Fortinet's FortiGate is a next-generation firewall that covers both traditional and wireless traffic. The hardware-based firewall can function as an IPS and include SSL inspection and web filtering. This technology pack will process FortiGate event log messages, providing normalization and enrichment of common events of interest.
Requirement(s)
- FortiGate running FortiOS Version 7.0 or later
- Graylog Server with a valid Enterprise license, running Graylog version 4.2.5 or later
Configure FortiGate to transmit Syslog to your Graylog server Syslog input.
Not Supported
- Sending FortiGate logs with the CEF format.
Stream Configuration
This technology pack includes 1 stream:
- Illuminate:Fortigate Messages
Index Set Configuration
This technology pack includes 1 index set definition:
- Fortinet Event Log Messages
Log Collection
Configure your FortiGate device(s) following the instructions in the Graylog Syslog Inputs guide using TCP as the transport and format BSD.
Log Format Example
date=2021-06-22 time=14:32:46 devname="ABCD-EFG-HIK-LMN-202-87-35-206" devid="FGA20E5Q16027714" logid="0000000013" type="traffic" subtype="forward" level="notice" vd="root" eventtime=1624352568074022779 tz="+0530" srcip=x.x.x.x srcport=50198 srcintf="wan1" srcintfrole="wan" dstip=2.2.2.2 dstport=4510 dstintf="wan2" dstintfrole="wan" sessionid=2912907682 proto=6 action="close" policyid=32 policytype="policy" poluuid="5b3cd3ef-0fd0-51e7-1222-9c9e72bdfbba" service="4510" dstcountry="India" srccountry="India" trandisp="dnat" tranip=1.1.1.1 tranport=4510 duration=62 sentbyte=2049 rcvdbyte=2703 sentpkt=12 rcvdpkt=11 appcat="unscanned"
What is Provided
-
Rules to parse, normalize, and enrich Fortigate Content Pack messages.
-
A Fortigate Spotlight content pack
GIM Categorization
GIM categorization is provided for the following messages:
| fortigate_subtype | gim_event_type_code | gim_event_category | gim_event_class | gim_event_subcategory | gim_event_type |
|---|---|---|---|---|---|
| forward | 120000 | network | network.network connection | network connection | |
| multicast | 129999 | network | network.default | network message | |
| sniffer | 129999 | network | network.default | network message | |
| webfilter | 129999 | network | network.default | network message | |
| virus | 309999 | detection | detection.default | detection_message | |
| anomaly | 309999 | detection | detection.default | detection_message | |
| local | 129999 | network | network.default | network message | |
| ssl | 129999 | network | network.default | network message | |
| ips | 300001 | detection | detection.network_detection | network_detection | |
| signature | 309999 | detection | detection.default | detection_message | |
| 0100026001 | 290300 | dhcp | protocol | dhcp.acknowledgement | dhcp acknowledgement |
| 0104043666 | 290100 | dhcp | protocol | dhcp.offer | dhcp offer |
| 0104043664 | 290000 | dhcp | protocol | dhcp.request | dhcp request |
Message Fields Included in This Pack
Parsed Fields
This pack applies normalization to common fields that are present in all FortiGate event logs.
