Mimecast is a cloud-based cyber security provider specializing in email security and offering protection against phishing, malware, spam, and data leaks. It also delivers services for archiving, continuity, and threat intelligence to help organizations secure their communications and ensure compliance.
Supported Versions
-
Mimecast API 2.0
Requirements
-
Graylog 6.2.3+ with a valid Enterprise license
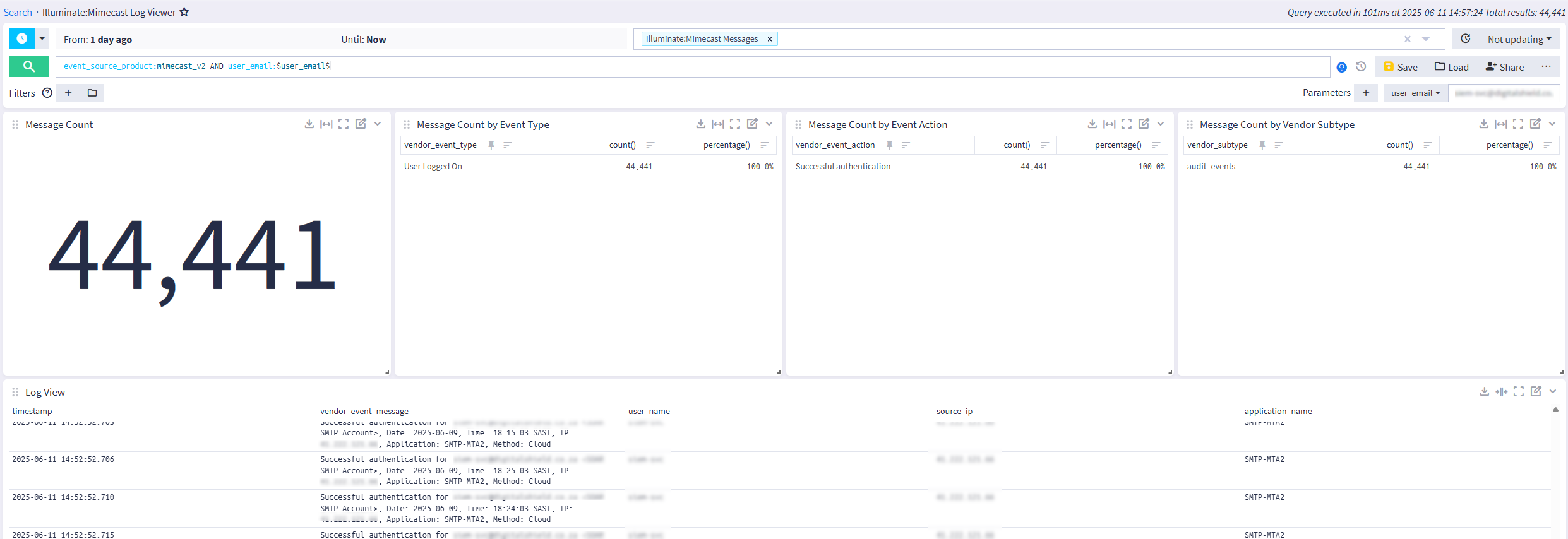
Stream Configuration
This technology pack includes 1 stream:
- "Illuminate:Mimecast Messages"
Index Set Configuration
This technology pack includes 1 index set definition:
- "Mimecast Logs"
Log Collection
Mimecast utilizes the Mimecast input that ingests multiple Mimecast content types in JSON format. See the Graylog documentation for information on how to launch a new Mimecast input.
Configuration Example
Log Format Example
This is a generic log representing the typical JSON format of Mimecast logs.
General Logs
{"id":"eNoVzt0KgjAAQOF32e0EdWrNoIvZn6UGYZKKNzqHWaai2y4Wv","auditType":"User Logged On","user":"user@domain.com","eventTime":"2025-06-12T14:53:56+0000","eventInfo":"Successful authentication for user@domain.com <Domain User>, Date: 2025-06-12, Time: 16:53:56 SAST, IP: 192.168.100.100, Application: SMTP-MTA2, Method: Cloud","category":"authentication_logs"}
What is Provided
-
Rules to parse, normalize, and enrich Mimecast content pack messages.
