The following content pack is available for use with a Graylog Illuminate license and Graylog Enterprise or Graylog Security. Contact sales to learn more about obtaining Illuminate.
The Linux AuditD Processing Pack is designed to extract, normalize, and enrich AuditD event data for more effective analysis and monitoring. It parses raw kernel audit logs into structured fields and adds useful context such as event categorization (e.g. authentication). This enables faster search, correlation, and analysis across diverse environments.
Supported Distributions
This pack was constructed to work with both Red Hat Enterprise Linux (RHEL) 9.5 and Ubuntu 24.04; however, most recent versions (Ubuntu 18+, RHEL 8+) of Linux that have AuditD installed or available in the official repositories should be supported.
The AuditD service must be a version that supports "enriched" logging.
There are subtle differences in the log contents and events generated across different Linux distributions and versions. As a result, there may be differences in how events are categorized between the different distributions based on which event types are generated by a given release of Linux and AuditD.
-
Ubuntu 24.04
-
Red Hat Enterprise Linux (RHEL) 9.5
Requirements
-
Graylog 6.1.3+ with a valid Enterprise license
Stream Configuration
This technology pack includes 1 stream:
- Illuminate:Linux AuditD Messages
Index Set Configuration
This technology pack includes 1 index set definition:
- Linux AuditD Logs
What is Provided
-
Rules to parse, normalize, and enrich Linux AuditD system log messages
-
An AuditD Overview dashboard that delivers an at-a-glance summary of key security events and the status of AuditD logging activity.
Log Collection and Delivery
This article will provide an Rsyslog message template and configuration for sending the AuditD logs to Graylog and the configuration that will enable AuditD to send audit events to the local syslog service.
After forwarding, Rsyslog will drop the events to prevent them from being written to disk; the AuditD service will have already written these logs to the audit log file.
Rsyslog Configuration
Before implementing the provided configuration it is important to review your current Rsyslog configuration and, if necessary, adjust the provided instructions to avoid any possible conflicts with your existing configuration.
While the example below presents a single configuration file, your system may split Rsyslog settings across multiple files, for example, loading modules and defining templates separately. Analyzing and understanding your Rsyslog configuration prior to implementing changes to your logging configuration will ensure your system logging continues to function properly.
The provided Rsyslog configuration is defined with the expectation that AuditD will use the syslog logging facility local6 with a severity of info. If any other application is using this, you must adjust all references to local6 and info, both in the Rsyslog and AuditD configurations, to use a facility and severity that is otherwise unused on your system(s).
Additionally, Graylog uses the Rsyslog module mmutf8fix to sanitize AuditD logs. On some systems the AuditD "enriched" logs include UTF8 "group separator" characters that may not render properly in Graylog.
-
Verify a TCP syslog input is defined on your Graylog systems, or create a new input following the Graylog documentation.
-
Create the file
/etc/rsyslog .d/60-graylog.confand add the following configuration, customizing to match your local system logging if necessaryCopymodule(load="mmutf8fix")
template(
name="custom_linux_syslog_5424"
type="string"
string="<%PRI%>1 %TIMESTAMP:::date-rfc3339% %HOSTNAME% %APP-NAME% %PROCID% %MSGID% [origin@graylog event_source_product=\"linux\"]%msg:::sp-if-no-1st-sp%%msg:::drop-last-lf%\n"
)
# Allow only ASCII characters in the AuditD logs
local6.info action(
type="mmutf8fix"
mode="controlcharacters"
)
# This forwards AuditD logs using the previously defined template.
# Adjust the line, changing "local6.info action(" to "*.* action("
# if you want to forward all Linux logs processed by Rsyslog to the
# Graylog instance.
local6.info action(
type="omfwd"
target="{GRAYLOG SERVER ADDRESS}"
port="{GRAYLOG SERVER TCP SYSLOG PORT}"
protocol="tcp"
template="custom_linux_syslog_5424"
)
# The following line will prevent AuditD logs from being saved with
# the Linux system logs by dropping them from Rsyslog processing.
# AuditD will save the logs in a location such as /var/log/audit,
# they typically should not be saved in the system logs.
local6.info stop -
Make backup copies of the current Rsyslog configuration, including the file
/etc/rsyslog .confand the contents of/etc/rsyslog .d/. -
In the configuration, replace
{GRAYLOG SERVER ADDRESS}and{GRAYLOG SERVER TCP SYSLOG PORT}with the network address and syslog TCP port of your Graylog server. -
Test the Rsyslog configuration with the following command:
Copysudo rsyslog d -N1 -
If the Rsyslog configuration is invalid, it will indicate an error has occurred. If this is the case, analyze the error before continuing and restore the back up configuration if necessary.
-
After you have verified the configuration is valid, restart the Rsyslog service:
Copysudo systemctl restart rsyslog .service -
On SELinux-enabled systems, such as RHEL, Rsyslog may require additional permissions in order to send logs to a remote Graylog server if a non-standard port is used. Use this command to allow access on RHEL systems:
Copysudo semanage port -a -t syslogd_port_t -p tcp {GRAYLOG SYSLOG TCP PORT}For example, if you have configured Graylog to listen for syslog on TCP port 6513, then the command would be:
Copysudo semanage port -a -t syslogd_port_t -p tcp 6513 -
To view existing SELinux port configurations:
Copysudo semanage port -l | grep syslog
AuditD Service Configuration
Red Hat systems will most likely include AuditD by default, but other Linux distributions like Ubuntu may not.
