AWS Security Hub Content Pack
AWS Security Hub is a centralized security and compliance service that aggregates, normalizes,
and prioritizes findings from multiple AWS services and third-party tools using the AWS Security Finding Format (ASFF). It provides a unified view of your security posture across your AWS accounts, helping you identify and remediate potential risks efficiently.
Supported Version(s)
-
Current version offered by Amazon as of December 2025.
Requirements
-
Graylog 6.3.7+
Stream Configuration
This technology pack includes 1 stream:
- Illuminate:AWS Security Hub Messages
Index Set Configuration
This technology pack includes 1 index set definition:
- AWS Security Hub Logs
Log Collection and Delivery
This pack parses logs from the following sources:
-
AWS Kinesis/CloudWatch Input
AWS Kinesis/CloudWatch Input Configuration
Refer to the input documentation to setup the AWS Kinesis/CloudWatch input.
Log Format Example
These are example logs for various processed log types.
GuardDuty
{"version":"0","id":"1f4fae6e-e5fb-1ea7-4429-115d43a26fb6","detail-type":"Security Hub Findings - Imported","source":"aws.securityhub","account":"517803882956","time":"2025-11-21T14:05:03Z","region":"us-east-1","resources":["arn:aws:securityhub:us-east-1::product/aws/guardduty/arn:aws:guardduty:us-east-1:517803882956:detector/2ccd501f6c1ad78037a84d3fc2c7e8c9/finding/633b4b32bddc4195bffe43c03de41e02"],"detail":{"findings":[{"ProductArn":"arn:aws:securityhub:us-east-1::product/aws/guardduty","Types":["TTPs/Credential Access/CredentialAccess:RDS-AnomalousBehavior.FailedLogin"],"SourceUrl":"https://us-east-1.console.aws.amazon.com/guardduty/home?region=us-east-1#/findings?macros=current&fId=633b4b32bddc4195bffe43c03de41e02","Description":"One or more unusual failed login attempts were observed on an RDS database in your account.","ProductName":"GuardDuty","FirstObservedAt":"2025-11-20T07:51:29.000Z","CreatedAt":"2025-11-20T07:51:29.455Z","LastObservedAt":"2025-11-21T14:01:40.000Z","CompanyName":"Amazon","FindingProviderFields":{"Types":["TTPs/Credential Access/CredentialAccess:RDS-AnomalousBehavior.FailedLogin"],"Severity":{"Normalized":40,"Label":"HIGH","Product":8}},"ProductFields":{"aws/guardduty/service/additionalInfo/profiledBehavior/profiledSuccessfulApplicationNamesClusterProfiling.2_/applicationName":"GeneratedFindingApplicationName3","aws/guardduty/service/action/rdsLoginAttemptAction/remoteIpDetails/ipAddressV4":"1.2.3.4","aws/guardduty/service/additionalInfo/unusualBehavior/unusualUserNameClusterProfiling/incompleteConnectionCount":"0","aws/guardduty/service/action/rdsLoginAttemptAction/remoteIpDetails/ipAddressV6":"1234:5678:90ab:cdef:1234:5678:90ab:cde0","aws/guardduty/service/additionalInfo/unusualBehavior/unusualDatabaseNameClusterProfiling/databaseName":"GeneratedFindingDatabaseName","aws/guardduty/service/action/rdsLoginAttemptAction/remoteIpDetails/organization/isp":"GeneratedFindingIsp","aws/guardduty/service/additionalInfo/profiledBehavior/profiledSuccessfulUserNamesClusterProfiling.1_/userName":"GeneratedFindingUserName2","aws/guardduty/service/action/rdsLoginAttemptAction/remoteIpDetails/geoLocation/lon":"0","aws/guardduty/service/action/rdsLoginAttemptAction/remoteIpDetails/organization/asn":"0","aws/guardduty/service/additionalInfo/profiledBehavior/profiledSuccessfulApplicationNamesClusterProfiling.1_/count":"1","aws/guardduty/service/additionalInfo/profiledBehavior/profiledSuccessfulApplicationNamesClusterProfiling.2_/count":"1","aws/guardduty/service/additionalInfo/profiledBehavior/profiledSuccessfulApplicationNamesClusterProfiling.1_/applicationName":"GeneratedFindingApplicationName2","aws/guardduty/service/additionalInfo/profiledBehavior/profiledSuccessfulApplicationNamesClusterProfiling.0_/count":"1","aws/guardduty/service/additionalInfo/profiledBehavior/profiledSuccessfulApplicationNamesClusterProfiling.3_/count":"1","aws/guardduty/service/additionalInfo/unusualBehavior/unusualDatabaseNameClusterProfiling/failedLoginCount":"1","aws/guardduty/service/additionalInfo/unusualBehavior/unusualASNClusterProfiling/incompleteConnectionCount":"0","aws/guardduty/service/action/actionType":"RDS_LOGIN_ATTEMPT","aws/guardduty/service/additionalInfo/unusualBehavior/unusualUserNameClusterProfiling/failedLoginCount":"1","aws/guardduty/service/additionalInfo/profiledBehavior/profiledSuccessfulUserNamesClusterProfiling.