Sendmail is a free and open-source mail transfer agent (MTA) used to route and deliver email on Unix-based systems. This technology pack will process Sendmail logs and includes parsers and dashboards to visualize key data such as sender/recipient activity, delivery status, ruleset rejections, authentication, and processing statistics.
What is Provided
-
Rules to parse, normalize and enrich Sendmail log messages and a dashboard with six tabs covering key insights.
Supported Version(s)
- Tested with Sendmail version 8.15.2 but earlier versions are compatible.
Requirements
- Minimum of Graylog version 5.2.4 with a valid Enterprise license.
Stream Configuration
This technology pack includes 1 stream:
- "Illuminate:Sendmail Mail Server Messages"
Index Set Configuration
This technology pack includes 1 index set definition:
- "Sendmail Mail Server Logs"
Log Collection
- Syslog
- Filebeat (with Sidecar)
Syslog Configuration
Sendmail outputs to syslog under mail facility by default.
-
Create a matching syslog input in Graylog.
-
Configure your syslog server (e.g. rsyslog) to send the logs to Graylog.
Filebeat Configuration
Please refer to the official documentation to setup Graylog Sidecar for filebeat.
-
Create a matching Beats input in Graylog.
-
Create an API access token and Linux filebeat collector.
-
Configure the collector for Sendmail. See the following example snippet:
-
Configure the client with filebeat and Sidecar.
filebeat.inputs:
- input_type: log
paths:
- /var/log/mail.log
type: filestream
fields_under_root: true
fields:
event_source_product: sendmail
event_source_product and - /var/log/mail.log.
Log Format Examples
Receipt Logs