The following documentation assumes that AuditD is available in the official repositories for the system you are running and that you are using the apt package manager to manage installed software on your system.
If your system does not meet these requirements, then consult the guidance for installing AuditD on your system.
-
If not completed already, install the AuditD service and associated plugins (commonly
audispd-plugins) on your system according to the documentation for your Linux distribution. -
Edit the file
/etc/audit/plugins.d/syslog.confin your editor of choice as needed, including the following necessary configurations:-
Update the configuration
active = notoactive = yes. -
Update the configuration
args = LOG_INFOtoargs = LOG_INFO LOG_LOCAL6.
-
-
Restart the AuditD service. If AuditD is configured to run in immutable mode, it may require a full system restart.
AuditD Rules Configuration
AuditD is configured using AuditD Rules. These rules define which system activity is monitored and logged by AuditD. AuditD rules are not universal, so if a rule is defined to monitor a specific syscall, but that syscall does not exist on that version of the kernel, then AuditD will generate an error attempting to load the rule.
AuditD is a complex and powerful auditing tool for Linux systems, but it is important to understand how AuditD functions and how to configure it appropriately to meet your organization's security and compliance logging requirements.
The example AuditD rules provided below are a basic set of rules intended to capture basic system activity. They are not meant to fulfill all organizational requirements and may not be compatible with your version of Linux.
-
Create the file
/etc/audit/rules.d/70-basic.rulesand add the following sample rules:Copy##############################
# USER INTERACTIVE ACTIVITY
##############################
# Monitor interactive user command execution
-a always,exit -F arch=b64 -S execve,execveat -F auid>=1000 -F auid!=4294967295 -k user-cmd
-a always,exit -F arch=b32 -S execve -F auid>=1000 -F auid!=4294967295 -k user-cmd
#################################
# USER SESSION START / STOP
#################################
# Monitor access to session tracking files
# Replaces: -w /var/run/utmp -p wa -k session-tracking
-a always,exit -F arch=b64 -S openat,openat2,truncate,unlinkat,renameat,renameat2 -F path=/var/run/utmp -F perm=wa -k session-tracking
-a always,exit -F arch=b64 -S openat,openat2,truncate,unlinkat,renameat,renameat2 -F path=/var/log/wtmp -F perm=wa -k session-tracking
-a always,exit -F arch=b64 -S openat,openat2,truncate,unlinkat,renameat,renameat2 -F path=/var/log/btmp -F perm=wa -k session-tracking
-a always,exit -F arch=b32 -S openat,truncate,unlinkat,renameat,renameat2 -F path=/var/run/utmp -F perm=wa -k session-tracking
-a always,exit -F arch=b32 -S openat,truncate,unlinkat,renameat,renameat2 -F path=/var/log/wtmp -F perm=wa -k session-tracking
-a always,exit -F arch=b32 -S openat,truncate,unlinkat,renameat,renameat2 -F path=/var/log/btmp -F perm=wa -k session-tracking
#########################################
# PRIVILEGE ESCALATION ATTEMPTS
#########################################
# Track UID transitions to root (euid=0)
-a always,exit -F arch=b64 -S setuid,setreuid,setresuid -F euid=0 -F auid>=1000 -F auid!=4294967295 -k priv-escalation
-a always,exit -F arch=b32 -S setuid,setreuid,setresuid -F euid=0 -F auid>=1000 -F auid!=4294967295 -k priv-escalation
######################################################
# PASSWORD, ACCOUNT AND GROUP CONFIGURATION CHANGES
######################################################
# Monitor modifications to sensitive identity and group files
-a always,exit -F arch=b64 -S openat,openat2,truncate,renameat,renameat2,unlinkat -F path=/etc/passwd -F perm=wa -k account-modify
-a always,exit -F arch=b64 -S openat,openat2,truncate,renameat,renameat2,unlinkat -F path=/etc/shadow -F perm=wa -k account-modify
-a always,exit -F arch=b64 -S openat,openat2,truncate,renameat,renameat2,unlinkat -F path=/etc/group -F perm=wa -k account-modify
