ProFTPD Server Content Pack
The ProFTPD Server content pack is designed to extract, normalize, and enrich ProFTPD event data for more effective analysis and monitoring. It parses default logs and enhanced logs into structured fields and adds useful context like event categorization (e.g. authentication and file events). This parsing and normalization enables faster search, correlation, and dashboard creation across diverse environments.
Supported Versions
This pack was constructed to work with both standard and enhanced logs.
Custom log formats are not supported.
-
ProFTPD 1.3.9
-
ProFTPD 1.3.8d
Log Collection and Delivery
This pack is designed to collect ProFTPD logs delivered via Syslog via the local Rsyslog service. See the ProFTPD Project Documentation site for configuration details. Fine-tune log types via Syslog Facility or Loglevel, if necessary. The application_name has to be proftpd.
Beta support: Filebeat.
-
Syslog
-
Filebeat (Beta)
Example: Rsyslog Configuration
-
Create a matching Syslog input in Graylog.
-
Configure rsyslog to send logs under e.g.
/var/log/proftpd/*.logto Graylog. -
If needed, create a custom template that identifies the logs as ProFTPD logs for the parser to recognize.
-
ProFTPD messages with the field
application_nameand the valueproftpdwill get parsed. Graylog's syslog input should parse out these fields.
(Example) Filebeat Configuration
-
Please refer to the official documentation to set up Graylog Sidecar for Filebeat.
-
Create a matching Beats input in Graylog.
-
Ensure that the option Do not add Beats type as prefix is disabled.
-
Create an API access token and custom Linux Filebeat collector.
-
Configure the collector to ship messages in syslog and auth.log to Graylog. The Filebeat input must add the field
event_source_product: proftpdfor the parser to identify the log source as ProFTPD. -
Set the option
fields_under_roottotrue. This step is also necessary for message identification to work. See the following example:Copy- input_type: log
paths:
- /var/log/proftpd/*.log # adjust the paths accordingly to your settings
- /var/log/proftpd/proftpd.log
type: filestream
fields_under_root: true
fields:
event_source_product: proftpd -
Install Graylog Sidecar on the client host.
-
Edit the Graylog Sidecar client configuration with your Graylog server API URL and API access token.
Requirements
-
Graylog 6.2.0+ with a valid Enterprise license
Stream Configuration
This technology pack includes 1 stream:
- Illuminate:ProFTPD FTP Server Messages
Index Set Configuration
This technology pack includes 1 index set definition:
- ProFTPD FTP Server Logs
Log Format Example
These are normal and enhanced ProFTPD example logs.
ProFTPD Logs
Oct 20 10:06:03 ftp01 proftpd[24523]: 10.0.0.15 (remote01[10.0.0.15]) - USER bob: Login successful.
Oct 20 10:06:03 ftp01 proftpd[24523]: USER bob: Login successful.
Oct 20 10:10:34 ftp01 proftpd[24688]: 192.168.10.55 (client01[192.168.10.55]) - USER alice (Login failed): Incorrect password.
Oct 20 10:10:34 ftp01 proftpd[24688]: USER alice (Login failed): Incorrect password.
Oct 20 10:35:22 ftp01 proftpd[24567]: 192.168.1.10 (client.example.com[192.168.1.10]) - FTP session opened.
Oct 20 10:35:22 ftp01 proftpd[24567]: 192.168.1.10 (client.example.com[192.168.1.10]) - STOR /uploads/test.txt
Oct 20 10:35:22 ftp01 proftpd[24567]: 192.168.1.10 (client.example.com[192.168.1.10]) - RETR /downloads/manual.pdf
Oct 20 10:35:22 ftp01 proftpd[24567]: 192.168.1.10 (client.example.com[192.168.1.10]) - FTP session closed.
Oct 20 14:53:50 ftpserver proftpd[24123]: STOR /uploads/manual.pdf 1048576 226
Oct 20 14:53:50 ftpserver proftpd[24123]: STOR /uploads/manual.pdf
Oct 20 14:53:50 ftpserver proftpd[24123]: Connection from client.example.com [10.0.0.5] opened.
Oct 20 14:53:50 ftpserver proftpd[24123]: Connection from client.example.com [10.0.0.5] closed.
Oct 20 14:53:50 ftpserver proftpd[24123]: Connection from crawl-googlebot.com [26.249.66.80] denied.
Oct 20 14:53:50 ftpserver proftpd[24123]: Connection from 192.168.1.10 [192.168.1.10] refused.
Oct 20 14:53:50 ftpserver proftpd[24123]: Connection from 203.0.113.9 [20.0.113.9] rejected.
Oct 20 14:53:50 ftpserver proftpd[24123]: Connection from 10.1.1.5 [10.1.1.5] timed out.
Oct 20 14:53:50 ftpserver proftpd[24123]: Connection from 10.1.1.5 [10.1.1.5] dropped.
Oct 20 14:53:50 ftpserver proftpd[24123]: Connection from 10.0.0.5 [10.0.0.5] terminated.
Oct 20 14:53:50 ftpserver proftpd[24123]: Connection from 10.0.0.5 [10.0.0.5] lost.
Oct 20 14:53:50 ftpserver proftpd[24123]: Connection from 10.0.0.5 [10.0.0.5] deferred.
Oct 20 14:53:50 ftpserver proftpd[24123]: mod_ban/0.9.2: banning client <20.51.100.17> after 5 failed attempts within 60 seconds.
