Palo Alto is a next-generation firewall that provides real-time (line-rate, low-latency) content scanning to protect users against malicious attacks that include viruses, spyware, data leakage, and application vulnerabilities based on a stream-based threat prevention engine. This technology pack will process Palo Alto logs, providing normalization and enrichment of common events of interest.
Supported Version(s)
- PAN-OS 11.1+
Requirements
- Graylog Server 6.1.0+ with a valid Enterprise license
- Palo Alto Device(s) sending Logs to the Palo Alto 11.x input on the Graylog system
Stream Configuration
This technology pack includes 1 stream:
- "Illuminate:Palo Alto Messages"
If you were previously using the Palo Alto 9.x pack with Illuminate, this pack will use the same stream.
Index Set Configuration
This technology pack includes 1 index set definition:
- "Palo Alto Logs"
Log Collection
Palo Alto Device Logging Configuration
Configure your device(s) following the instructions in the Palo Alto logging guide using TCP as the transport and the format "BSD."
Log Processing
The Illuminate pack for Palo Alto 11.x will rename some common fields to all Palo Alto logs but primarily processes the following log types:
- Config
- Decryption
- GlobalProtect
- HIP Match
- System
- Threat
- Traffic
- User-ID
Palo Alto Logs and CSV Processing
Illuminate processes Palo Alto logs in CSV format. A common issue arises when newer versions of PAN-OS introduce additional fields.
To handle these gracefully, this pack captures the extra fields in placeholder fields prefixed with additional_field_, followed by a letter corresponding to the field’s position.
Letters a through x are used to represent these additional columns. These placeholders are temporary and will be replaced with properly labeled fields in a future release of the pack.
IP Field Processing
Palo Alto devices have distinct fields for device IPv4 and IPv6 addresses. When one of these values is not present, it will log that field with the value 0.0.0.0.
Illuminate will reassign the IPv6 address to the appropriate IP field: source_ip, host_ip, or destination_ip.
If both IPv4 and IPv6 values are defined (e.g. not assigned the value 0.0.0.0), then no changes will be made to the field assignments.
Field Normalization
The Illuminate pack for Palo Alto will normalize fields common fields from all logs. The normalized common fields are in the following table:
| Palo Alto Field | Illuminate Field |
|---|---|
Receive Time
|
event_received_time
|
Serial Number
|
event_observer_uid
|
Type
|
vendor_subtype
|
Threat/Content Type
|
vendor_log_subtype
|
Generated Time
|
vendor_event_created
|
Illuminate will prune these common fields from the beginning of the message field value. The message value examples below, in the per-log type sections, will show the complete Palo Alto log message in the examples, but note that these will appear differently in Graylog due to the common fields being removed. Additionally, some message values may be overwritten by either vendor-provided descriptive text or by brief message summaries generated by Illuminate. This is done in an effort to reduce the overall size of the message due to the message data existing in both the original event and in the normalized fields. A description of the modification to the message field will be done on a per-log type basis in the sections below. Additional fields will be normalized from Palo Alto log messages based on the log type.
In order to have the full, unmodified message value from the Palo Alto device stored in Graylog, enable the option Store full message? on the Palo Alto 11 input.
Config Logs
Log Format Example
1,2024/10/04 03:46:00,,CONFIG,0,2816,2024/10/04 03:46:00,172.16.14.19,,commit,admin,Web,Submitted,,7421534605078953992,0x0,0,0,0,0,,PA-VM,0,,0,2024-10-04T03:46:00.050-07:00
Normalized Fields
| Palo Alto Fields | Illuminate Fields |
|---|---|
Host
|
host_ip or host_hostname |
Virtual System
|
host_virtfw_id
|
Command
|
user_command
|
Admin
|
user_name
|
Client
|
vendor_signin_protocol
|
Result
|
vendor_event_action
|
Configuration Path
|
user_command_path
|
Sequence Number
|
event_uid
|
Action Flags
|
vendor_log_panorama
|
Device Group Hierarchy Level 1
|
vendor_dev_group_level_1
|
Device Group Hierarchy Level 2
|
vendor_dev_group_level_2
|
Device Group Hierarchy Level 3
|
vendor_dev_group_level_3
|
Device Group Hierarchy Level 4
|
vendor_dev_group_level_4
|
Virtual System Name
|
host_virtfw_hostname
|
Device Name
|
event_observer_hostname
|
Device Group
|
device_group
|
Audit Comment
|
vendor_audit_comment
|
High Resolution Timestamp
|
event_created
|
Decryption Logs
Log Format Example