# Optional: for older kernels supporting creat()
# -a always,exit -F arch=b64 -S openat,openat2,creat,truncate,renameat,renameat2,unlinkat -F path=/etc/passwd -F perm=wa -k account-modify
-a always,exit -F arch=b32 -S openat,truncate,renameat,renameat2,unlinkat -F path=/etc/passwd -F perm=wa -k account-modify
-a always,exit -F arch=b32 -S openat,truncate,renameat,renameat2,unlinkat -F path=/etc/shadow -F perm=wa -k account-modify
-a always,exit -F arch=b32 -S openat,truncate,renameat,renameat2,unlinkat -F path=/etc/group -F perm=wa -k account-modify
##########################
# AUDIT SYSTEM MONITORING
##########################
# Detect changes to audit configuration files or tools
-a always,exit -F arch=b64 -S openat,openat2,truncate,unlinkat,renameat,renameat2 -F path=/etc/audit/auditd.conf -F perm=wa -k audit-config
-a always,exit -F arch=b64 -S openat,openat2,truncate,unlinkat,renameat,renameat2 -F dir=/etc/audit/rules.d -F perm=wa -k audit-config
-a always,exit -F arch=b64 -S execve,execveat -F path=/sbin/auditctl -F auid>=1000 -F auid!=4294967295 -k audit-tools
-a always,exit -F arch=b32 -S openat,truncate,unlinkat,renameat,renameat2 -F path=/etc/audit/auditd.conf -F perm=wa -k audit-config
-a always,exit -F arch=b32 -S openat,truncate,unlinkat,renameat,renameat2 -F dir=/etc/audit/rules.d -F perm=wa -k audit-config
-a always,exit -F arch=b32 -S execve -F path=/sbin/auditctl -F auid>=1000 -F auid!=4294967295 -k audit-tools
#################################
# AUDIT LOG FILE ACTIVITY
#################################
# Monitor changes to the audit log files themselves
-a always,exit -F arch=b64 -S openat,openat2,truncate,renameat,renameat2,unlinkat -F dir=/var/log/audit -F perm=wa -k audit-logs
-a always,exit -F arch=b32 -S openat,truncate,renameat,renameat2,unlinkat -F dir=/var/log/audit -F perm=wa -k audit-logs -
Load the rules:
Copysudo augenrules --loadHint: If you encounter an error with loading the rules, it will be indicated at the end of theaugenrulesoutput. -
Some systems may have AuditD configured to run in "immutable" mode, so note these systems will require a full system restart to enable new/modified rules.
Example Logs
The AuditD processing pack will modify AuditD logs, trimming the header metadata from the AuditD log message.
This section will include examples of both the full messages, including the Syslog header and the resulting message after Illuminate has trimmed the header component from the message.
Syscall Log Example - Full Log
<18>node=testgoat01 type=SYSCALL msg=audit(1749212648.902:7315): arch=c00000b7 syscall=14 success=no exit=-61 a0=c698361a5470 a1=f324ec214fc8 a2=0 a3=31a60d86952b0 items=1 ppid=1 pid=18990 auid=1000 uid=1000 gid=1000 euid=1000 suid=1000 fsuid=1000 egid=1000 sgid=1000 fsgid=1000 tty=(none) ses=282 comm="systemd" exe="/usr/lib/systemd/systemd" subj=unconfined key="perm_mod" ARCH=aarch64 SYSCALL=removexattr AUID="usera" UID="usera" GID="usera" EUID="usera" SUID="usera" FSUID="usera" EGID="usera" SGID="usera" FSGID="usera
Syscall Log Example - Processed Log
<18>audit(1749212648.902:7315): arch=c00000b7 syscall=14 success=no exit=-61 a0=c698361a5470 a1=f324ec214fc8 a2=0 a3=31a60d86952b0 items=1 ppid=1 pid=18990 auid=1000 uid=1000 gid=1000 euid=1000 suid=1000 fsuid=1000 egid=1000 sgid=1000 fsgid=1000 tty=(none) ses=282 comm="systemd" exe="/usr/lib/systemd/systemd" subj=unconfined key="perm_mod" ARCH=aarch64 SYSCALL=removexattr AUID="usera" UID="usera" GID="usera" EUID="usera" SUID="usera" FSUID="usera" EGID="usera" SGID="usera" FSGID="usera"
CRED_DISP Log Example - Full Log
<18>node=rhel-machine type=CRED_DISP msg=audit(1746772858.810:7300): pid=53518 uid=1000 auid=1000 ses=13 subj=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 msg='op=PAM:setcred grantors=pam_env,pam_fprintd acct="root" exe="/usr/bin/sudo" hostname=? addr=? terminal=/dev/pts/0 res=success' UID="company" AUID="company"
GIM Categorization
In most cases the AuditD logs will be categorized based on the AuditD event type, though for some generic event types, the op property will be used alongside the event type for categorization.