`qA6KmkmX918730: from=<user@corp.example.com>, size=1286, class=0, nrcpts=1, msgid=<498FC718.7000891@corp.example.com>, proto=ESMTP, daemon=MTA, relay=a.mail.example.com [11.111.11.111]`
Delivery Logs
`qABK0GcL913544: to=<user@corp.example.com>, delay=00:00:08, xdelay=00:00:01, mailer=esmtp, pri=1314205, relay=aspmx.l.google.com. [173.194.79.26], dsn=2.0.0, stat=Sent (OK 1234567890 g7zy99885643ion.56)`
Ruleset Rejection Logs
`e5DHeYC11749: ruleset=check_rcpt, arg1=<user@foo.bar.com>, relay=user@mail.bar.com [11.111.11.111], reject=550 5.7.1 <user@foo.bar.com>... Relaying denied`
Authentication Logs
`AUTH=server, relay=11-111-11-111.srv.foo.bar.com [11.111.11.111] (may be forged), authid=gooduser, mech=PLAIN, bits=0`
STARTTLS Logs
`STARTTLS=client, relay=gmail-smtp-in.l.google.com., version=TLSv1/SSLv3, verify=OK, cipher=RC4-SHA, bits=128/128`
Connection Logs
`c22AJzde908658: SMTP outgoing connect on server1.example.com`
Invalid Connection Logs
`m12Umdcw998259: [11.111.11.111] did not issue MAIL/EXPN/VRFY/ETRN during connection to SSLMTA`
Pregreet Traffic Logs
`z1ENNTPj905074: rejecting commands from foo.bar.com [11.111.11.111] due to pre-greeting traffic after 0 seconds`
Rejected Discovery Logs
`u52CZzhr906425: AAAb9625.ne.foo.bar.com [11.111.11.111]: VRFY user [rejected]`
Service Status Logs
`starting daemon (8.14.4): SMTP+queueing@00:10:00`
Events Processed by This Technology Pack
The Sendmail content pack supports:
-
Receipt Logs
-
Delivery Logs
-
Ruleset Rejection Logs
-
Authentication Logs
-
STARTTLS Logs
-
Connection Logs
-
Invalid Connection Logs
-
Pregreet Traffic Logs
-
Rejected Discovery Logs
-
Service Status Logs
Message Fields Included in this Pack
| Field Name | Example Value | Field Type | Description |
|---|---|---|---|
| General Parsing | |||
application_name