1,2024/11/28 04:39:15,007954000533467,DECRYPTION,0,2817,2024/11/28 04:39:15,172.16.16.11,198.51.100.20,172.16.14.28,198.51.100.20,LAN_WAN,,,web-browsing,vsys1,LAN_Zone,WAN_Zone,ethernet1/1,ethernet1/3,Licen_PA,2024/11/28 04:39:15,593,1,49984,443,12874,443,0x1400000,tcp,allow,N/A,,,,,b8b30cde-a128-468c-a1ca-69fc9cd04b22,Finished,Finished,TLS1.2,ECDHE,AES_256_GCM,SHA384,Test SSL Decryption,secp384r1,None,trusted,Trusted,Forward,01e3ae440d35ca7bc34,d8d8858803dacbb6b9002a070297eeaf0269380972364ba09e518ebe3676fa88,2024/11/12 16:00:00,2025/05/13 16:59:59,V3,2048,14,30,23,14,:::::RSA,login.live.com,DigiCert SHA2 Secure Server CA,DigiCert Global Root CA,login.live.com,,,,,,,,,2024-11-28T04:39:15.985-08:00,,,,,,,,,,,,,,,,,7442296184930041891,0x0,0,0,0,0,,PA-VM,1,internet-utility,general-internet,browser-based,4,\"used-by-malware,able-to-transfer-file,has-known-vulnerability,tunnel-other-application,pervasive-use\",,web-browsing,no,no,
Normalized Fields
| Palo Alto Fields | Illuminate Fields |
|---|---|
Source Address
|
source_ip
|
Destination Address
|
destination_ip
|
NAT Source IP
|
source_nat_ip
|
NAT Destination IP
|
destination_nat_ip
|
Rule
|
rule_name
|
Source User
|
user_name
|
Destination User
|
destination_user_name
|
Application
|
application_name
|
Virtual System
|
host_virtfw_id
|
Source Zone
|
source_zone
|
Destination Zone
|
destination_zone
|
Inbound Interface
|
network_interface_in
|
Outbound Interface
|
network_interface_out
|
Log Action
|
vendor_logging_profile
|
Time Logged
|
time_received
|
Session ID
|
session_id
|
Repeat Count
|
event_repeat_count
|
Source Port
|
source_port
|
Destination Port
|
destination_port
|
NAT Source Port
|
source_nat_port
|
NAT Destination Port
|
destination_nat_port
|
Flags
|
vendor_flags
|
IP Protocol
|
network_transport
|
Action
|
vendor_event_action
|
Tunnel
|
tunnel
|
FUTURE_USE
|
future_use_1
|
FUTURE_USE
|
future_use_2
|
Source VM UUID
|
source_vsys_uuid
|
Destination VM UUID
|
destination_vsys_uuid
|
UUID for rule
|
rule_uuid
|
Stage for Client to Firewall
|
hs_stage_c2f
|
Stage for Firewall to Server
|
hs_stage_f2s
|
TLS Version
|
crypto_protocol_version
|
Key Exchange Algorithm
|
tls_keyxchg
|
Encryption Algorithm
|
tls_enc
|
Hash Algorithm
|
tls_auth
|
Policy Name
|
policy_name
|
Elliptic Curve
|
ec_curve
|
Error Index
|
err_index
|
Root Status
|
root_status
|
Chain Status
|
chain_status
|
Proxy Type
|
proxy_type
|
Certificate Serial Number
|
crypto_certificate_serial_number
|
Fingerprint
|
fingerprint
|
Certificate Start Date
|
crypto_certificate_activation_time
|
Certificate End Date
|
crypto_certificate_expiration_time
|
Certificate Version
|
crypto_certificate_version
|
Certificate Size
|
cert_size
|
Common Name Length
|
cn_len
|
Issuer Common Name Length
|
crypto_certificate_issuer_len
|
Root Common Name Length
|
rootcn_len
|
SNI Length
|
sni_len
|
Certificate Flags
|
cert_flags
|
Subject Common Name
|
cn
|
Issuer Subject Common Name
|
crypto_certificate_issuer
|
Root Subject Common Name
|
root_cn
|
Server Name Indication
|
sni
|
Error
|
event_error_description
|
Container ID
|
container_id
|
POD Namespace
|
container_namespace
|
POD Name
|
container_name
|
Source External Dynamic List
|
vendor_src_edl
|
Destination External Dynamic List
|
vendor_dst_edl
|
Source Dynamic Address Group
|
vendor_src_dag
|
Destination Dynamic Address Group
|
vendor_dst_dag
|
High Res Timestamp
|
event_created
|
Source Device Category
|
source_category
|
Source Device Profile
|
vendor_source_profile
|
Source Device Model
|
source_device_model
|
Source Device Vendor
|
source_device_vendor
|
Source Device OS Family
|
source_os_name
|
Source Device OS Version
|
source_os_version
|
Source Hostname
|
source_hostname
|
Source Mac Address
|
source_mac
|
Destination Device Category
|
destination_category
|
Destination Device Profile
|
vendor_destination_profile
|
Destination Device Model
|
destination_device_model
|
Destination Device Vendor
|
destination_device_vendor
|
Destination Device OS Family
|
destination_os_name
|
Destination Device OS Version
|
destination_os_version
|
Destination Hostname
|
destination_hostname
|
Destination Mac Address
|
destination_mac
|
Sequence Number
|
event_uid
|
Action Flags
|
vendor_log_panorama
|
Device Group Hierarchy Level 1
|
vendor_dev_group_level_1
|
Device Group Hierarchy Level 2
|
vendor_dev_group_level_2
|
Device Group Hierarchy Level 3
|
vendor_dev_group_level_3
|
Device Group Hierarchy Level 4
|
vendor_dev_group_level_4
|
Virtual System Name
|
host_virtfw_hostname
|
Device Name
|
event_observer_hostname
|
Virtual System ID
|
host_virtfw_uid
|
Application Subcategory
|
application_subcategory
|
Application Category
|
application_category
|
Application Technology
|
application_technology
|
Application Risk
|
application_risk
|