GIM categorization is provided for the following messages:
| Event Type | AuditD Op | GIM Category | GIM Subcategory | GIM Event Type |
|---|---|---|---|---|
| ANOM_LOGIN_TIME | authentication | authentication.access policy | access policy violation | |
| ANOM_LOGIN_SESSIONS | authentication | authentication.access policy | access policy violation | |
| ANOM_LOGIN_FAILURES | authentication | authentication.access policy | access policy violation | |
| ANOM_LOGIN_LOCATION | authentication | authentication.access policy | access policy violation | |
| ANOM_LOGIN_SERVICE | authentication | authentication.access policy | access policy violation | |
| USER_ACCT | authentication | authentication.default | authentication message | |
| USER_AUTH | authentication | authentication.credential validation | credential validation | |
| CRED_ACQ | authentication | authentication.default | authentication message | |
| USER_START | authentication | authentication.logon | logon | |
| USER_LOGIN | authentication | authentication.default | authentication message | |
| CRED_DISP | authentication | authentication.default | authentication message | |
| USER_END | authentication | authentication.logoff | logoff | |
| LOGIN | authentication | authentication.default | authentication message | |
| USER_LOGOUT | authentication | authentication.default | authentication message | |
| CRED_REFR | authentication | authentication.default | authentication message | |
| ADD_GROUP | iam | iam.object create | group created | |
| DEL_GROUP | iam | iam.object delete | group deleted | |
| MOD_GROUP | iam | iam.object modify | group properties modified | |
| GRP_MGMT | delete-group | iam | iam.object delete | group deleted |
| GRP_MGMT | add-group | iam | iam.object create | group created |
| GRP_MGMT | (other - not listed) | iam | iam.default | iam message |
| ADD_USER | iam | iam.object create | account created | |
| DEL_USER | iam | iam.object delete | account deleted | |
| MOD_USER | iam | iam.object modify | account modified | |
| ADD_USER_TO_GROUP | iam | iam.default | iam message | |
| DEL_USER_FROM_GROUP | iam | iam.default | iam message | |
| USER_CHAUTHTOK | iam | iam.object modify | Administrative password reset | |
| GRP_AUTH | iam | iam.default | iam message | |
| USER_ROLE_CHANGE | iam | iam.default | iam message | |
| USER_MGMT | add-user | iam | iam.default | iam message |
| USER_MGMT | faillock-reset | iam | iam.object enable | account unlocked |
| USER_MGMT | add-user-to-group | iam | iam.object modify | group member added |
| USER_MGMT | (other - not listed) | iam | iam.default | iam message |
| ACCT_LOCK | iam | iam.object disable | account locked | |
| ACCT_UNLOCK | iam | iam.object enable | account unlocked | |
| GRP_CHAUTHTOK | iam | iam.object modify | Administrative password reset | |
| SERVICE_START | service | service.start | service started | |
| SERVICE_STOP | service | service.stop | service stopped |
Message Fields Included in This Pack
General Parsing
This pack will apply normalization to common fields that are present in all AuditD event logs. Additionally, it will replace the "message" field with the contents of the AuditD "msg" property, reducing the size of the overall message.
| Normalized Field Name | AuditD Source Property | Description |
|---|---|---|
| event_key | key | This is the user-provided key value that is optionally defined in AuditD Rules. |
| vendor_event_type | type | This is the AuditD event type. |
| event_source | node | This is the hostname that is sometimes added by AuditD to event messages. |
Event Enrichment
The following fields are added to all AuditD event messages:
| Field Name | Description |
|---|---|
| event_correlation_hash | Unique identifier to correlate messages associated with the same AuditD event. |
| event_outcome | The normalized outcome (\success\" or \"failure\") based on on the indication of event outcome in the event - see \"vendor_event_outcome\"." |
| vendor_event_outcome | The outcome property based on the value of the AuditD properties \res\" or \"success\"." |
Group Management Event Fields
This pack will process the following Linux AuditD group management event types:
- ADD_GROUP
- DEL_GROUP
- MOD_GROUP
- GROUP_MGMT
These events will be processed and normalized as follows:
| Normalized Field Name | AuditD Source Property | Description |
|---|---|---|
| group_name | acct | The name of the linux group described in the event |
| process_id | pid | The process ID of the associated executable described in the event |
| source_addr | addr | If the value is determined not to be an IPv4 or IPv6 it will be assigned to source_addr |
| source_ip | addr | If the value is determined to be an IPv4 or IPv6 address it will be assigned to source_ip |
| user_audit_id | auid | The audit user ID of the user taking action described in the event |
| user_audit_name | AUID | The audit user name of the user taking action described in the event |
| user_effective_id | euid | The effective user ID of the user taking action described in the event |
| user_effective_name | EUID | The effective user name of the user taking action described in the event |
| user_id | uid | The Linux user ID of the user taking action described in the event |
| user_name | UID | The user taking action described in the event |
| user_session_id | ses | The session identifier associated with the user session described in the event |
| user_terminal | terminal | The terminal name associated with the user session described in the event |
User Management Event Fields
This pack will process the following Linux AuditD user management event types:
- ADD_USER
- ADD_USER_TO_GROUP
- ACCT_LOCK
- ACCT_UNLOCK
- DEL_USER
- DEL_USER_FROM_GROUP
- GRP_AUTH
- GRP_CHAUTHTOK
- MOD_USER
- USER_CHAUTHTOK
- USER_MGMT
- USER_ROLE_CHANGE
It is important to note that different Linux distributions and versions may generate different event types to represent the same action.
Fields in user management events will be normalized as follows:
| Normalized Field Name | AuditD Source Property | Description |
|---|---|---|
| group_name | grp | The group name sometimes included in AuditD user management events |
| process_id | pid | The process ID of the associated executable described in the event |
| source_ip or source_addr | addr | If the value is determined to be an IP it will be assigned to source_ip, otherwise it will be source_addr |
| target_user_id | id | The User ID of the linux user account that is the target of the user management action |
| target_user_name | acct or ID | The name of the linux user account that is the target of the user management action |
| user_audit_id | auid | The audit user ID of the user taking action described in the event |
| user_audit_name | AUID | The audit user name of the user taking action described in the event |
| user_effective_id | euid | The effective user ID of the user taking action described in the event |
| user_effective_name | EUID | The effective user name of the user taking action described in the event |
| user_id | uid | The Linux user ID of the user taking action described in the event |
| user_name | UID | The user taking action described in the event |
| user_session_id | ses | The session identifier associated with the user session described in the event |
| user_terminal | terminal | The terminal name associated with the user session described in the event |
ANOM_LOGIN_* Event Fields
This pack processes events with the "ANOM_LOGIN" prefix.