-
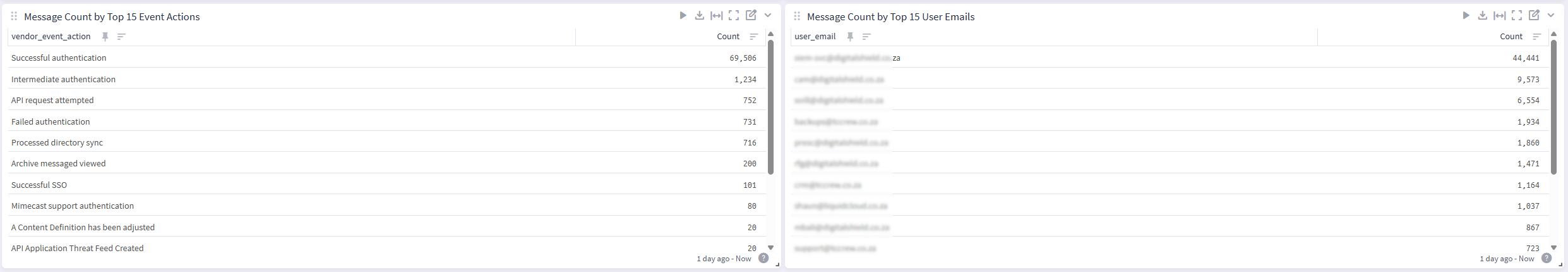
A dashboard displaying events and statistics of interest.
-
Saved search highlighting key information using a
user_emailparameter.
Events Processed by This Technology Pack
The content pack supports the following log types. Generic processing will be provided for log types not listed.
-
User Logged On
-
Unauthorized API Request
-
Case Action
-
Review Set Action
-
Discovery Case Adjustments
-
Logon Authentication Failed
-
Logon Requires Challenge
-
Completed Directory Sync
-
New Policy
-
Existing Policy Changed
-
Mimecast Support Login
-
Content Definition Adjustments
-
Existing Route Changed
-
New Delivery Route
-
Profile Group (Address) Log Entry
-
Account Updated
-
API Application Created
-
User Password Changed
-
User Settings Updated
-
User Locked
GIM Categorization
GIM categorization is provided for the following messages:
| Log Type | GIM Category | GIM Subcategory | GIM Event Type Code |
|---|---|---|---|
| User Locked | iam | iam.object disable | 111500 |
| User Settings Updated | iam | iam.object modify | 111000 |
| User Password Changed | iam | iam.object modify | 111004 |
Message Fields Included in This Pack
Field of Note
| Field Name | Example Value | Field Type | Description |
|---|---|---|---|
application_name
|
SMTP-MTA2 | keyword | Application extracted from 'Application' reference from .eventInfo in JSON body |
destination_ip
|
8.8.8.8 | ip | Destination IP associated with the event pulled from 'Remote IP' from .eventInfo in JSON body |
destination_port
|
25 | long | Destination port extracted from .eventInfo in JSON body |
email_from
|
person@domain | keyword | Extracted from .from in JSON body |
email_subject
|
Test Message | keyword | Extracted from .subject in JSON body |
email_to
|
another_person@domain.com | keyword | Extracted from .to in JSON body |
event_created
|
2025-06-13T14:30:03+0000 | date | Timestamp extracted from .eventTime or .viewed in JSON body |
event_source
|
JvuS6F0rQmdeSSqcrF8xSAA1BFbYC1Lqkk1A5 | keyword | The client_id set in the Mimecast v2 input |