Application Characteristic
|
application_characteristic
|
Application Container
|
application_container
|
Application SaaS
|
application_is_saas
|
Application Sanctioned State
|
application_sanctioned_state
|
Cluster Name
|
cluster_name
|
Flow Type
|
flow_type
|
GlobalProtect Logs
Log Format Example
1,2024/11/27 11:45:44,007954000533467,GLOBALPROTECT,0,2817,2024/11/27 11:45:44,vsys1,gateway-config-release,configuration,,,test,172.16.0.0-172.31.255.255,DESKTOP-FNV6TE0,172.16.14.19,0.0.0.0,192.168.40.1,0.0.0.0,23fd01a8-11d4-44cd-8be9-774d7e1b68a5,6ZVJD02,6.3.1,Windows,\"Microsoft Windows 10 Pro , 64-bit\",1,,,,success,,0,,0,Test GP GW,7441913159746584601,0x0,2024-11-27T11:45:46.019-08:00,,,,,,0,0,0,0,,PA-VM,1,
Normalized Fields
| Palo Alto Fields | Illuminate Fields |
|---|---|
Virtual System
|
host_virtfw_id
|
Event ID
|
vendor_event_name
|
Stage
|
vendor_tunnel_stage
|
Authentication Method
|
vendor_auth_method
|
Tunnel Type
|
network_tunnel_type
|
Source User
|
user_name
|
Source Region
|
vendor_source_region
|
Machine Name
|
source_hostname or source_ip |
Public IP
|
source_ip
|
Public IPv6
|
source_ipv6
|
Private IP
|
source_nat_ip
|
Private IPv6
|
source_nat_ipv6
|
Host ID
|
vendor_gp_hostid
|
Serial Number
|
source_id
|
Client Version
|
vendor_gp_client_version
|
Client OS
|
source_os_name
|
Client OS Version
|
source_os_version
|
Repeat Count
|
event_repeat_count
|
Reason
|
vendor_gp_reason
|
Error
|
event_error_description
|
Description
|
vendor_gp_error_extended
|
Status
|
vendor_event_outcome
|
Location
|
vendor_gp_location_name
|
Login Duration
|
network_tunnel_duration
|
Connect Method
|
vendor_gp_connect_method
|
Error Code
|
event_error_code
|
Portal
|
destination_hostname
|
Sequence Number
|
event_uid
|
Action Flags
|
vendor_log_panorama
|
High Res Timestamp
|
event_created
|
Selection Type
|
vendor_selection_type
|
Response Time
|
application_response_time
|
Priority
|
vendor_gateway_priority
|
Attempted Gateways
|
vendor_attempted_gateways
|
Gateway
|
vendor_gateway
|
Device Group Hierarchy Level 1
|
vendor_dev_group_level_1
|
Device Group Hierarchy Level 2
|
vendor_dev_group_level_2
|
Device Group Hierarchy Level 3
|
vendor_dev_group_level_3
|
Device Group Hierarchy Level 4
|
vendor_dev_group_level_4
|
Virtual System Name
|
host_virtfw_hostname
|
Device Name
|
event_observer_hostname
|
Virtual System ID
|
host_virtfw_uid
|
Cluster Name
|
cluster_name
|
HIP Match Logs
Log Format Example
1,2024/11/27 11:45:02,007954000533467,HIPMATCH,0,2817,2024/11/27 11:45:02,test,vsys1,DESKTOP-FNV6TE0,Windows,192.168.40.1,Test_HIP,1,object,,,7441913164041551873,0x0,0,0,0,0,,PA-VM,1,0.0.0.0,23fd01a8-11d4-44cd-8be9-774d7e1b68a5,6ZVJD02,,2024-11-27T11:45:03.231-08:00,
Normalized Fields
| Palo Alto Fields | Illuminate Fields |
|---|---|
Source User
|
user_name
|
Virtual System
|
host_virtfw_id
|
Machine Name
|
host_hostname
|
Operating System
|
host_type
|
Source Address
|
host_ip
|
HIP
|
vendor_hipmatch_name
|
Repeat Count
|
event_repeat_count
|
HIP Type
|
vendor_hipmatch_type
|
Sequence Number
|
event_uid
|
Action Flags
|
vendor_log_panorama
|
Device Group Hierarchy Level 1
|
vendor_dev_group_level_1
|
Device Group Hierarchy Level 2
|
vendor_dev_group_level_2
|
Device Group Hierarchy Level 3
|
vendor_dev_group_level_3
|
Device Group Hierarchy Level 4
|
vendor_dev_group_level_4
|
Virtual System Name
|
host_virtfw_hostname
|
Device Name
|
event_observer_hostname
|
Virtual System ID
|
host_virtfw_uid
|
IPv6 Source Address
|
host_ipv6
|
Host ID
|
vendor_gp_hostid
|
User Device Serial Number
|
host_id
|
Device MAC Address
|
source_mac
|
High Resolution Timestamp
|
event_created
|
Cluster Name
|
cluster_name
|
System Logs
Log Format Example
1,2024/10/08 12:04:25,,SYSTEM,general,2816,2024/10/08 12:04:25,,general,,0,0,general,informational,\"Connection to Update server: updates.paloaltonetworks.com completed successfully, initiated by 172.16.14.40\",7421534605078955497,0x0,0,0,0,0,,PA-VM,0,0,2024-10-08T12:04:25.668-07:00
Normalized Fields
| Palo Alto Fields | Illuminate Fields |
|---|---|
Virtual System
|
host_virtfw_id
|
Event ID
|
vendor_event_name
|
Object
|
vendor_event_object
|
Module
|
vendor_module
|
Severity
|
event_severity
|
Description
|
message
|
Sequence Number
|
event_uid
|
Action Flags
|
vendor_log_panorama
|
Device Group Hierarchy Level 1
|
vendor_dev_group_level_1
|
Device Group Hierarchy Level 2
|
vendor_dev_group_level_2
|
Device Group Hierarchy Level 3
|
vendor_dev_group_level_3
|
Device Group Hierarchy Level 4
|
vendor_dev_group_level_4
|
Virtual System Name
|
host_virtfw_hostname
|
Device Name
|
event_observer_hostname
|
High Resolution Timestamp
|
event_created
|
message using the summary message from the Palo Alto source field Description.