These events are generated when a login access policy, defined in Linux PAM, is violated. The types of events processed by this pack include:
- ANOM_LOGIN_FAILURES
- ANOM_LOGIN_LOCATION
- ANOM_LOGIN_SERVICE
- ANOM_LOGIN_SESSIONS
- ANOM_LOGIN_TIME
Fields in ANOM_LOGIN events will be normalized as follows:
| Normalized Field Name | AuditD Source Property | Description |
|---|---|---|
| group_name | acct | The name of the linux group described in the event |
| process_id | pid | The process ID of the associated executable described in the event |
| source_ip or source_addr | addr | If the value is determined to be an IP it will be assigned to source_ip, otherwise it will be source_addr |
| user_audit_id | auid | The audit user ID of the user taking action described in the event |
| user_audit_name | AUID | The audit user name of the user taking action described in the event |
| user_effective_id | euid | The effective user ID of the user taking action described in the event |
| user_effective_name | EUID | The effective user name of the user taking action described in the event |
| user_id | uid | The Linux user ID of the user taking action described in the event |
| user_name | UID | The user taking action described in the event |
| user_session_id | ses | The session identifier associated with the user session described in the event |
| user_terminal | terminal | The terminal name associated with the user session described in the event |
User Authentication Event Fields
This pack processes events related to user authentication and session activity. It applies to the following AuditD event types:
- USER_ACCT
- USER_AUTH
- CRED_ACQ
- USER_START
- USER_LOGIN
- CRED_DISP
- USER_END
- LOGIN
- USER_LOGOUT
- CRED_REFR
These events indicate authentication lifecycle activities such as credential acquisition, login attempts, session starts and ends, and logout operations.
The fields in these authentication-related events will be normalized as follows:
| Normalized Field Name | AuditD Source Property | Description |
|---|---|---|
| source_addr | addr | Source address of the user (renamed for clarity) |
| destination_hostname | event_source | Hostname of the system processing the event |
| source_hostname | hostname | Resolved hostname for the source system |
| session_id | ses | Session ID of the login event |
| user_name | UID | Username of the account |
| user_id | uid | UID of the account |
| user_name | AUID | Audit name of the account |
| user_id | auid | Audit UID (AUID) of the account |
| user_effective_name | EUID | Effective username of the account |
| user_effective_id | euid | Effective UID of the account |
SERVICE_* Event Fields
This section documents field extraction and normalization for SERVICE_START and SERVICE_STOP events.
These events record when system services are started or stopped, typically via systemd or similar service managers. They are useful for monitoring service lifecycle activity, validating operational status, and detecting unexpected or unauthorized changes in service state.
The fields extracted from these events identify the service, the initiating user, and process metadata.
Fields in SERVICE_* events will be normalized as follows:
| Normalized Field Name | AuditD Source Property | Description |
|---|---|---|
| service_name | unit | Name of the service unit |
| user_name | UID | Resolved name of the real user |
| user_id | uid | Numeric ID of the real user |
| user_audit_name | AUID | Resolved audit user name |
| user_audit_id | auid | Audit user ID |
| user_effective_name | EUID | Resolved effective user name |
| user_effective_id | euid | Numeric effective user ID |
| process_id | pid | Process ID of the service trigger process |
SYSCALL Event Fields
This section documents field extraction and normalization for SYSCALL events.
SYSCALL events are generated when system calls are invoked by user-space processes. These logs provide detailed insight into process behavior, arguments passed to syscalls, and user context at execution time. Monitoring these events enables deep visibility into potential privilege escalations, file modifications, or anomalous process behavior.
