Sophos Central is a cloud-based unified security management platform that delivers centralized administration, threat detection, and policy enforcement across a range of security services encompassing network, endpoint, server, mobile, and email security. This content pack extracts fields from Sophos Central Endpoint Protection telemetry and event messages and normalizes them to align with the Graylog schema.
Supported Version(s)
Sophos Central is a continuously updated managed service that does not feature version numbers. This pack was built and tested for integration with the Sophos Central SIEM Integration v1 API. In addition, parsing is designed around Sophos Central events sourced from Windows endpoints. Events from other OS platforms such as macOS may be supported, but not fully tested.
Requirements
-
Graylog 6.2.0+ with a valid Enterprise license
-
Sophos Endpoint agent installed on client hosts with Endpoint Protection policies enabled
-
Sophos Central API credentials created for use with the Graylog Sophos Central input
What is Provided
-
Extraction of fields, normalization, and enrichment of Sophos Central Endpoint Protection event logs
-
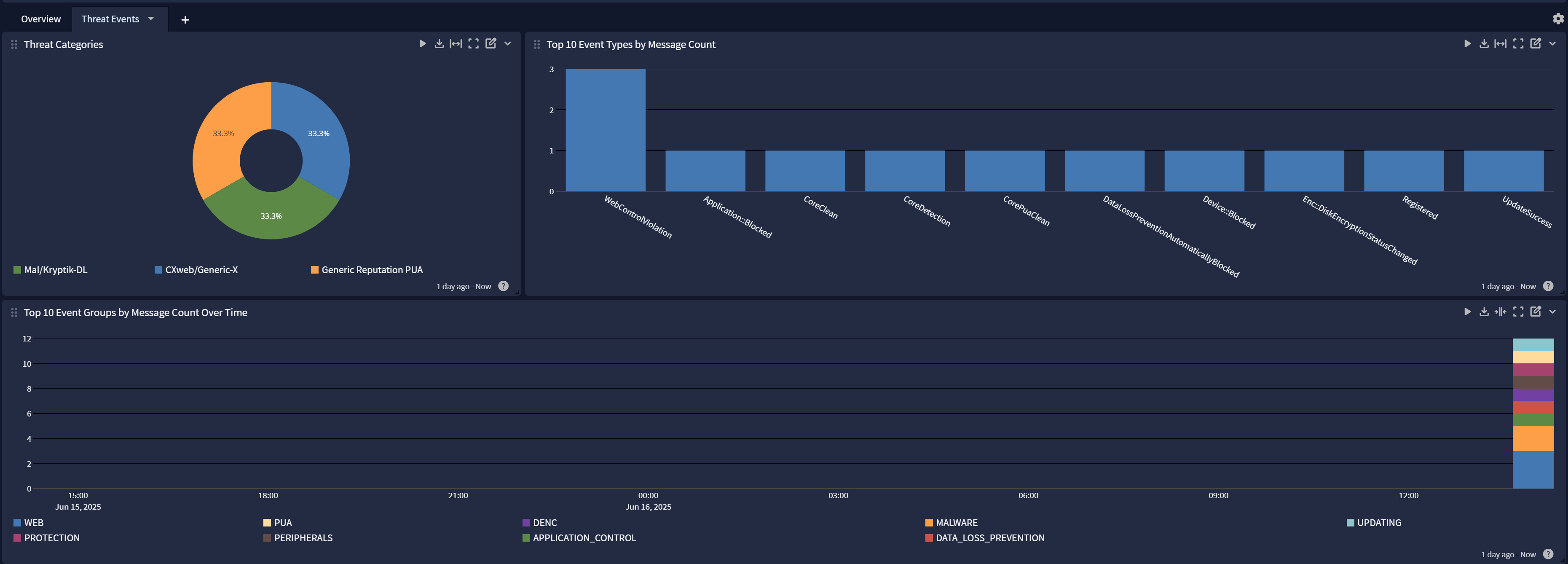
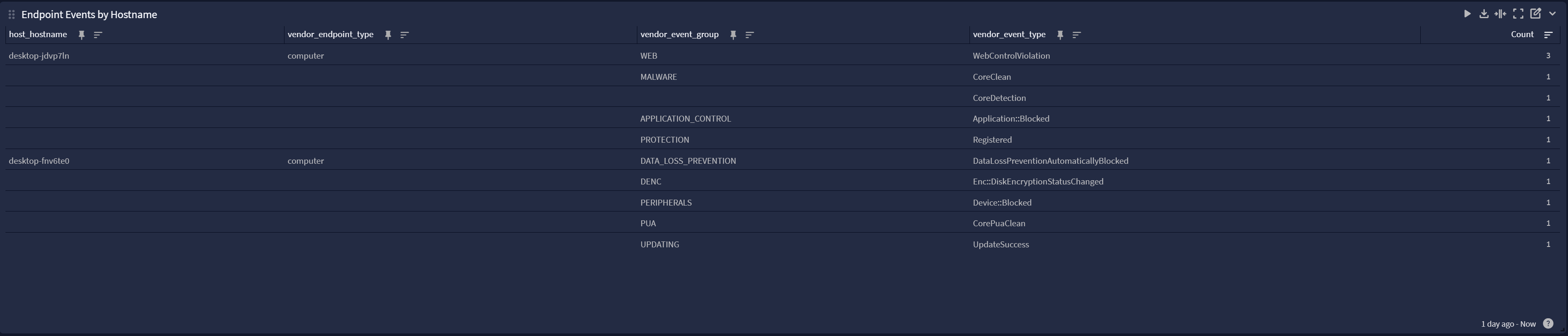
A dashboard for monitoring threat detections and affected endpoints
Stream Configuration
This technology pack includes one stream:
-
"Illuminate:Sophos Messages"
Index Set Configuration
This technology pack includes one index set definition:
-
"Sophos Device Log Messages"
Log Collection
The Sophos Central input can be configured to securely access the Sophos Central SIEM Integration API for log data retrieval.
