:41:07.479Z","cmd_line":"\"C:\\Users\\user2\\AppData\\Local\\Microsoft\\Teams\\current\\Teams.exe\" --system-initiated","integrity_id":3,"file":{"type_id":1,"created":"2024-03-11T09:36:04.367Z","modified":"2024-03-11T09:36:07.440Z","md5":"4989696e862d359ec09b75f4b2934b4b","sha2":"48cf3cfae4cc99eb5ed7b2fa0104fa8db47b6b13bc9e4c05103cc6b0265e9aeb","size":149479288,"signature_company_name":"Microsoft Corporation","signature_value_ids":[3,5],"security_descriptor":"O:S-1-5-21-2943851542-2441814902-1111111-1002G:S-1-5-21-2943851542-2441814902-1111111-513D:(A;;0x1fffff;;;S-1-5-21-2943851542-2441814902-1111111-1002)(A;;0x1fffff;;;SY)(A;;0x121411;;;S-1-5-5-0-43017645)S:AI","normalized_path":"CSIDL_PROFILE\\appdata\\local\\microsoft\\teams\\current\\teams.exe","path":"c:\\users\\user2\\appdata\\local\\microsoft\\teams\\current\\teams.exe","uid":"5629499534313427","name":"teams.exe","folder":"c:\\users\\user2\\appdata\\local\\microsoft\\teams\\current","original_name":"Teams.exe","signature_level_id":60},"user":{"name":"user1","sid":"S-1-5-21-2943851542-2441814902-1111111-1002","domain":"DESKTOP-BP8KOJM"}},"device_mac":"64:79:f0:cd:e9:02","device_uid":"HvM1Eew9SXmq8F-WGqkYtg","org_unit_uid":"DS-gzhR8RaWMhATsDmbsyg","severity_id":1,"logging_device_post_time":"2024-03-12T15:20:12.970Z","device_time":"2024-03-12T15:20:12.962Z","user_name":"user1","process":{"session_id":2,"pid":9352,"uid":"088F4DEC-E05C-F1EE-B896-84BC5A4C9DB5","start_time":"2024-03-12T15:20:12.962Z","cmd_line":"\"C:\\Users\\user2\\AppData\\Local\\Microsoft\\Teams\\current\\Teams.exe\" --type=renderer --enable-wer --user-data-dir=\"C:\\Users\\user2\\AppData\\Roaming\\Microsoft\\Teams\" --ms-teams-less-cors=522133263 --app-user-model-id=com.squirrel.Teams.Teams --app-path=\"C:\\Users\\user2\\AppData\\Local\\Microsoft\\Teams\\current\\resources\\app.asar\" --autoplay-policy=no-user-gesture-required --disable-background-timer-throttling --lang=en-US --device-scale-factor=1.5 --num-raster-threads=4 --enable-main-frame-before-activation --renderer-client-id=309 --launch-time-ticks=111330447179 --mojo-platform-channel-handle=3992 --field-trial-handle=1852,i,7718261119285444314,14632190959189571843,131072 --enable-features=ContextBridgeMutability,SharedArrayBuffer,WinUseBrowserSpellChecker,WinUseHybridSpellChecker --disable-features=CalculateNativeWinOcclusion,ExtraCookieValidityChecks,ForcedColors,SpareRendererForSitePerProcess,WinRetrieveSuggestionsOnlyOnDemand /prefetch:1","integrity_id":2,"file":{"type_id":1,"created":"2024-03-11T09:36:04.367Z","modified":"2024-03-11T09:36:07.440Z","md5":"4989696e862d359ec09b75f4b2934b4b","sha2":"48cf3cfae4cc99eb5ed7b2fa0104fa8db47b6b13bc9e4c05103cc6b0265e9aeb","size":149479288,"signature_company_name":"Microsoft Corporation","signature_value_ids":[3,5],"security_descriptor":"O:S-1-5-21-2943851542-2441814902-1111111-1002G:S-1-5-21-2943851542-2441814902-1111111-513D:(A;;0x1fffff;;;S-1-5-21-2943851542-2441814902-1111111-1002)(A;;0x1fffff;;;SY)S:AI","normalized_path":"CSIDL_PROFILE\\appdata\\local\\microsoft\\teams\\current\\teams.exe","path":"c:\\users\\user2\\appdata\\local\\microsoft\\teams\\current\\teams.exe","uid":"5629499534313427","name":"teams.exe","folder":"c:\\users\\user2\\appdata\\local\\microsoft\\teams\\current","original_name":"Teams.exe","signature_level_id":60},"user":{"name":"user1","sid":"S-1-5-21-2943851542-2441814902-1111111-1002","domain":"DESKTOP-BP8KOJM"}},"edr_enriched_data":{"category_name":"Generic Data to be sent to Symantec