Threat Logs
Log Format Example
1,2024/12/18 03:45:54,007954000533467,THREAT,virus,2817,2024/12/18 03:45:54,172.16.16.11,89.238.73.97,172.16.14.28,89.238.73.97,LAN_WAN,,,web-browsing,vsys1,LAN_Zone,WAN_Zone,ethernet1/1,ethernet1/3,Licen_PA,2024/12/18 03:45:54,307,1,49878,443,39152,443,0x1402000,tcp,reset-server,\"eicar.com\",Eicar Test File(100000),any,medium,server-to-client,7449709697914896384,0x0,172.16.0.0-172.31.255.255,Germany,,,0,,,1,,,,,,,,0,0,0,0,0,,PA-VM,,,,,0,,0,,N/A,js,Antivirus-5010-5528,0x0,0,4294967295,,,b8b30cde-a128-468c-a1ca-69fc9cd04b22,0,,,,,,,,,,,,,,,,,,,,,,,,,,,,,0,2024-12-18T03:45:54.944-08:00,,,,internet-utility,general-internet,browser-based,4,\"used-by-malware,able-to-transfer-file,has-known-vulnerability,tunnel-other-application,pervasive-use\",,web-browsing,no,no,,,NonProxyTraffic
Normalized Fields
| Palo Alto Fields | Illuminate Fields |
|---|---|
Source Address
|
source_ip
|
Destination Address
|
destination_ip
|
NAT Source IP
|
source_nat_ip
|
NAT Destination IP
|
destination_nat_ip
|
Rule Name
|
rule_name
|
Source User
|
source_user_name
|
Destination User
|
destination_user_name
|
Application
|
application_name
|
Virtual System
|
host_virtfw_id
|
Source Zone
|
source_zone
|
Destination Zone
|
destination_zone
|
Inbound Interface
|
network_interface_in
|
Outbound Interface
|
network_interface_out
|
Log Action
|
vendor_logging_profile
|
Session ID
|
session_id
|
Repeat Count
|
event_repeat_count
|
Source Port
|
source_port
|
Destination Port
|
destination_port
|
NAT Source Port
|
source_nat_port
|
NAT Destination Port
|
destination_nat_port
|
Flags
|
vendor_flags
|
IP Protocol
|
network_transport
|
Action
|
vendor_event_action
|
URL/Filename
|
alert_indicator
|
Threat ID
|
alert_signature
|
Category
|
event_category
|
Severity
|
vendor_alert_severity
|
Direction
|
vendor_alert_direction
|
Sequence Number
|
event_uid
|
Action Flags
|
vendor_log_panorama
|
Source Location
|
source_location_name
|
Destination Location
|
destination_location_name
|
Content Type
|
http_content_type
|
PCAP_ID
|
vendor_pcap_id
|
File Digest
|
vendor_wildfire_hash
|
Cloud
|
vendor_cloud_hostname
|
URL Index
|
vendor_url_index
|
User Agent
|
http_user_agent_name
|
File Type
|
file_type
|
X-Forwarded-For
|
http_xff
|
Referer
|
http_referrer
|
Sender
|
source_user_email
|
Subject
|
email_subject
|
Recipient
|
target_user_email
|
Report ID
|
vendor_wildfire_report_id
|
Device Group Hierarchy Level 1
|
vendor_dev_group_level_1
|
Device Group Hierarchy Level 2
|
vendor_dev_group_level_2
|
Device Group Hierarchy Level 3
|
vendor_dev_group_level_3
|
Device Group Hierarchy Level 4
|
vendor_dev_group_level_4
|
Virtual System Name
|
host_virtfw_hostname
|
Device Name
|
event_observer_hostname
|
Source VM UUID
|
source_vsys_uuid
|
Destination VM UUID
|
destination_vsys_uuid
|
HTTP Method
|
http_method
|
Tunnel ID/IMSI
|
vendor_tunnel_id
|
Monitor Tag/IMEI
|
vendor_monitor_tag
|
Parent Session ID
|
vendor_parent_session_id
|
Parent Start Time
|
vendor_parent_start_time
|
Tunnel Type
|
network_tunnel_type
|
Threat Category
|
vendor_threat_category
|
Content Version
|
alert_definitions_version
|
SCTP Association ID
|
vendor_assoc_id
|
SCTP Chunks
|
vendor_sctp_chunks_sum
|
SCTP Chunks Sent
|
vendor_sctp_chunks_tx
|
SCTP Chunks Received
|
vendor_sctp_chunks_rx
|
Rule UUID
|
policy_uid
|
HTTP/2 Connection
|
vendor_http2
|
Dynamic User Group Name
|
vendor_dynusergroup_name
|
XFF Address
|
http_xff_address
|
Source Device Category
|
source_category
|
Source Device Profile
|
vendor_source_profile
|
Source Device Model
|
source_device_model
|
Source Device Vendor
|
source_device_vendor
|
Source Device OS Family
|
source_os_name
|
Source Device OS Version
|
source_os_version
|
Source Hostname
|
source_hostname
|
Source MAC Address
|
source_mac
|
Destination Device Category
|
destination_category
|
Destination Device Profile
|
vendor_destination_profile
|
Destination Device Model
|
destination_device_model
|
Destination Device Vendor
|
destination_device_vendor
|
Destination Device OS Family
|
destination_os_name
|
Destination Device OS Version
|
destination_os_version
|
Destination Hostname
|
destination_hostname
|
Destination MAC Address
|
destination_mac
|
Container ID
|
container_id
|
POD Namespace
|
container_namespace
|
POD Name
|
container_name
|
Source External Dynamic List
|
vendor_src_edl
|
Destination External Dynamic List
|
vendor_dst_edl
|
Host ID
|
vendor_host_id
|
Serial Number
|
vendor_host_sn
|
Domain EDL
|
vendor_domain_edl
|
Source Dynamic Address Group
|
vendor_src_dag
|
Destination Dynamic Address Group
|
vendor_dst_dag
|
Partial Hash
|
vendor_partial_hash
|
High Resolution Timestamp
|
event_created
|
Reason
|
vendor_event_outcome_reason
|
Justification
|
vendor_event_justification
|
A Slice Service Type
|
vendor_nsdsai_sst
|
Application Subcategory
|
application_subcategory
|
Application Category
|
application_category
|
Application Technology
|
application_technology
|
Application Risk
|
application_risk_level
|
Application Characteristic
|
application_characteristic
|
Application Container
|
application_container
|
Tunneled Application
|
tunneled_app
|
Application SaaS
|
application_is_saas
|
Application Sanctioned State
|
application_sanctioned_state
|
Cloud Report ID
|
cloud_reportid
|
Cluster Name
|
cluster_name
|
Flow Type
|
flow_type
|
Illuminate will overwrite the message field for threat logs, normally the CSV-formatted event data, into a more brief summary of the event in question.
The replacement message uses the template PAN:{vendor_subtype}:{vendor_log_subtype} - {alert signature}:{alert_indicator} - source_ip:{source_ip} destination_ip:{destination_ip} - {vendor_event_action}.
For example: PAN:THREAT:spyware - Grayware:s.uuidksinc.net:s.uuidksinc.net - source_ip:172.16.16.11 destination_ip:198.51.100.20 - drop.