Configuring a Sophos Central Input
For Graylog to access Sophos Central logs via API, it needs API credentials:
-
Create API credentials in Sophos Central Admin. The assigned role should have read capabilities and access to queries, such as Service Principal Super Admin. A guide can be found here.
-
Copy the generated Client ID and Client Secret and store them securely.
-
Launch a Sophos Central input in Graylog. When prompted, provide the previously obtained Sophos Client ID and Secret.
-
Optionally configure the following input options:
-
Ingest Alerts: Whether to ingest Sophos alerts in addition to events.
-
Polling Interval: How often (in minutes) the input will check for new log data, recommended to leave at default 5 minutes.
-
Enable Throttling: If enabled, it will stop reading new data for this input whenever the system falls behind on message processing and needs to catch up.
-
-
Save the input settings.
If the input does not start automatically, select Start Input to begin retrieving and processing messages from the configured Sophos Central server.
true.
Log Format Example
{"type":"Event::Endpoint::CoreDetection","origin":"SAV","created_at":"2025-01-24T11:32:22.544Z","source_info":{"ip":"192.168.40.176"},"customer_id":"aabbccdd-1234-5678-abcd-ef1234567890","severity":"medium","endpoint_id":"10a1a0aa-aa10-10aa-1010-a01a1aaa01a0","endpoint_type":"computer","user_id":"671565c8eeddce2b21c52a24","threat":"Mal/Kryptik-DL","when":"2025-01-24T11:32:11.870Z","appSha256":"43670ae43df9e361fa15f09f611da32db104ee207ed5af3e7e7f098ad82a68e0","source":"DESKTOP-JDVP7LN\Test234","location":"DESKTOP-JDVP7LN","id":"cc29ad5d-3e42-20da-8790-03f87f291fa6","group":"MALWARE","name":"Malware detected: 'Mal/Kryptik-DL' at 'C:\Users\Test234\Downloads\43670ae43df9e361fa15f09f611da32db104ee207ed5af3e7e7f098ad82a68e0'"}
Event Groups Processed
Logs from event groups not included will have generic processing applied:
-
APPLICATION_CONTROL -
DATA_LOSS_PREVENTION -
DENC -
MALWARE -
PERIPHERALS -
PROTECTION -
PUA -
SYSTEM_HEALTH -
UPDATING -
WEB
Sophos Central Spotlight Content Pack
Overview
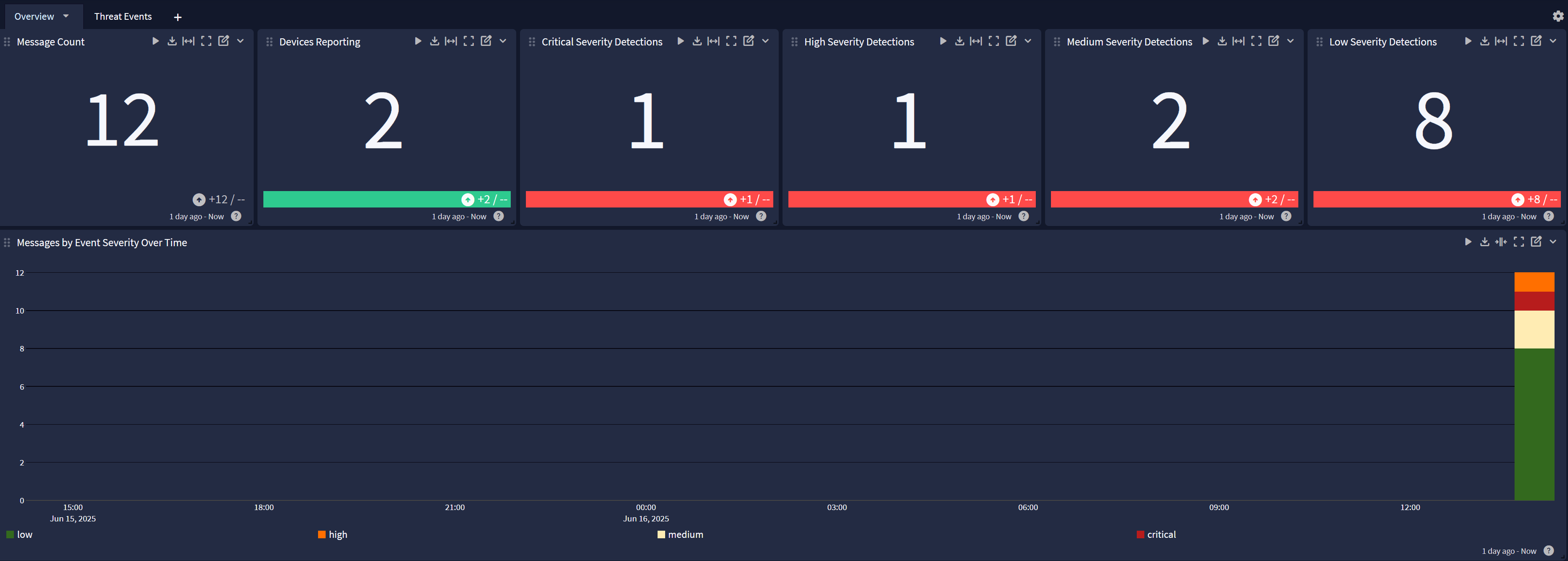
Threat Events