| FortiGate Source Property | Normalized Field Name |
|---|---|
| srcintf | network_interface_in |
| dstintf | network_interface_out |
| srcmac | source_mac |
| dstmac | destination_mac |
| srcip | source_ip |
| srcport | source_port |
| dstip | destination_ip |
| dstport | destination_port |
| dst_host | destination_host |
| sessionid | session_id |
| policyid | policy_id |
| policytype | policy_type |
| service | network_application |
| sentbyte | source_bytes_sent |
| rcvdbyte | destination_bytes_sent |
| sentpkt | source_packets_sent |
| rcvdpkt | destination_packets_sent |
| tunnelip | tunnel_ip |
| remip | remote_ip |
| locip | local_ip |
| devid | event_observer_id |
| apprisk | vendor_threat_suspected |
| hostname | destination_domain |
| vd | virtual_domain_name |
| utmaction | vendor_utm_action |
| user | user_name |
| vendor_hostname | host_hostname |
| app | application_name |
| logid | event_id |
| filename | file_name |
| filetype | file_type |
| craction | vendor_threat_weight_action |
| crlevel | vendor_threat_weight_level |
| crscore | vendor_threat_weight_score |
| agent | http_user_agent |
| from | source_user_email |
| to | destination_user_email |
| sender | http_sender |
| fctuid | vendor_client_user_id |
| url | http_url |
| dtime | event_created |
| itime | event_received_time |
| vrf | vendor_virtual_routing_and_forwarding |
| dstepid | vendor_destination_endpoint_id |
| fctemssn | vendor_client_endpoint_ssn |
| addr | vendor_address |
| euid | vendor_enduser_id |
| threat | threat_category |
| attack | vendor_alert_category |
| cve | cve_number |
| itime_t | vendor_log_received |
| idseq | event_uid |
| ref | vendor_reference_url |
| mastersrcmac | vendor_source_master_mac |
| srccountry | vendor_source_country |
| dstcountry | vendor_destination_country |
| srcuuid | vendor_source_uuid |
| srcname | vendor_source_name |
| appcat | vendor_application_category |