event_source_product
|
mimecast_v2 | keyword | Created via input. This will always be the same. |
event_uid
|
JvuVUt30eqQpG3S6F0rQmdeSSqc | keyword | Extracted from .id in the JSON body. |
source_ip
|
192.168.1.100 | ip | Source IP that generated the activity. Extracted from 'IP' from .eventInfo in JSON body |
user_domain
|
example.com | keyword | Extracted domain from user related e-mail's in JSON body |
user_email
|
person@domain.com | keyword | Extracted user e-mail from JSON body |
user_email_display_name
|
Random Person | keyword | The display name extracted from .eventInfo in JSON body |
user_name
|
person | keyword | Multi-value field containing all user_name references in full JSON body |
vendor_email_content_viewed_flag
|
false | keyword | Extracted from .contentViewed in JSON body |
vendor_email_date
|
2025-05-30T10:10:32+0000 | date | Extracted from .messageDate in JSON body |
vendor_email_discovery_case_flag
|
true | keyword | Extracted from discoverCase in JSON body |
vendor_event_action
|
Successful Authentication | keyword | Vendor's event action reference extracted from .eventInfo in JSON body |
vendor_event_category
|
authentication_logs | keyword | Extracted from .category in JSON body |
vendor_event_message
|
Successful authentication for person@domain.com <SMTP Account>, Date: 2025-06-13, Time: 16:30:03 SAST, IP: 192.168.1.1, Application: SMTP-MTA2, Method: Cloud | keyword | Full .eventInfo from JSON body |
vendor_event_method
|
Cloud | keyword | Extracted from 'Method' reference from .eventInfo in JSON body |
vendor_event_type
|
User Logged On | keyword | Event type extracted from .auditType in JSON body |
vendor_subtype
|
audit_events | keyword | Created via input and associated configuration |
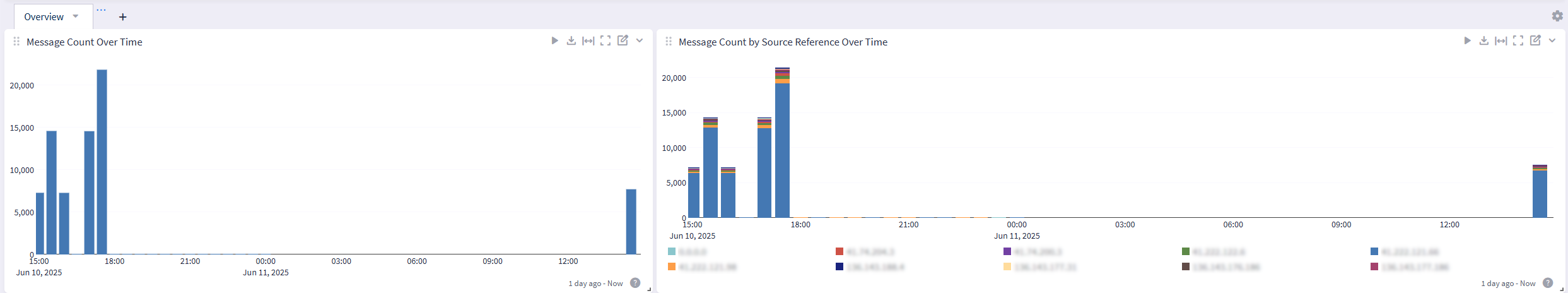
Mimecast Spotlight Content Pack
This spotlight offers a dashboard with an Overview tab and a saved search tied to the user_name parameter:
Overview
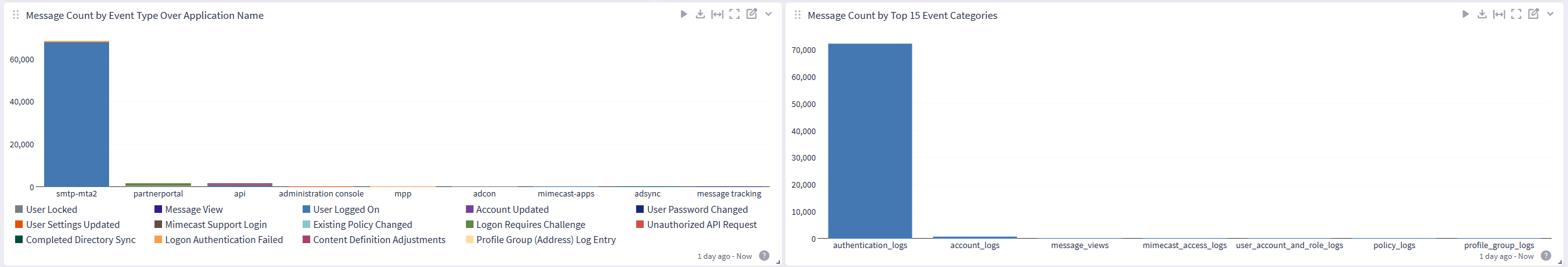
Saved Search