|
sendmail | keyword | This field is generated by the syslog input. |
facility
|
keyword | This field is generated by the syslog input. | |
process_id
|
5222 | keyword | This field is generated by the syslog input. |
|
mailsrv1 |
keyword/loweronly |
Hostname or IP of the source system that generated the event. |
|
|
qABK0GcL913544 |
keyword |
The queue ID unique to each message. |
| Receipt | |||
email_from
|
user@graylog.com | keyword | Email address of the sender. |
email_size
|
589 | long | Size of the email message in bytes. |
email_message_id
|
200046040409.e5EECA205337@foo.bar.com |
keyword |
Email Message ID. |
vendor_class
|
0 |
long |
The queue class (numeric precedence) of the message. |
vendor_nrcpts
|
1 |
long |
Number of recipients for the email. |
vendor_daemon
|
MTA |
keyword |
The name of the sender daemon. |
vendor_relay_user
|
user@graylog.com |
keyword |
User of the client relay, the host from which a message was received. |
vendor_relay_warning
|
may be forged |
keyword |
Warning that relay IP or name may be forged. |
source_ip
|
10.1.2.3 |
keyword |
IP address of the client relay, the host from which a message was received. |
source_hostname
|
graylog.com |
keyword |
Hostname of the client relay, the host from which a message was received. |
network_protocol
|
esmtp |
keyword |
The protocol used when the message was received. |
| Delivery | |||
email_to
|
user@graylog.com |
keyword | Email address of the recipient. |
vendor_ctladdr
|
mailadmin | keyword | The controlling user, the name of the user whose credentials are used for delivery. |
vendor_delay
|
00:08:52 | keyword | The total time the message took to be processed from reception to attempted delivery. |
vendor_delay_total_seconds