Oct 20 14:53:50 ftpserver proftpd[24123]: mod_ban/0.9.2: unbanning client <20.51.100.17>.
Oct 20 14:53:50 ftpserver proftpd[24123]: Maximum number of clients (50) reached, refusing connection from 10.0.0.50.
Oct 20 14:53:50 ftpserver proftpd[24123]: Maximum number of connections (100) reached, denying connection from 192.0.2.15.
Oct 20 14:53:50 ftpserver proftpd[24123]: Maximum number of users (200) reached, refusing connection from 203.0.113.22
What Is Provided
-
Rules to parse, normalize, and enrich ProFTPD log messages
-
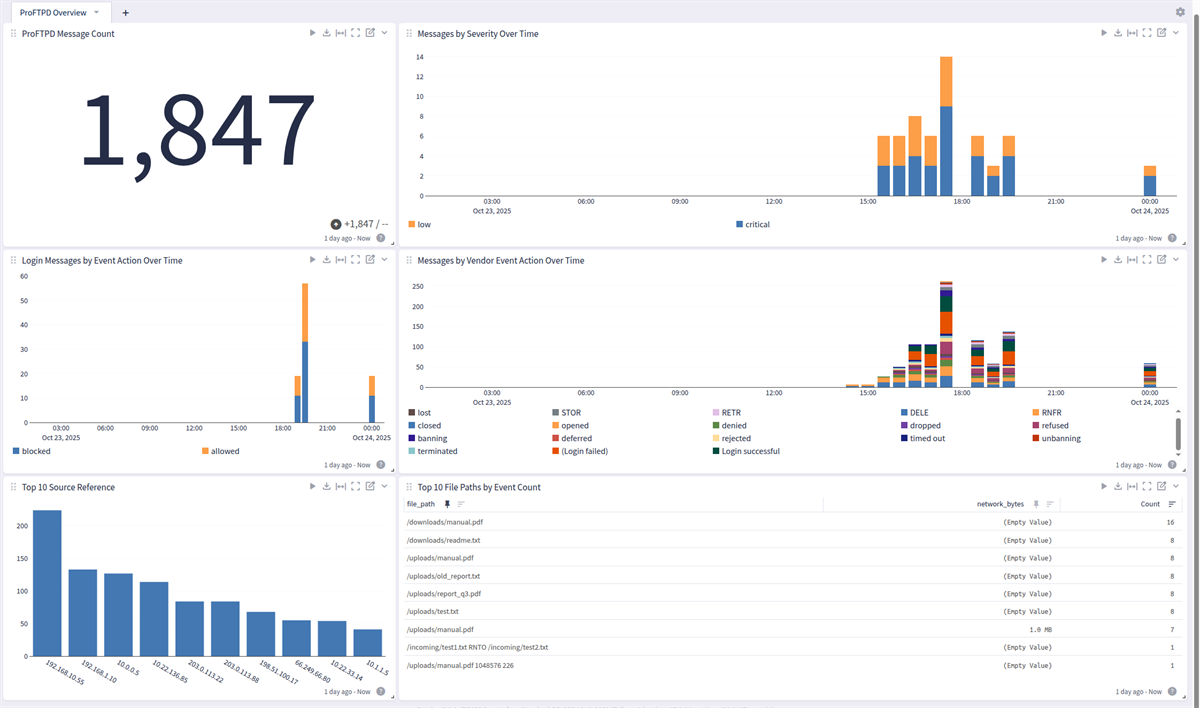
A ProFTPD Overview Dashboard that delivers an at-a-glance summary of key events.
GIM Categorization
In most cases, ProFTPD messages are categorized based on the Vendor Event Action field, but some log types are generic and we might use a different method to categorize them.
GIM categorization is provided for the following messages:
| Vendor Event Action | GIM Category | GIM Subcategory | GIM Event Type |
|---|---|---|---|
| STOR | file | file.default | file event |
| RETR | file | file.default | file event |
| DELE | file | file.default | file event |
| RNFR | file | file.default | file event |
| RNTO | file | file.default | file event |
| Login successful | authentication | authentication.default | authentication message |
| (Login failed) | authentication | authentication.default | authentication message |
Message Fields Included in This Pack
General Parsing
This pack applies normalization to standard and enhanced ProFTPD logs. Additionally, it shortens the "message." Exiting headers and enhanced headers are parsed but dropped to reduce license utilization.
Attached are the most common parsed fields for ProFTPD logs.
| Fields | Example Value |
|---|---|
| application_name | proftpd |
| destination_hostname | ProFTPD Server DESTINATION_NOT_SET |
| event_action | allowed |
| event_outcome | success |
| event_source_product | proftpd |
| file_name | manual.pdf |
| file_path | /uploads/manual.pdf |
| host_hostname | ftp01 |
| network_bytes | 1048576 |
| process_id | 24512 |
| source_hostname | client01 |
| source_ip | 192.168.10.55 |
| source_ip_inner | 192.168.10.55 |
| user_name | alice |
| vendor_event_action | Login successful |
| vendor_event_created | Oct 20 10:05:42 |
| vendor_event_outcome | successful |
| vendor_event_outcome_reason | Incorrect password. |
| vendor_ftp_status_code | 226 |
ProFTPD Server Content Pack
This spotlight offers a dashboard with 1 tab:
Overview