Fields in SYSCALL events will be normalized as follows:
| Normalized Field Name | AuditD Source Property | Description |
|---|---|---|
| process_path | exe | Full path to the executable binary |
| host_architecture | ARCH | Reported architecture name |
| host_architecture_id | arch | Architecture identifier constant |
| process_id | pid | Process ID of the syscall origin |
| process_parent_id | ppid | Parent process ID |
| user_session_id | ses | Audit session ID |
| process_name_alternate | comm | Command name (may differ from exe) |
| user_terminal | tty | Terminal device used |
| syscall_id | syscall | Syscall numeric ID |
| syscall_name | SYSCALL | Syscall name |
| syscall_exit_code | exit | Syscall return/exit code |
| user_filesystem_id | fsuid | Filesystem user ID |
| user_filesystem_name | FSUID | Resolved name for fsuid |
| user_filesystem_group_id | fsgid | Filesystem group ID |
| user_filesystem_group_name | FSGID | Resolved name for fsgid |
| user_effective_group_id | egid | Effective group ID |
| user_effective_group_name | EGID | Resolved effective group name |
| user_group_id | gid | Real group ID |
| user_group_name | GID | Resolved real group name |
| user_saved_group_id | sgid | Saved group ID |
| user_saved_group_name | SGID | Resolved saved group name |
| user_saved_id | suid | Saved UID |
| user_saved_name | SUID | Resolved saved UID name |