|
532 | long | The total message delay described in seconds. |
vendor_xdelay
|
00:00:04 | keyword | The total time the message took to be transmitted during final delivery. |
vendor_mailer
|
esmtp | keyword | The name of the delivery agent used. |
vendor_pri
|
30589 | long | The initial priority assigned to the message. |
vendor_dsn
|
2.0.0 | keyword | Delivery Status Notification indicating the outcome of an email delivery attempt. |
vendor_status_full
|
Sent (e6FDCEv13455 Message accepted for delivery) | keyword | The full delivery status of the message. |
vendor_status
|
Sent | keyword | The abbreviated delivery status of the message. |
vendor_status_text
|
e6FDCEv13455 Message accepted for delivery | keyword | The delivery status information returned by the delivery agent or destination host. |
vendor_relay_user
|
user@graylog.com | keyword | User of the destination relay, the host that receives a message. |
vendor_relay_warning
|
may be forged | keyword | Warning that relay IP or name may be forged. |
destination_ip
|
10.1.2.3 | keyword | IP address of the destination relay, the host that receives a message. |
destination_hostname
|
graylog.com | keyword | Hostname of the destination relay, the host that receives a message. |
| Ruleset Rejection | |||
vendor_ruleset
|
check_rcpt | keyword | The ruleset that was used to screen the rejected message. |
vendor_arg1
|
spammer@spammy.com | keyword | The argument to a ruleset check, usually an IP, domain or email address. |
vendor_arg2
|
127.0.0.4 | keyword | Additional argument to a ruleset check, often the query result from abuse lookup services. |
vendor_relay_user
|
user@graylog.com | keyword | User of the client relay, the host from which a message was received. |