| dstname | vendor_destination_name |
| qclass | query_class |
| ipaddr | dns_value |
| osname | vendor_source_os_name |
| trandisp | vendor_nat_translation_type |
| appid | vendor_application_id |
| utmref | vendor_reference_to_utm |
| ssid | wifi_ssid |
| channel | wifi_channel |
| encryption | wifi_encryption |
| stamac | host_mac |
| remotewtptime | vendor_remote_wifi_radius_authentication_time |
| vap | wifi_virtual_access_point |
| qname | query_request |
| qtype | query_record_type |
| qtypeval | query_record_type_code |
| applist | vendor_application_list |
| lanin | vendor_incoming_lantraffic_bytes |
| lanout | vendor_outgoing_lantraffic_bytes |
| wanin | vendor_incoming_wantraffic_bytes |
| wanout | vendor_outgoing_wantraffic_bytes |
| countav | vendor_number_of_associated_av_logs |
| countapp | vendor_number_of_associated_app_ctrl_logs |
| cfgattr | vendor_configuration_attribute |
| cfgpath | vendor_configuration_path |
| cfgtid | vendor_configuration_id |
| cfgobj | vendor_configuration_setting |
| dvid | vendor_device_id |
| epid | vendor_endpoint_id |
| tz | vendor_time_zone |
| dstosname | vendor_destination_os_name |
| devtype | vendor_source_device_type |
| dstdevtype | vendor_destination_device_type |
| duration | event_duration |
| virus | vendor_virus |
| attackid | vendor_attackid |
| virusid | vendor_virusid |
| viruscat | vendor_viruscat |
| proto | vendor_proto |
| eventtime | vendor_eventtime |
| action | vendor_action |
| time | vendor_time |
| date | vendor_date |
| status | vendor_status |
| eventtype | vendor_eventtype |
| pri | vendor_pri |
| severity | vendor_severity |
| devname | vendor_devname |
| type | vendor_type |
| subtype | vendor_subtype |
| attachment | vendor_attachment |
| direction | vendor_direction |
| srcdomain | vendor_srcdomain |
| subject | vendor_subject |
| dtype | vendor_dtype |
| profile | vendor_profile |
| quarskip | vendor_quarskip |