| syscall_associated_item_count | items | Number of objects linked to the syscall |
| user_name | UID | Resolved real user name |
| user_id | uid | Real user ID |
| user_audit_name | AUID | Resolved audit user name |
| user_audit_id | auid | Audit user ID |
| user_effective_name | EUID | Resolved effective user name |
| user_effective_id | euid | Effective user ID |
Linux AuditD spotlight
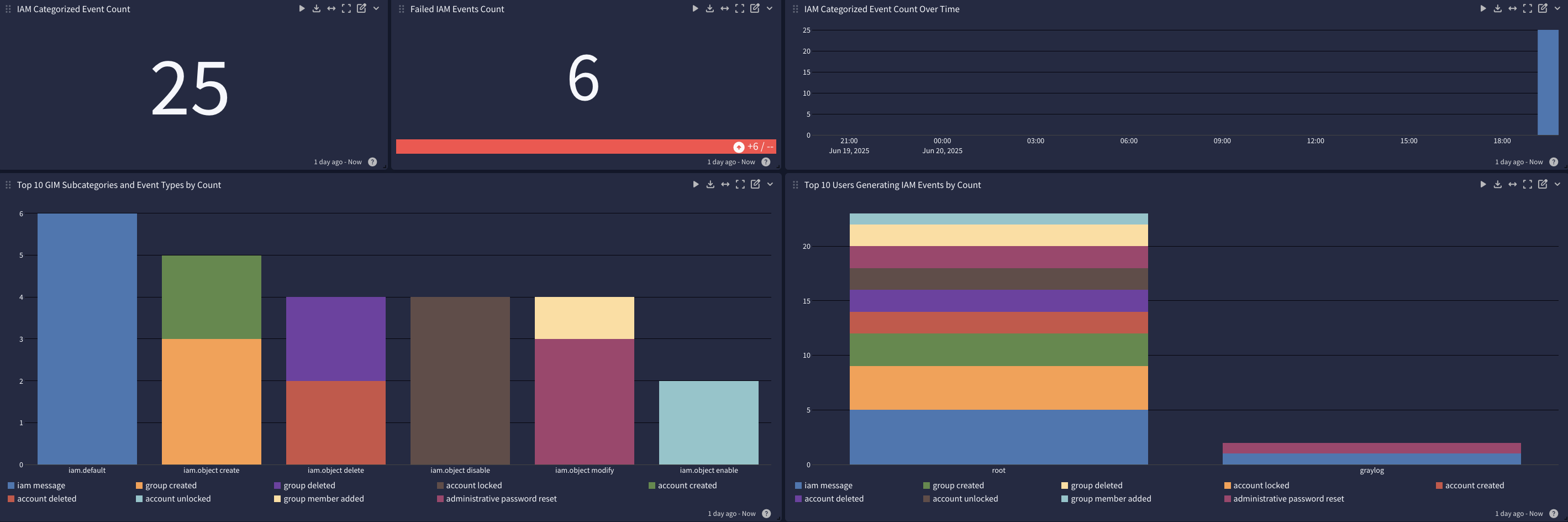
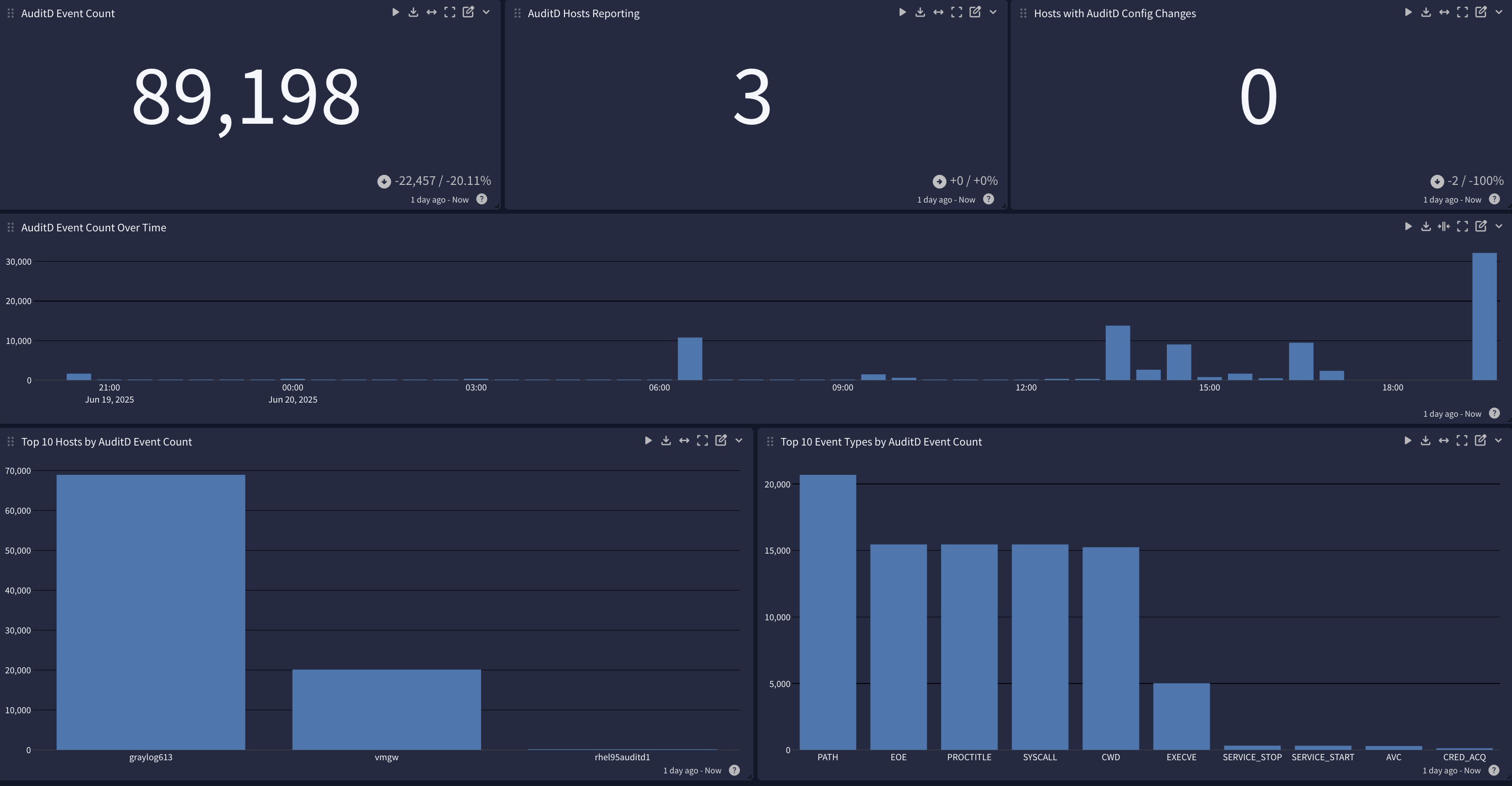
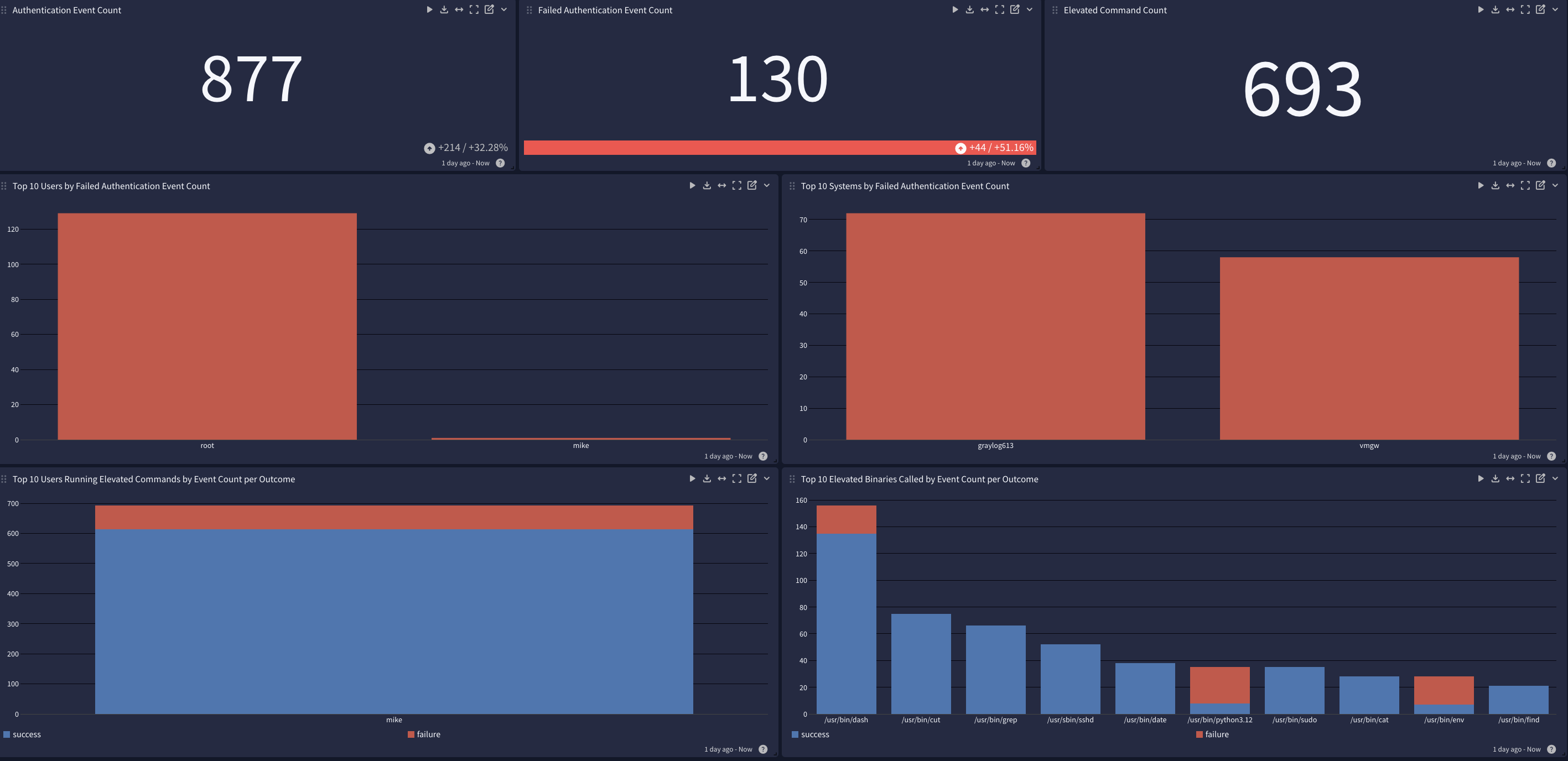
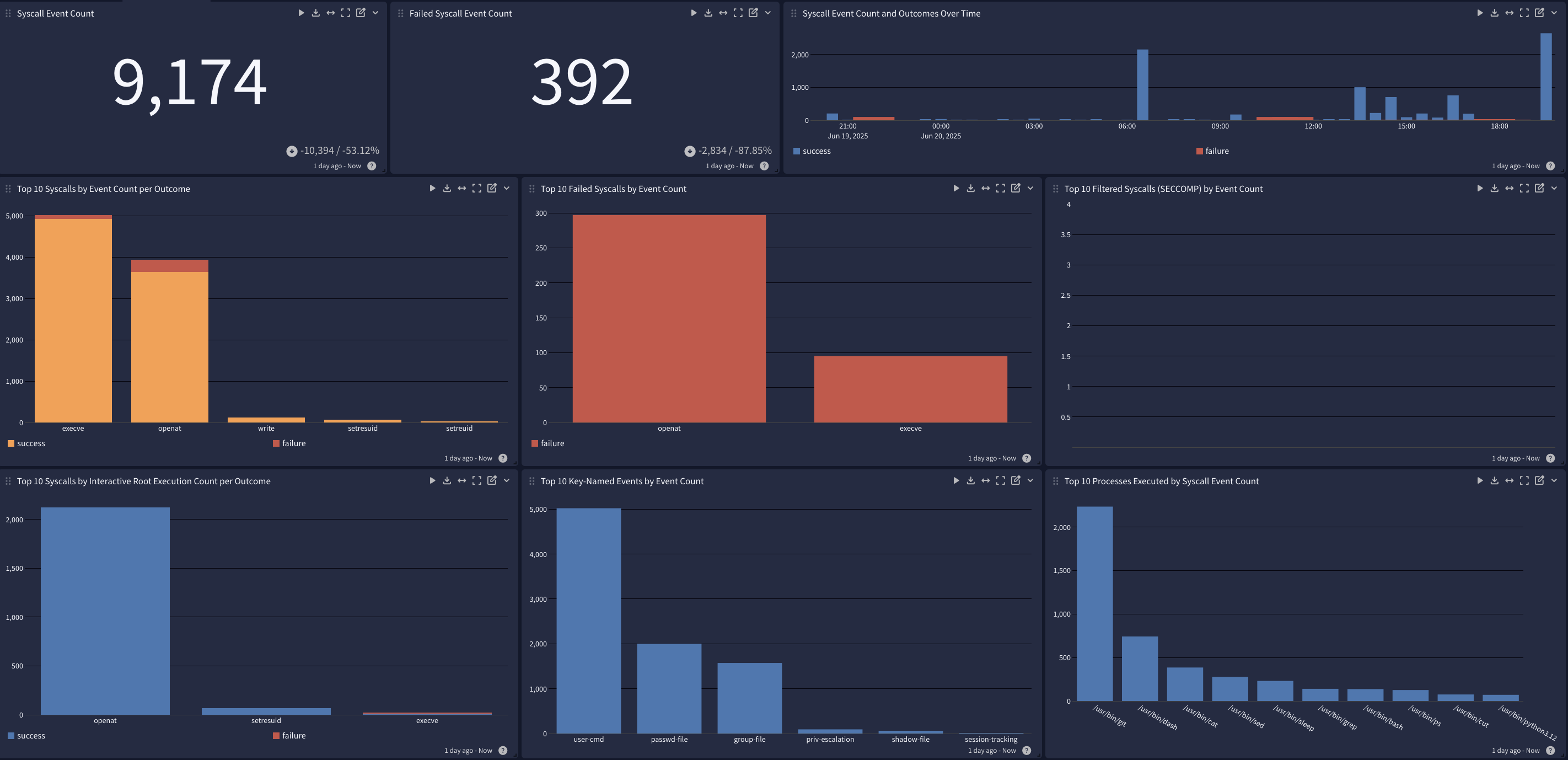
This spotlight offers a dashboard with 4 tabs:
Overview
User Activity
Syscall Activity
Identity and Access Management Activity