vendor_relay_warning
|
may be forged |
keyword |
Warning that relay IP or name may be forged. |
source_ip
|
10.1.2.3 |
keyword |
IP address of the client relay, the host from which a message was received. |
source_hostname
|
graylog.com |
keyword |
Hostname of the client relay, the host from which a message was received. |
vendor_reject
|
550 5.7.1 Mail from 11.111.11.111 rejected by SPAMHAUS. |
keyword |
The reason a message was rejected, often containing the server SMTP response. |
vendor_smtp_response_message
|
<spammer@spammy.com.>... SPAM REJECT |
keyword |
The information provided in an SMTP response. |
smtp_response_code
|
550 |
keyword |
SMTP basic status code. |
smtp_response_code_description
|
Mailbox unavailable |
keyword |
SMTP basic status code description. |
smtp_response_enhanced_class_code
|
5 |
keyword |
SMTP enhanced status class code. |
smtp_response_enhanced_class_code_description
|
Permanent Failure |
keyword |
SMTP enhanced status class code. |
smtp_response_enhanced_status_code
|
7.1 |
keyword |
SMTP enhanced status enumerated status code. |
smtp_response_enhanced_subject_code
|
7 |
keyword |
SMTP enhanced status subject code. |
smtp_response_enhanced_subject_code_description
|
Security or Policy Status |
keyword |
SMTP enhanced status subject code description. |
| Authentication | |||
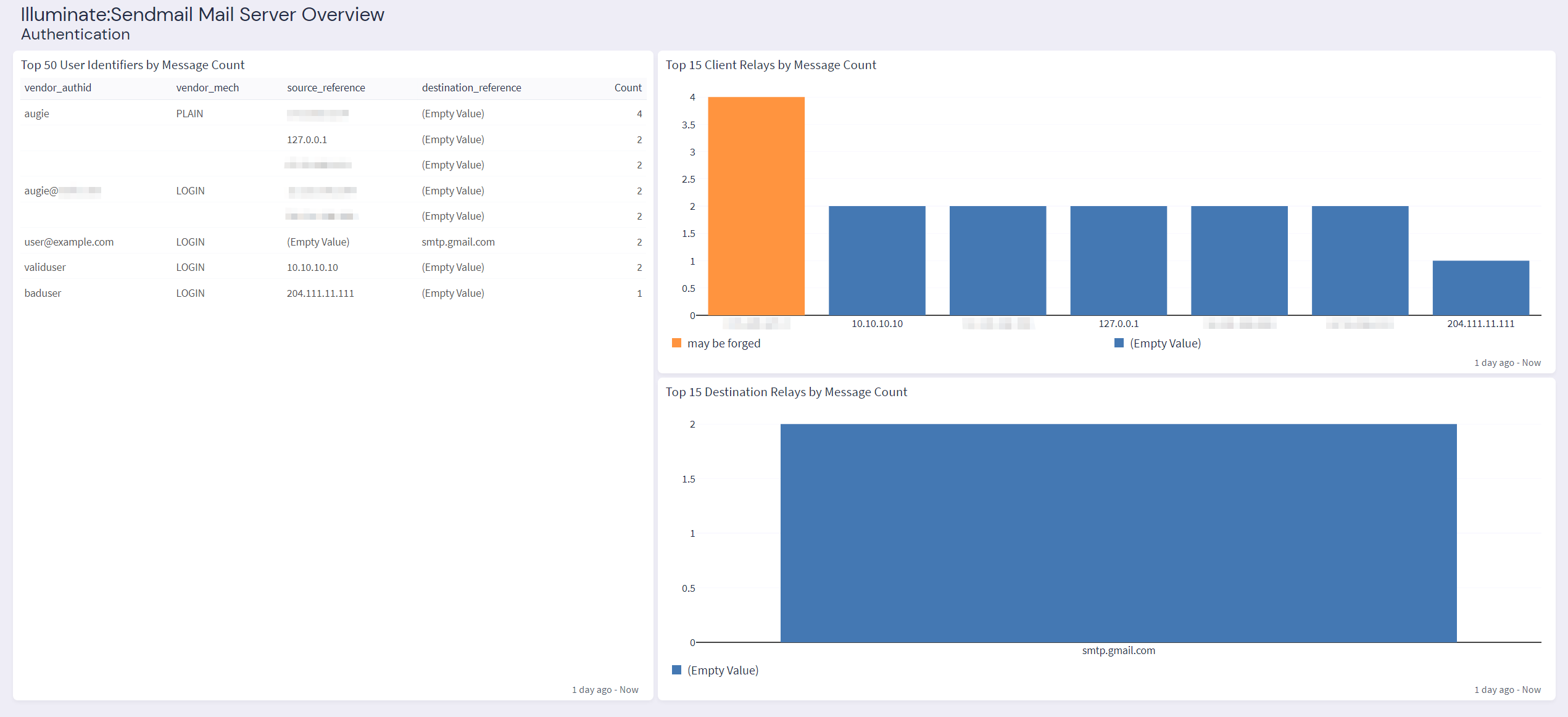
vendor_auth
|
client | keyword | Indicates whether Sendmail acted as the client or server during authentication. |
vendor_authid
|
mailadmin | keyword | The authentication identifier, usually a username. |
vendor_mech
|
LOGIN | keyword | The authentication mechanism used. |
vendor_bits
|
0 | keyword | The strength of encryption used during authentication, or none used. |