Traffic Logs
Log Format Example
1,2024/10/03 00:38:31,,TRAFFIC,end,2816,2024/10/03 00:38:31,172.16.16.11,172.16.14.40,172.16.14.28,172.16.14.40,LAN-WAN,,,ping,vsys1,LAN_Zone,WAN_Zone,ethernet1/1,ethernet1/3,Traffic_log1,2024/10/03 00:38:31,16,4,0,0,0,0,0x500019,icmp,allow,592,296,296,8,2024/10/03 00:38:15,0,any,,7421447455897550886,0x0,172.16.0.0-172.31.255.255,172.16.0.0-172.31.255.255,,4,4,aged-out,0,0,0,0,,PA-VM,from-policy,,,0,,0,,N/A,0,0,0,0,1c467ae3-1dd7-4dd3-976e-c2e6d98e7cc2,0,0,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,2024-10-03T00:38:31.407-07:00,,,internet-utility,general-internet,network-protocol,2,\"has-known-vulnerability,tunnel-other-application,pervasive-use\",,untunneled,no,no,0,NonProxyTraffic,
Normalized Fields
| Palo Alto Fields | Illuminate Fields |
|---|---|
Source Address
|
source_ip
|
Destination Address
|
destination_ip
|
NAT Source IP
|
source_nat_ip
|
NAT Destination IP
|
destination_nat_ip
|
Rule Name
|
rule_name
|
Source User
|
user_name
|
Destination User
|
destination_user_name
|
Application
|
application_name
|
Virtual System
|
host_virtfw_id
|
Source Zone
|
source_zone
|
Destination Zone
|
destination_zone
|
Inbound Interface
|
network_interface_in
|
Outbound Interface
|
network_interface_out
|
Log Action
|
vendor_logging_profile
|
Session ID
|
session_id
|
Repeat Count
|
event_repeat_count
|
Source Port
|
source_port
|
Destination Port
|
destination_port
|
NAT Source Port
|
source_nat_port
|
NAT Destination Port
|
destination_nat_port
|
Flags
|
vendor_flags
|
IP Protocol
|
network_transport
|
Action
|
vendor_event_action
|
Bytes
|
network_bytes
|
Bytes Sent
|
source_bytes_sent
|
Bytes Received
|
destination_bytes_sent
|
Packets
|
network_packets
|
Start Time
|
event_start
|
Elapsed Time
|
event_duration
|
Category
|
http_uri_category
|
Sequence Number
|
event_uid
|
Action Flags
|
vendor_log_panorama
|
Source Country
|
source_location_name
|
Destination Country
|
destination_location_name
|
Packets Sent
|
source_packets_sent
|
Packets Received
|
destination_packets_sent
|
Session End Reason
|
vendor_session_end_reason
|
Device Group Hierarchy Level 1
|
vendor_dev_group_level_1
|
Device Group Hierarchy Level 2
|
vendor_dev_group_level_2
|
Device Group Hierarchy Level 3
|
vendor_dev_group_level_3
|
Device Group Hierarchy Level 4
|
vendor_dev_group_level_4
|
Virtual System Name
|
host_virtfw_hostname
|
Device Name
|
event_observer_hostname
|
Action Source
|
vendor_event_description
|
Source VM UUID
|
source_vsys_uuid
|
Destination VM UUID
|
destination_vsys_uuid
|
Rule UUID
|
rule_uuid
|
Stage for Client to Firewall
|
hs_stage_c2f
|
Stage for Firewall to Server
|
hs_stage_f2s
|
TLS Version
|
crypto_protocol_version
|
Key Exchange Algorithm
|
tls_keyxchg
|
Encryption Algorithm
|
tls_enc
|
Hash Algorithm
|
tls_auth
|
Policy Name
|
policy_name
|
Elliptic Curve
|
ec_curve
|
Error Index
|
err_index
|
Root Status
|
root_status
|
Chain Status
|
chain_status
|
Proxy Type
|
proxy_type
|
Certificate Serial Number
|
crypto_certificate_serial_number
|
Fingerprint
|
fingerprint
|
Certificate Start Date
|
notbefore
|
Certificate End Date
|
notafter
|
Certificate Version
|
crypto_certificate_version
|
Certificate Size
|
cert_size
|
Common Name Length
|
cn_len
|
Issuer Common Name Length
|
crypto_certificate_issuer_len
|
Root Common Name Length
|
rootcn_len
|
SNI Length
|
sni_len
|
Certificate Flags
|
cert_flags
|
Subject Common Name
|
cn
|
Issuer Subject Common Name
|
crypto_certificate_issuer
|
Root Subject Common Name
|
root_cn
|
Server Name Indication
|
sni
|
Error
|
event_error_description
|
Container ID
|
container_id
|
POD Namespace
|
container_namespace
|
POD Name
|
container_name
|
Source External Dynamic List
|
vendor_src_edl
|
Destination External Dynamic List
|
vendor_dst_edl
|
Source Dynamic Address Group
|
vendor_src_dag
|
Destination Dynamic Address Group
|
vendor_dst_dag
|
High Res Timestamp
|
event_created
|
Source Device Category
|
source_category
|
Source Device Profile
|
vendor_source_profile
|
Source Device Model
|
source_device_model
|
Source Device Vendor
|
source_device_vendor
|
Source Device OS Family
|
source_os_name
|
Source Device OS Version
|
source_os_version
|
Source Hostname
|
source_hostname
|
Source Mac Address
|
source_mac
|
Destination Device Category
|
destination_category
|
Destination Device Profile
|
vendor_destination_profile
|
Destination Device Model
|
destination_device_model
|
Destination Device Vendor
|
destination_device_vendor
|
Destination Device OS Family
|
destination_os_name
|
Destination Device OS Version
|
destination_os_version
|
Destination Hostname
|
destination_hostname
|
Destination Mac Address
|
destination_mac
|
Container ID
|
container_id
|
POD Namespace
|
container_namespace
|
POD Name
|
container_name
|
Source External Dynamic List
|
vendor_src_edl
|
Destination External Dynamic List
|
vendor_dst_edl
|
Source Dynamic Address Group
|
vendor_src_dag
|
Destination Dynamic Address Group
|
vendor_dst_dag
|
Host ID
|
vendor_host_id
|
Serial Number
|
vendor_host_sn
|
Source Dynamic Address Group
|
vendor_src_dag
|
Destination Dynamic Address Group
|
vendor_dst_dag
|
Session Owner
|
vendor_session_owner
|
High Resolution Timestamp
|
event_created
|
A Slice Service Type
|
vendor_nsdsai_sst
|
A Slice Differentiator
|
vendor_nsdsai_sd
|
Application Subcategory
|
application_subcategory
|
Application Category
|
application_category
|
Application Technology
|
application_technology
|
Application Risk
|
application_risk
|
Application Characteristic
|
application_characteristic
|
Application Container
|
application_container
|
Tunneled Application
|
tunneled_app
|
Application SaaS
|
application_is_saas
|
Application Sanctioned State
|
application_sanctioned_state
|
Offloaded
|
offloaded
|
Flow Type
|
flow_type
|
Cluster Name
|
cluster_name
|
Illuminate will overwrite the "message" field for traffic logs, normally the CSV-formatted event data, into a more brief summary of the event in question. The replacement message uses the template {network_protocol}/{vendor_event_action} {source_ip}:{source_port}->{destination_ip}:{destination_port}.