| id | vendor_id |
| msg | vendor_msg |
| count | vendor_count |
| icmpcode | vendor_icmpcode |
| icmpid | vendor_icmpid |
| icmptype | vendor_icmptype |
| transip | vendor_transip |
| transport | vendor_transport |
| tranip | vendor_tranip |
| tranport | vandor_tranport |
| logdesc | vendor_logdesc |
| method | vendor_method |
| reason | vendor_reason |
| sn | vendor_sn |
| ui | vendor_ui |
| security | vendor_security |
| ap | vendor_ap |
| policyname | policy_name |
| dsthwvendor | vendor_destination_hw_interface |
| dstintfrole | vendor_destination_interface_role |
| srchwvendor | vendor_source_hw_interface |
| srcintfrole | vendor_source_interface_role |
| dstserver | vendor_destination_server |
| srcserver | vendor_source_server |
| poluuid | policy_uid |
Event Enrichment
The following fields are added to all FortiGate event messages:
| Field Name | Description |
|---|---|
| event_severity | Text description of the severity rating of the event |
| event_severity_level | Numeric representation of the severity rating of the event |
| vendor_event_severity_level | Vendor-defined numeric severity rating for the event |
| destination_reference | Mapped from source_ip or source_hostname in that order |
| source_reference | Mapped from source_ip or source_hostname in that order |
| host_reference | Mapped from host_ip or host_hostname in that order - allows a common field to reference for messages that do not provide both |
| event_source | Source system that generated the event |
| vendor_full_url | The normalized full url based on combination of destination_domain and http_url |
Fortigate Spotlight Content Pack
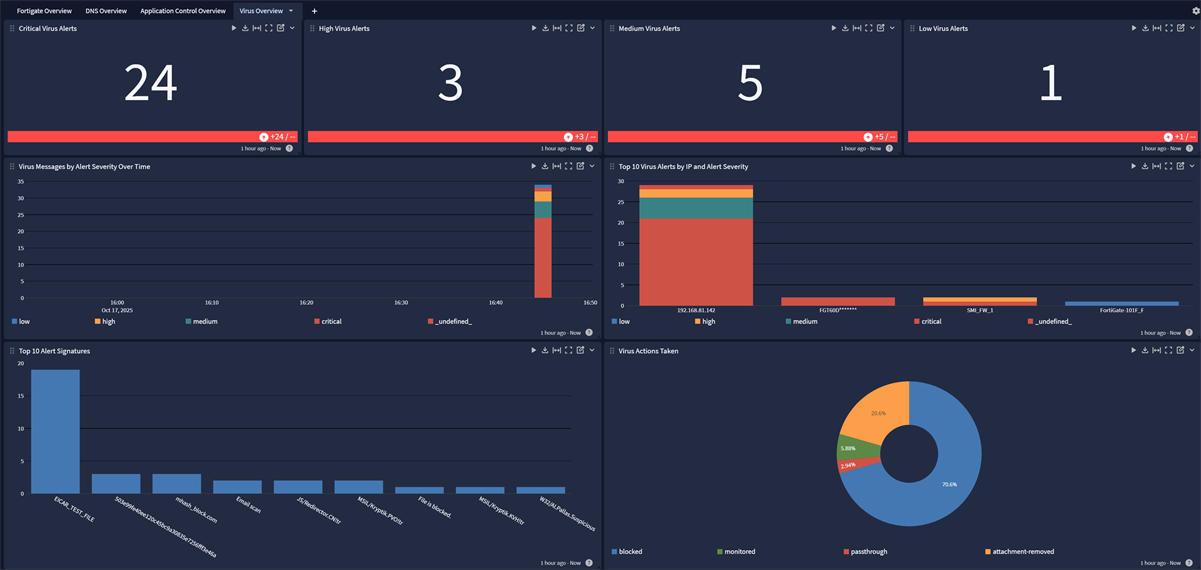
The Fortigate Spotlight Pack offers an overview dashboard with the following tabs:
Overview
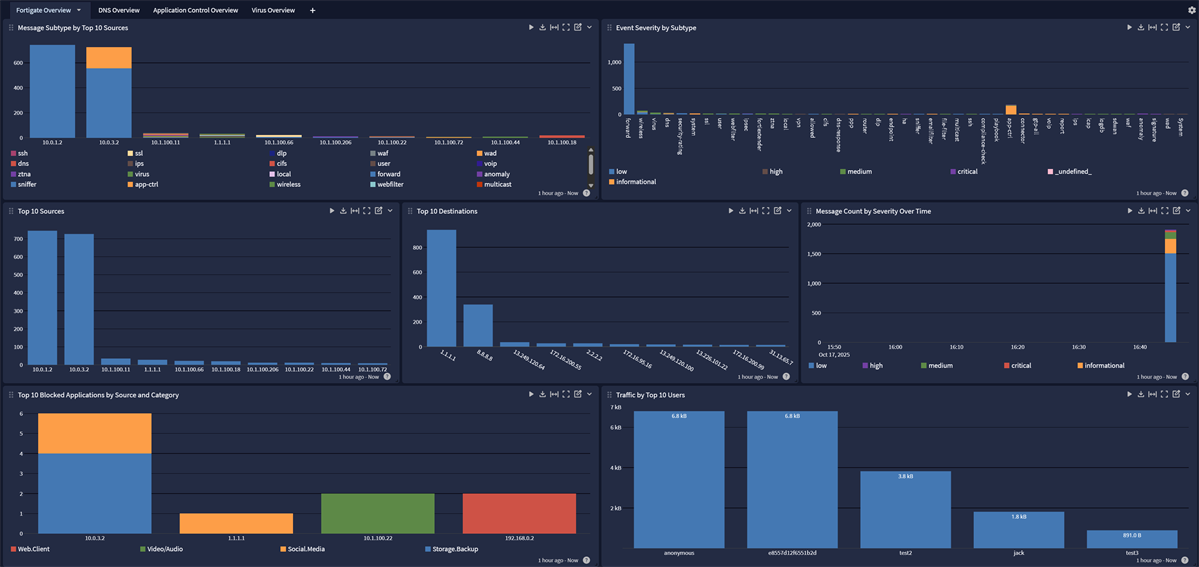
DNS
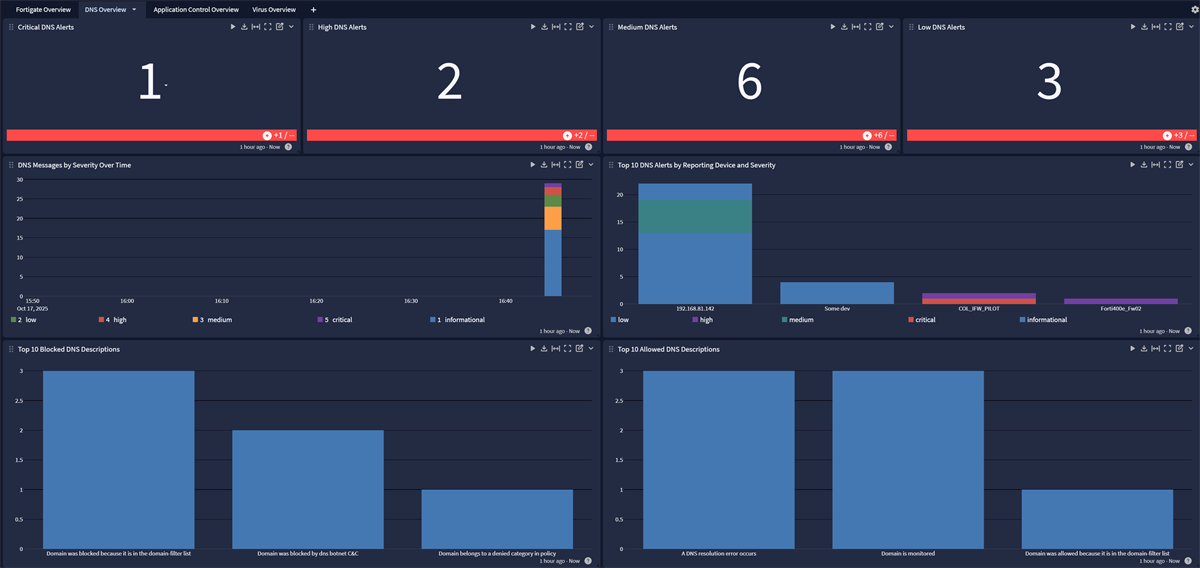
Application Control
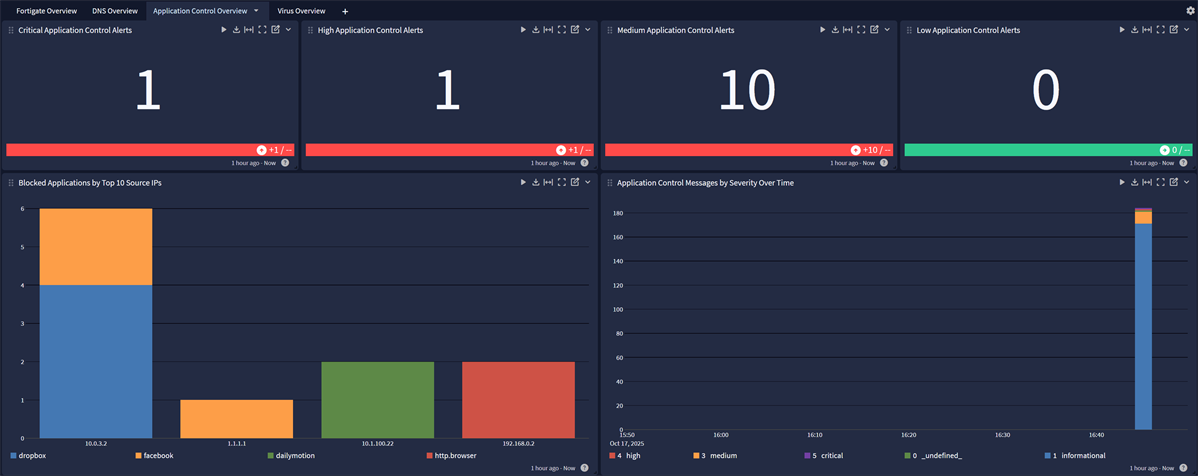
Virus