|
|
user@graylog.com |
keyword |
User of the client/destination relay depending on the direction of authentication. |
vendor_relay_warning
|
may be forged |
keyword |
Warning that relay IP or name may be forged. |
source_ip
|
10.1.2.3 |
keyword |
IP address of the client relay, the host authenticating to the server. |
source_hostname
|
graylog.com |
keyword |
Hostname of the client relay, the host authenticating to the server. |
destination_ip
|
10.1.2.3 |
keyword |
IP address of the destination relay, the server being authenticated to by a client. |
|
|
graylog.com |
keyword |
Hostname of the destination relay, the server being authenticated to by a client. |
| STARTTLS | |||
vendor_starttls
|
server | keyword | Indicates whether Sendmail acted as the client or server during STARTTLS negotiation. |
vendor_tls_version
|
TLSv1/SSLv3 | keyword | The TLS version used. |
vendor_tls_cipher
|
AES128-SHA | keyword | The cipher suite negotiated for the secure connection. |
vendor_tls_cipher_size
|
128/128 | keyword | The key size used for encryption. |
vendor_starttls_verify
|
OK | keyword | The result of the server certificate verification. |
vendor_starttls_error
|
accept failed | keyword | The error that occurred during STARTTLS negotiation. |
vendor_starttls_error_code
|
-1 | keyword | The result code assigned to a STARTTLS negotiation error. |
vendor_starttls_error_reason
|
sslv3 alert bad certificate | keyword | The reason for a STARTTLS negotiation error. |
vendor_relay_user
|
user@graylog.com | keyword | User of the client/destination relay depending on the direction of connection. |
vendor_relay_warning
|
may be forged | keyword | Warning that relay IP or name may be forged. |