For example: allow/udp 198.51.100.20:52491->192.0.2.10:443
User-ID Logs
Log Format Example
1,2024/11/27 11:45:44,007954000533467,USERID,logout,2817,2024/11/27 11:45:44,vsys1,192.168.40.1,test,,0,1,0,0,0,vpn-client,globalprotect,7441913164041551877,0x0,0,0,0,0,,PA-VM,1,,2024/11/27 11:45:46,1,0x0,test,,2024-11-27T11:45:46.015-08:00,,client-to-server,
Normalized Fields
| Palo Alto Fields | Illuminate Fields |
|---|---|
Virtual System
|
host_virtfw_id
|
Source IP
|
source_ip
|
User
|
user_name*
|
Data Source Name
|
vendor_datasource_name
|
Event ID
|
vendor_event_name
|
Repeat Count
|
event_repeat_count
|
Time Out Threshold
|
vendor_timeout
|
Source Port
|
source_port
|
Destination Port
|
destination_port
|
Data Source
|
vendor_datasource
|
Data Source Type
|
vendor_datasource_type
|
Sequence Number
|
event_uid
|
Action Flags
|
vendor_log_panorama
|
Device Group Hierarchy Level 1
|
vendor_dev_group_level_1
|
Device Group Hierarchy Level 2
|
vendor_dev_group_level_2
|