EDR","category_id":201,"event_group_id":"9878AD19-4849-439E-A68A-7353D041C701","suspicion_score":50,"rule_id":1198,"rule_name":"eUserExecution","rule_description":"User execution detected"},"feature_ver":"edr/1.3.0","is_user_present":true,"event_data_type":"fdr","user":{"name":"user1"},"device_os_ver":"10.0.22621","policy":{"uid":"19caded7-de5f-4e05-8000-f71fd8151bb7","name":"Default Detection and Response Policy","version":"2"},"attacks":[{"technique_uid":"T1204","technique_name":"User Execution","tactic_ids":[2],"tactic_uids":["TA0002"]}],"customer_uid":"abc123","device_public_ip":"1.1.1.1","domain_uid":"xyz456","time":"2024-03-12T15:20:12.962Z","log_time":"2024-03-12T15:23:02.261Z","uuid":"8001:059e2820-e084-11ee-e526-000003a26ae1"}
Requirements
-
Symantec Endpoint Security Loggings: Symantec Endpoint Security (SES) utitlizes the Graylog Symantec SES Events input that ingests events and incidents logs in JSON format (as seen above).
What is Provided?
Rules to normalize and enrich Symantec Endpoint Security log messages.
Symantec Endpoint Security Log Message Processing
The Illuminate processing of Symantec Endpoint Security log messages provides the following:
-
Field extraction, normalization and message enrichment for Symantec Endpoint Security log messages.
-
GIM Categorization of the following messages:
| Vendor Event ID | GIM Category | GIM Subcategory |
|---|---|---|
| 8075 | detection
|
detection.default
|
Symantec Endpoint Security Spotlight Content Pack
The Symantec Endpoint Protection Spotlight content pack contains:
-
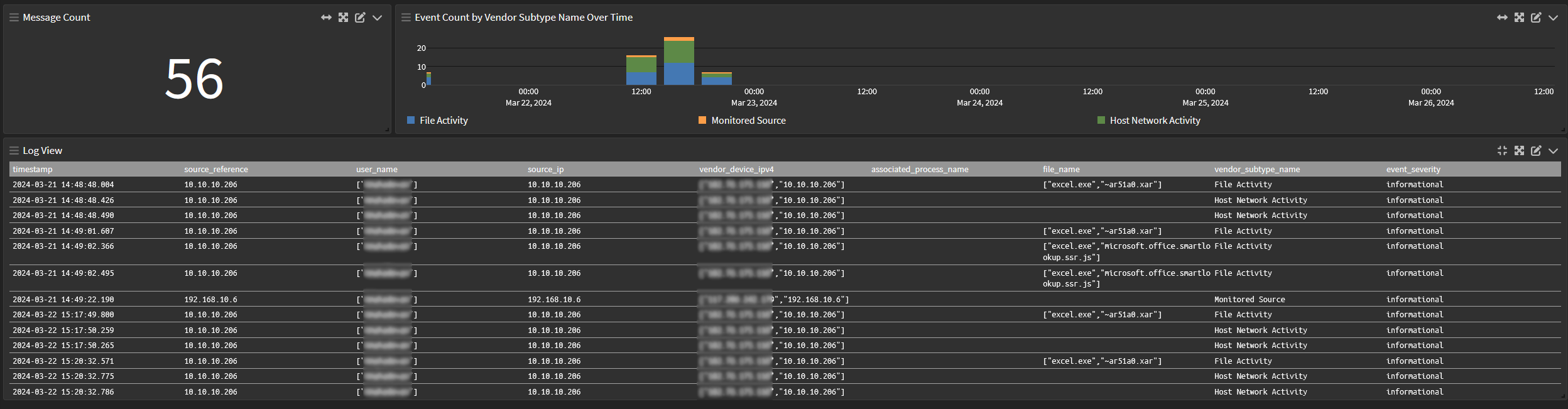
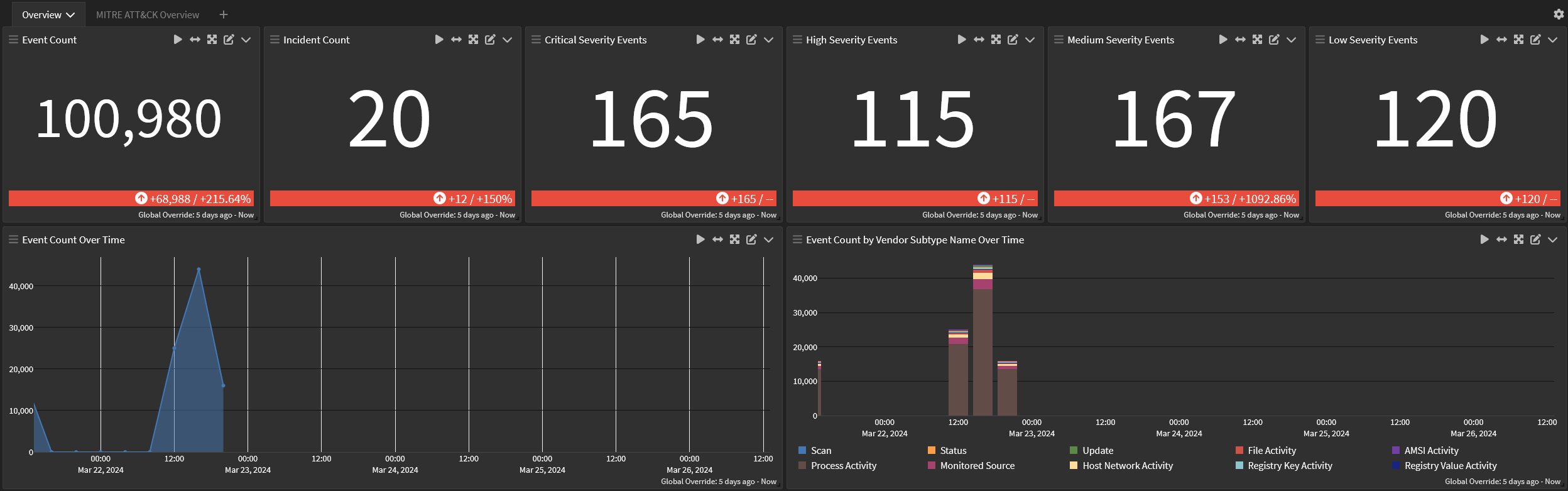
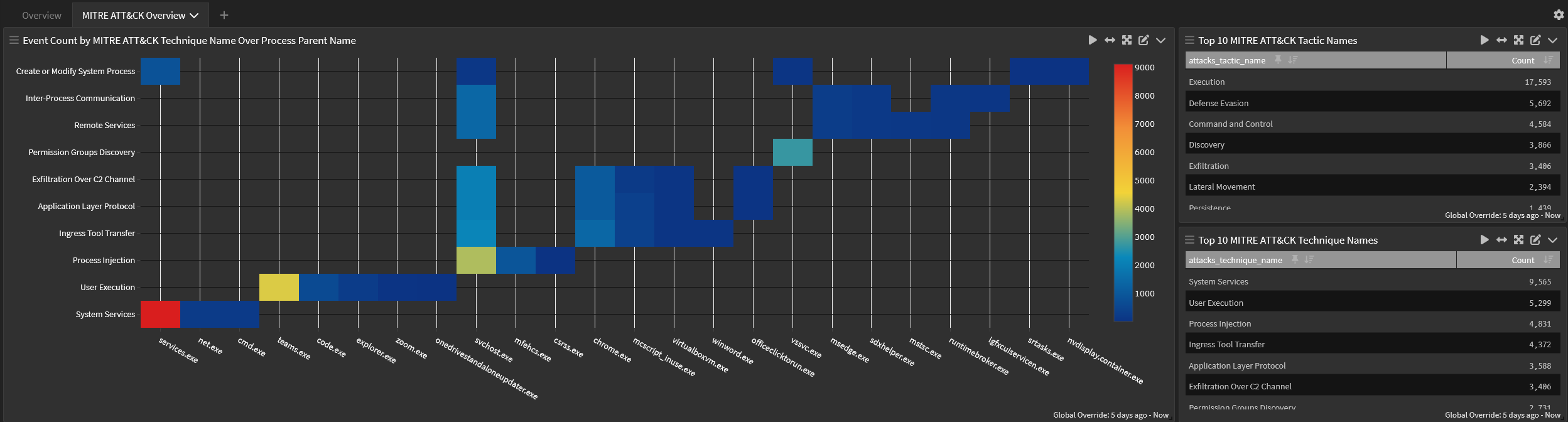
Dashboard: Illuminate:Symantec Endpoint Security Overview
Overview tab
MITRE ATTACK Overview tab
-
Saved Search: Illuminate:Symantec Endpoint Security Correlation UID Log Viewer
Log viewer