source_ip
|
10.1.2.3 | keyword | IP address of the client relay, the host connecting to the server. |
source_hostname
|
graylog.com | keyword | Hostname of the client relay, the host connecting to the server. |
destination_ip
|
10.1.2.3 | keyword | IP address of the destination relay, the server receiving the connection. |
destination_hostname
|
graylog.com | keyword | Hostname of the destination relay, the server receiving the connection. |
| Connection | |||
vendor_event_action
|
connect | keyword | The action taken in the event. |
vendor_relay_user
|
user@graylog.com | keyword | User of the client/local relay. |
vendor_relay_warning
|
may be forged |
keyword |
Warning that relay IP or name may be forged. |
vendor_relay_ip
|
10.1.2.3 |
keyword |
IP address of the local relay used to send a message. |
vendor_relay_host
|
graylog.com |
keyword |
Hostname of the local relay used to send a message. |
source_ip
|
10.1.2.3 |
keyword |
IP address of the client relay, the host from which a connection was received. |
source_hostname
|
graylog.com |
keyword |
Hostname of the client relay, the host from which a connection was received. |
| Invalid Connection | |||
vendor_relay_user
|
suspicious@domain.tld | keyword | User of the client relay, the host from which the invalid connection was received. |
vendor_relay_warning
|
may be forged | keyword | Warning that relay IP or name may be forged. |
source_ip
|
10.1.2.3 | keyword | IP address of the client relay, the host from which the invalid connection was received. |
source_hostname
|
domain.tld | keyword | Hostname of the client relay, the host from which the invalid connection was received. |
| Pre-greet Traffic | |||
vendor_event_action
|
