DHCP is a network protocol used to assign IP addresses and other network configuration parameters dynamically to devices on a network. Microsoft provides DHCP server software as a component of its Windows Server operating system.
The Microsoft DHCP server is designed to manage the automatic assignment of IP addresses to client devices on a network, reducing the need for manual configuration of each device and helping to ensure a consistent and correct IP addressing scheme. The DHCP server can be managed through the Microsoft management console, making it easy to administer and configure.
This technology pack provides processing for Microsoft DHCP server event logs collected with the filebeat agent.
Supported Versions
-
Supported versions are Windows 2016, 2019, and 2022.
Requirements
-
Windows DHCP server
-
Graylog Server with a valid Enterprise license, running Graylog version 4.3 or later
-
Configure Filebeat to send Microsoft DHCP server(s) logs to Graylog server beats input
Log Collection
The DHCP activity log can be read in a text-based editor and is stored in the C:\Windows\System32\DHCP folder. A log is created for each day of the week and named.
Filebeat Setup
Filebeat is a lightweight log shipper that can be used to send logs from a Windows server to a remote logging system like Graylog.
1. Install Filebeat
Download and install Filebeat for Windows from elastic.co. Choose the required version and download the ZIP file. Follow the installation instructions for Filebeat.
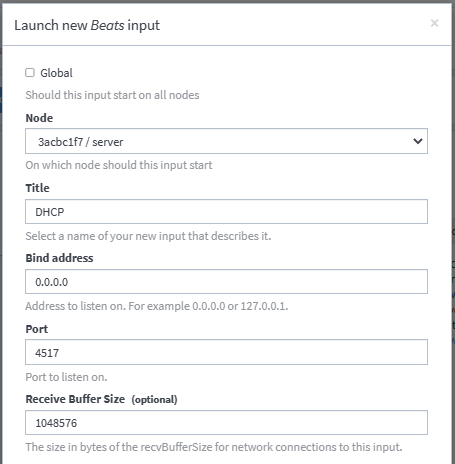
2. Create An Input Page in Graylog
-
Create a Beats input under System/Inputs in Graylog with the desired port number.
-
Name and save the input. Make sure input status is running.
3. Configure Filebeat
Configure Filebeat to collect DHCP logs. Edit the Filebeat configuration file (filebeat.yml) to specify the location of the DHCP logs and any other desired settings. In this file, you'll also need to specify the Graylog output for Filebeat to send the logs to.
-
In our case below, under “paths,” we added this line to fetch all the files in the folder:
C:\Windows\System32\dhcp\*
-
The “ fields” portion is mandatory as this is the field that Graylog will focus on to direct the logs into the correct stream.
We have provided a sample filebeat.yml file that will send your logs from your DHCP server to Graylog, allowing for them to be fully imported and parsed. The following yaml file shows the minimum required sections for a yml file running DHCP. You may choose to add to the file but both sections (inputs and output) need to be present.
# ============================== Filebeat inputs ===============================
filebeat.inputs:
# Each - is an input. Most options can be set at the input level, so
# you can use different inputs for various configurations.
# Below are the input specific configurations.
# filestream is an input for collecting log messages from files.
- type: filestream
# Unique ID among all inputs, an ID is required.
id: <my-filestream-id>
# Change to true to enable this input configuration.
enabled: true
# Paths that should be crawled and fetched. Glob based paths.
paths:
- <path_to_log_file>
# Set the event_source_product field to microsoftdhcp
fields:
event_source_product: microsoft_dhcp
fields_under_root: true
○ Output.logstash
# ------------------------------ Logstash Output -------------------------------
output.logstash:
# The Graylog host IP and beats input
hosts: ["<your_graylog_ip>:5044"]Starting Filebeat
Start Filebeat as a service on the Windows server to begin collecting and sending the DHCP logs. To do this you can open a command and enter the following command:
Start-Service filebeat
Once that is running, enter this command to start sending logs to Graylog:
.\filebeat.exe -c filebeat.yml
You should now see your logs coming into your Graylog server and being successfully parsed.
Stream Configuration
This technology pack includes one stream:
-
“Illuminate:Windows Event Log Messages”
Index Set Configuration
This technology pack includes one index set definition:
-
"Windows Event Log Messages”
Log Format Example
12,01/30/23,15:27:28,Release,192.168.1.11,DESKTOP-P423Q1J,C025A54DB363,,3451374721,0,,,,,,,,,0
What is Provided
-
Parsing rules to normalize and enrich Microsoft DHCP log messages.
-
We support the following event IDs:
| Event ID | Description |
|---|---|
| 00 | The log was started. |
| 01 | The log was stopped. |
| 02 | The log was temporarily paused due to low disk space. |
| 10 | A new IP address was leased to a client. |
| 11 | A lease was renewed by a client. |
| 12 | A lease was released by a client. |
| 13 | An IP address was found to be in use on the network. |
| 14 | A lease request could not be satisfied because the scope's address pool was exhausted. |
| 15 | A lease was denied. |
| 16 | A lease was deleted. |
| 17 | A lease was expired and DNS records for an expired leases have not been deleted. |
| 18 | A lease was expired, and DNS records were deleted. |
| 20 | A BOOTP address was leased to a client. |
| 21 | A dynamic BOOTP address was leased to a client. |
| 22 | A BOOTP request could not be satisfied because the scope's address pool for BOOTP was exhausted. |
| 23 | A BOOTP IP address was deleted after checking to see it was not in use. |
| 24 | IP address cleanup operation has begun. |
| 25 | IP address cleanup statistics. |
| 30 | DNS update request to the named DNS server. |
| 31 | DNS update failed. |
| 32 | DNS update successful. |
| 33 | Packet dropped due to NAP policy. |
| 34 | DNS update request failed as the DNS update request queue limit exceeded. |
| 35 | DNS update request failed. |
| 36 | Packet dropped because the server is in failover standby role or the hash of the client ID does not match. |
| 50+ | Codes above 50 are used for Rogue Server Detection information. |
Events Processed by This Technology Pack
The Microsoft DHCP content pack supports DHCP leasing events, parsing for all fields, and GIM categorization for the lease events: Release, Renew, and Assign.