Device Group Hierarchy Level 3
|
vendor_dev_group_level_3
|
Device Group Hierarchy Level 4
|
vendor_dev_group_level_4
|
Virtual System Name
|
host_virtfw_hostname
|
Device Name
|
event_observer_hostname
|
Virtual System ID
|
host_virtfw_uid
|
Factor Type
|
vendor_factor_type
|
Factor Completion Time
|
vendor_factor_completion_time
|
Factor Number
|
vendor_factor_number
|
User Group Flags
|
vendor_user_group_flags
|
User by Source
|
user_name_by_source*
|
Tag Name
|
tag_name
|
High Resolution Timestamp
|
event_created
|
Origin Data Source
|
origin_data_source
|
Cluster Name
|
cluster_name
|
User was extracted as source_user, and User by Source was extracted as vendor_source_user.
Illuminate will overwrite the message field for User ID logs (normally the CSV-formatted event data) into a more brief summary of the event in question.
The replacement message uses the template User-ID:{user_name} discovery:{vendor_log_subtype}, data source:{vendor_datasource} (name:{vendor_datasource_name}, type:{vendor_datasource_type}).
For example, User-ID:corpuser discovery:login, data source:agent (name:CORPSYS1, type:).
Enrichments
Illuminate will enrich events with data to make working with events easier.
application_risk
Some Palo Alto logs will include a numeric risk-scoring value, assigned to the field application_risk_level for logged applications, on a scale of 1 (lowest) to 5 (highest). Illuminate also adds the field application_risk_score, which will provide a text value that reflects the rating of the numeric risk score.
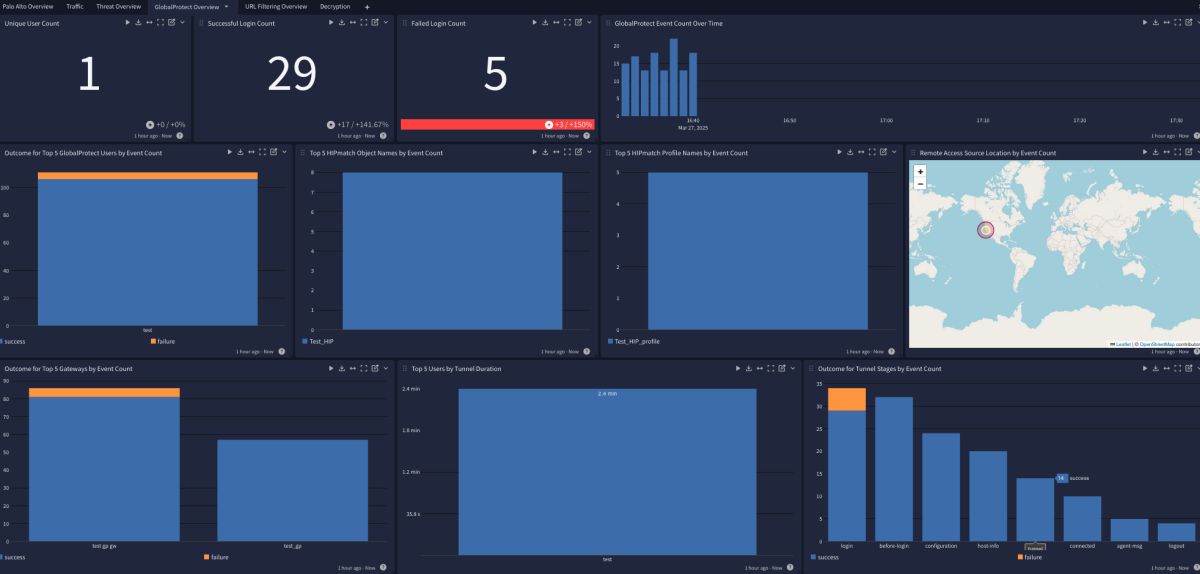
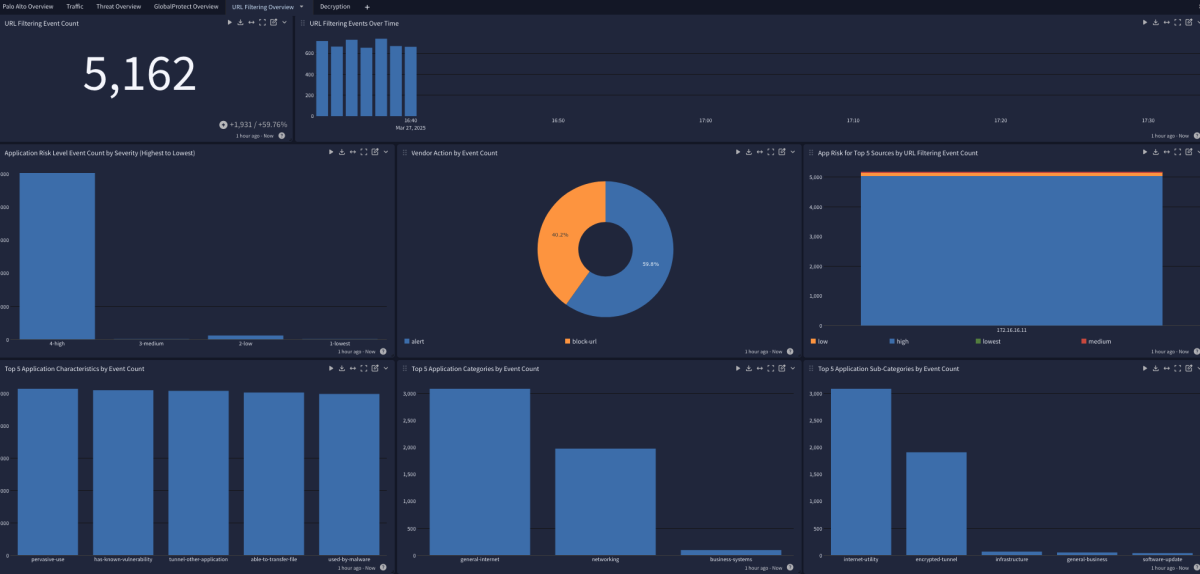
Palo Alto 11 Spotlight Content Pack
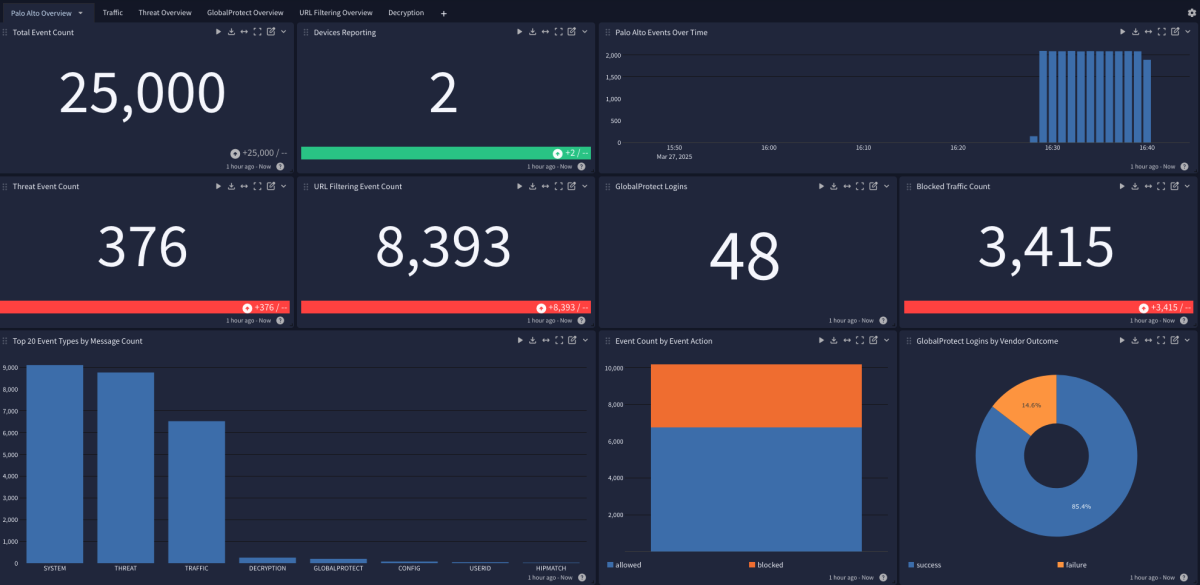
The Palo Alto 11 Spotlight Pack offers an overview dashboard with the following tabs:
Overview
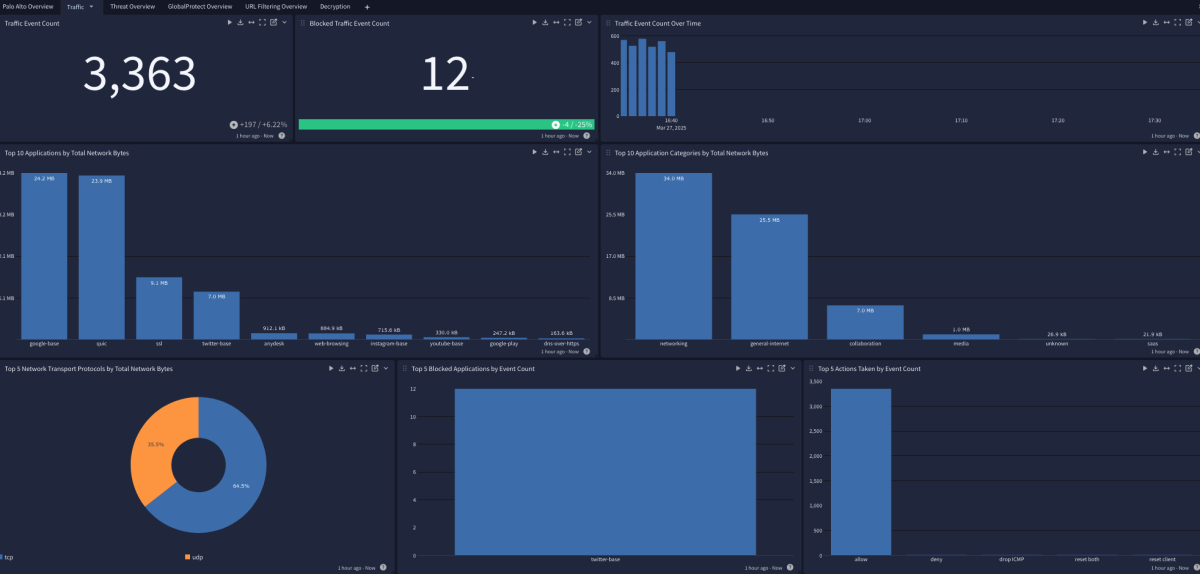
Traffic
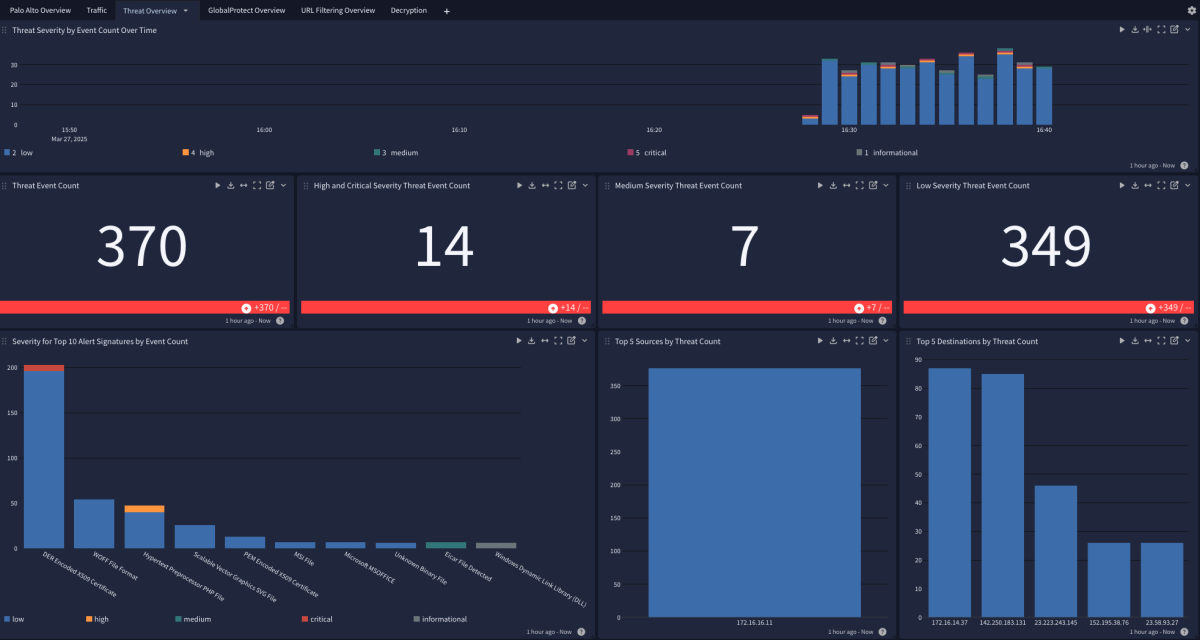
Threat
Global Protect
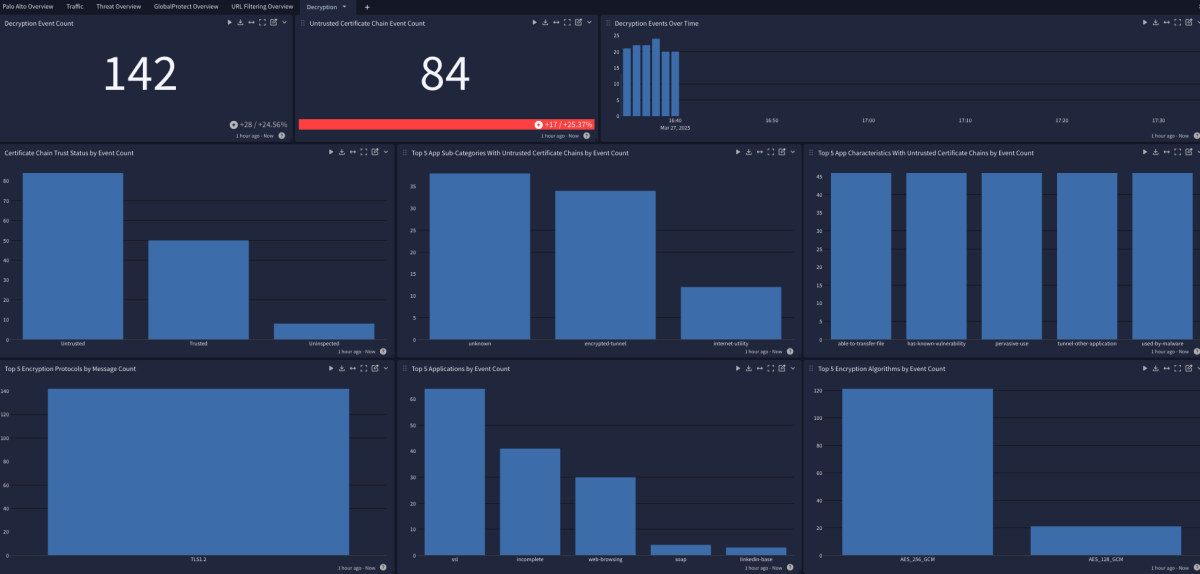
URL Filtering
Decryption