rejecting | keyword | The action taken in the event. |
vendor_relay_user
|
suspicious@domain.tld | keyword | User of the client relay, the host from which the pre-greeting traffic was sent. |
vendor_relay_warning
|
may be forged | keyword | Warning that relay IP or name may be forged. |
source_ip
|
10.1.2.3 | keyword | IP address of the client relay, the host from which the pre-greeting traffic was sent. |
source_hostname
|
domain.tld | keyword | Hostname of the client relay, the host from which the pre-greeting traffic was sent. |
| Rejected Discovery | |||
vendor_relay_user
|
suspicious@domain.tld | keyword | User of the client relay, the host potentially scanning the server. |
vendor_relay_warning
|
may be forged | keyword | Warning that relay IP or name may be forged. |
source_ip
|
10.1.2.3 |
keyword |
IP address of the client relay, the host potentially scanning the server. |
source_hostname
|
domain.tld |
keyword |
Hostname of the client relay, the host potentially scanning the server. |
| Service Status | |||
vendor_event_action
|
starting | keyword | The event action indicating the status of the Sendmail daemon. |
vendor_version
|
8.14.7 | keyword | The Sendmail version running. |
vendor_event_outcome_reason
|
signal | keyword | The specific cause for a service status change. |
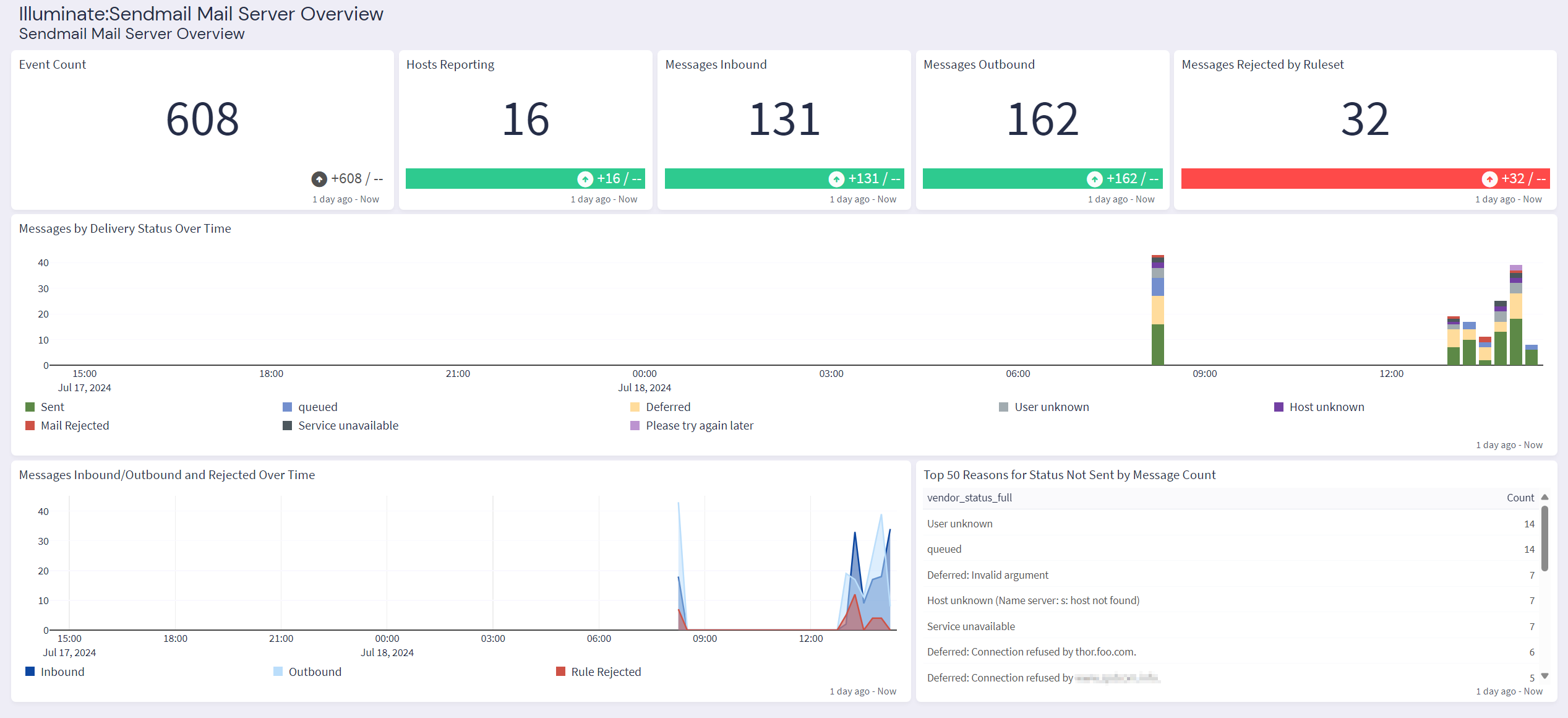
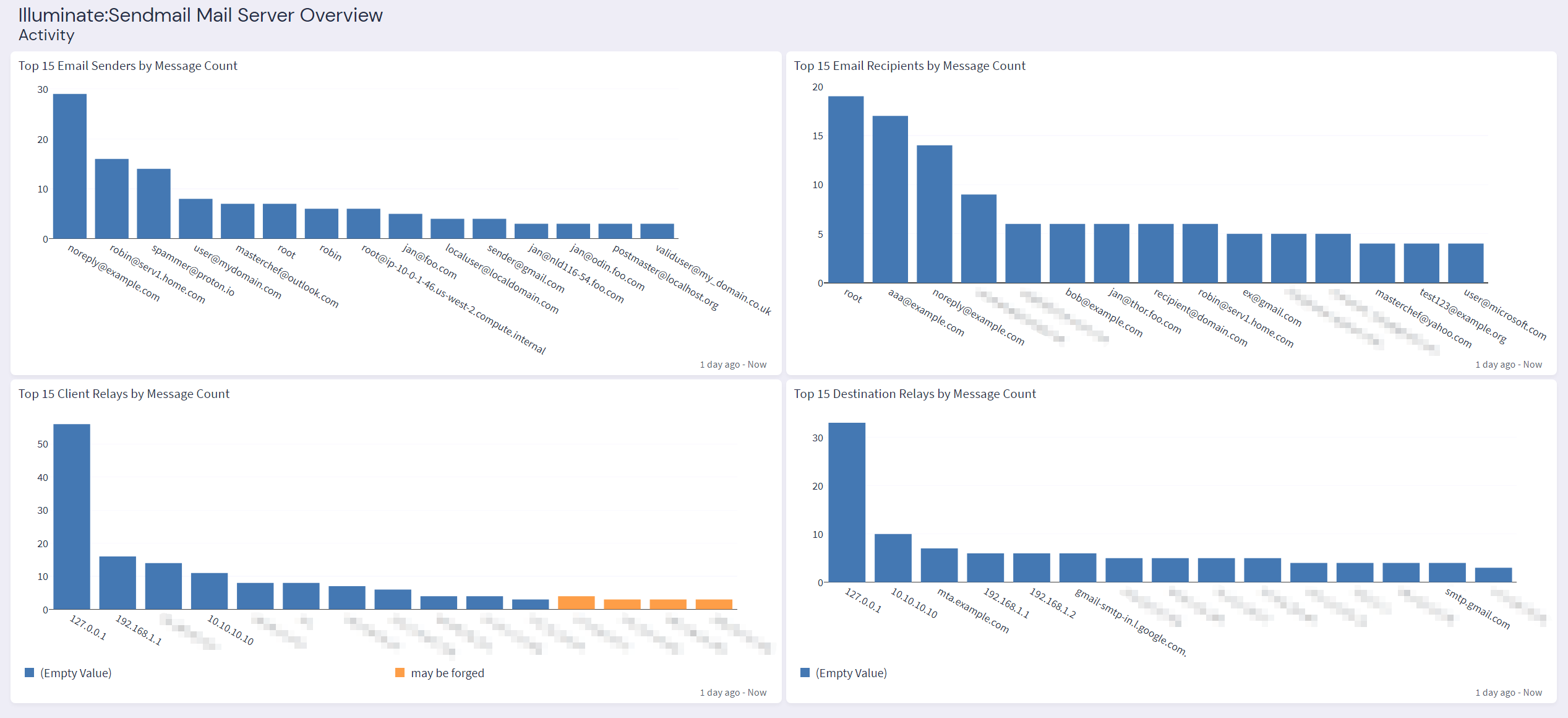
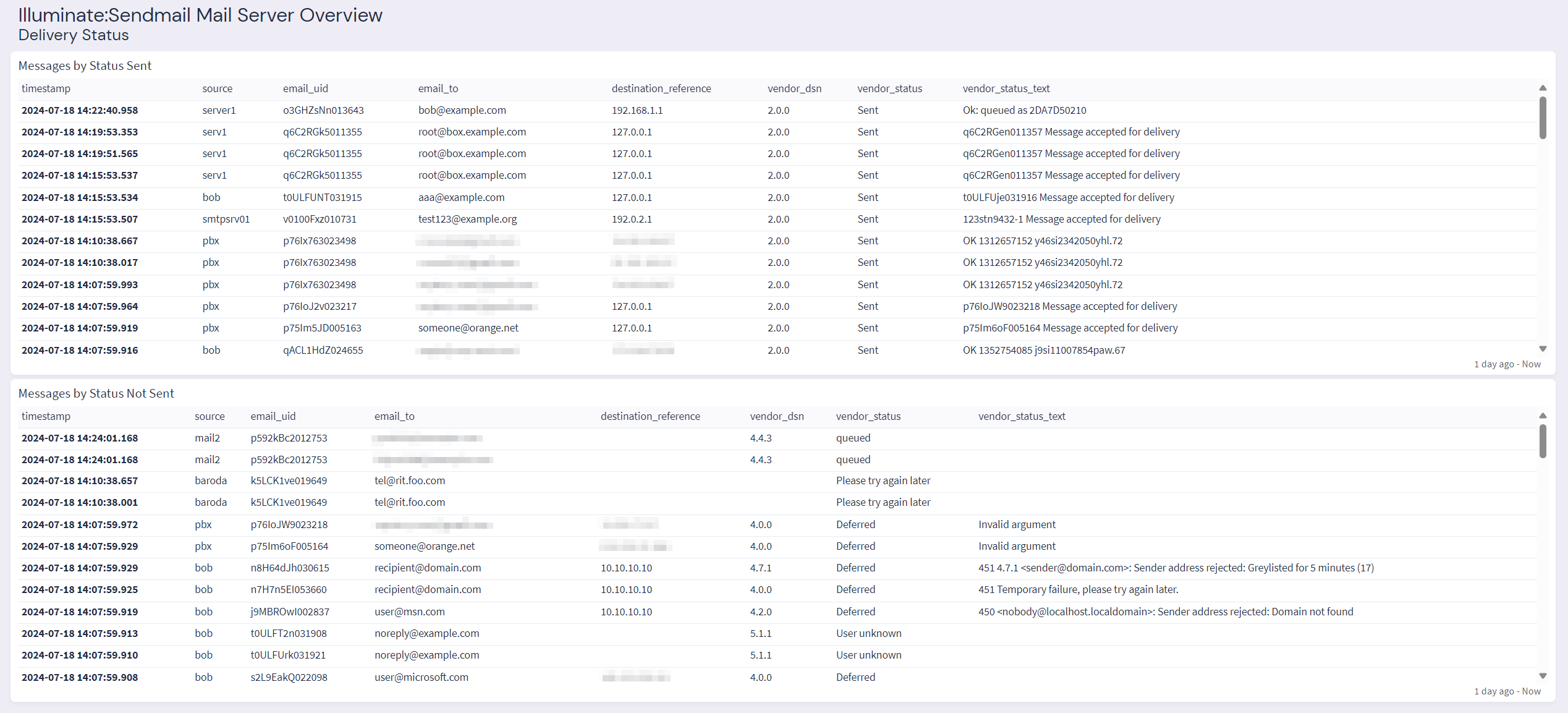
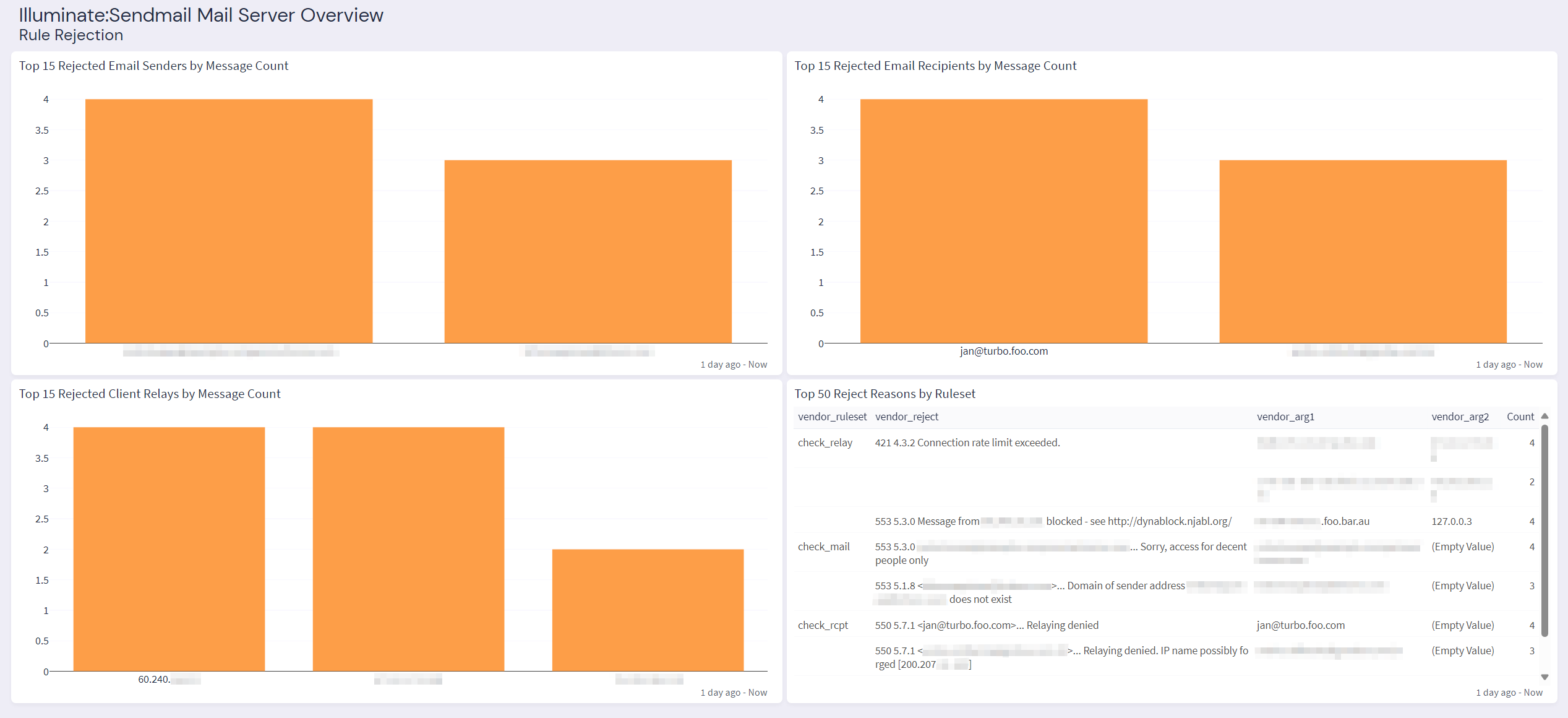
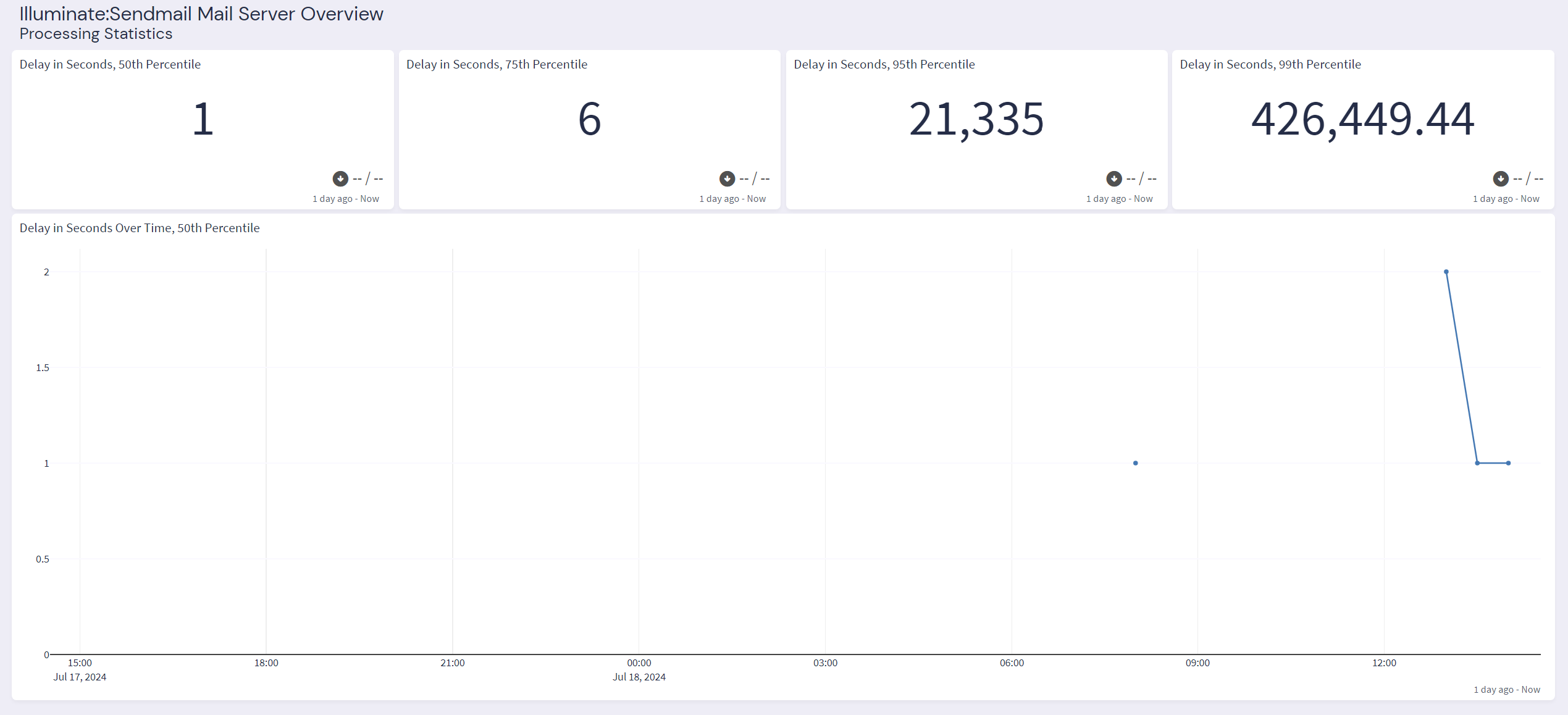
Graylog Illuminate:Sendmail Spotlight Content Pack
The Graylog "Illuminate:Sendmail Spotlight" offers a dashboard with 6 tabs: Sendmail Mail Server Overview, Activity, Delivery Status, Rule Rejection, Authentication, and Processing Statistics.