2_/count":"1","aws/guardduty/service/additionalInfo/unusualBehavior/unusualApplicationNameClusterProfiling/incompleteConnectionCount":"0","aws/guardduty/service/additionalInfo/profiledBehavior/profiledSuccessfulApplicationNamesClusterProfiling.0_/applicationName":"GeneratedFindingApplicationName1","aws/guardduty/service/additionalInfo/unusualBehavior/unusualASNClusterProfiling/failedLoginCount":"1","aws/guardduty/service/additionalInfo/profiledBehavior/profiledSuccessfulApplicationNamesClusterProfiling.3_/applicationName":"GeneratedFindingApplicationName4","aws/guardduty/service/additionalInfo/unusualBehavior/unusualApplicationNameClusterProfiling/applicationName":"GeneratedFindingApplicationName","aws/guardduty/service/additionalInfo/profiledBehavior/profiledSuccessfulAsnOrgsClusterProfiling.1_/asnOrg":"GeneratedFindingAsnOrg2","aws/guardduty/service/action/rdsLoginAttemptAction/remoteIpDetails/organization/org":"GeneratedFindingOrg","aws/guardduty/service/action/rdsLoginAttemptAction/remoteIpDetails/geoLocation/lat":"0","aws/guardduty/service/additionalInfo/profiledBehavior/profiledSuccessfulAsnOrgsClusterProfiling.0_/count":"1","aws/guardduty/service/additionalInfo/profiledBehavior/profiledSuccessfulAsnOrgsClusterProfiling.2_/count":"1","aws/guardduty/service/additionalInfo/profiledBehavior/profiledSuccessfulAsnOrgsClusterProfiling.3_/asnOrg":"GeneratedFindingAsnOrg4","aws/guardduty/service/additionalInfo/profiledBehavior/profiledSuccessfulUserNamesClusterProfiling.0_/count":"1","aws/guardduty/service/action/rdsLoginAttemptAction/remoteIpDetails/city/cityName":"GeneratedFindingCityName","aws/guardduty/service/additionalInfo/unusualBehavior/unusualASNClusterProfiling/asnOrg":"GeneratedFindingAsnOrg","aws/guardduty/service/action/rdsLoginAttemptAction/remoteIpDetails/organization/asnOrg":"GeneratedFindingAsnOrg","aws/guardduty/service/additionalInfo/unusualBehavior/unusualApplicationNameClusterProfiling/failedLoginCount":"1","aws/guardduty/service/additionalInfo/profiledBehavior/profiledSuccessfulAsnOrgsClusterProfiling.0_/asnOrg":"GeneratedFindingAsnOrg1","aws/guardduty/service/action/rdsLoginAttemptAction/remoteIpDetails/country/countryName":"GeneratedFindingCountryName","aws/guardduty/service/additionalInfo/profiledBehavior/profiledSuccessfulUserNamesClusterProfiling.2_/userName":"GeneratedFindingUserName3","aws/guardduty/service/additionalInfo/unusualBehavior/unusualASNClusterProfiling/successfulLoginCount":"0","aws/guardduty/service/additionalInfo/unusualBehavior/unusualDatabaseNameClusterProfiling/incompleteConnectionCount":"0","aws/guardduty/service/additionalInfo/profiledBehavior/profiledSuccessfulUserNamesClusterProfiling.0_/userName":"GeneratedFindingUserName1","aws/guardduty/service/additionalInfo/unusualBehavior/unusualUserNameClusterProfiling/successfulLoginCount":"0","aws/guardduty/service/additionalInfo/profiledBehavior/profiledSuccessfulUserNamesClusterProfiling.3_/userName":"GeneratedFindingUserName4","aws/guardduty/service/additionalInfo/profiledBehavior/profiledSuccessfulAsnOrgsClusterProfiling.2_/asnOrg":"GeneratedFindingAsnOrg3","aws/guardduty/service/additionalInfo/unusualBehavior/unusualApplicationNameClusterProfiling/successfulLoginCount":"0","aws/guardduty/service/additionalInfo/unusualBehavior/unusualDatabaseNameClusterProfiling/successfulLoginCount":"0","aws/guardduty/service/additionalInfo/profiledBehavior/profiledSuccessfulAsnOrgsClusterProfiling.1_/count":"1","aws/guardduty/service/additionalInfo/profiledBehavior/profiledSuccessfulAsnOrgsClusterProfiling.3_/count":"1","aws/guardduty/service/additionalInfo/profiledBehavior/profiledSuccessfulUserNamesClusterProfiling.1_/count":"1","aws/guardduty/service/additionalInfo/unusualBehavior/unusualUserNameClusterProfiling/userName":"GeneratedFindingUserName","aws/securityhub/FindingId":"arn:aws:securityhub:us-east-1::product/aws/guardduty/arn:aws:guardduty:us-east-1:517803882956:detector/2ccd501f6c1ad78037a84d3fc2c7e8c9/finding/633b4b32bddc4195bffe43c03de41e02","aws/securityhub/ProductName":"GuardDuty","aws/securityhub/CompanyName":"Amazon"},"SchemaVersion":"2018-10-08","GeneratorId":"arn:aws:guardduty:us-east-1:517803882956:detector/2ccd501f6c1ad78037a84d3fc2c7e8c9","Sample":true,"RecordState":"ACTIVE","Title":"One or more unusual failed login attempts were observed on an RDS database in your account.","Workflow":{"Status":"NEW"},"Severity":{"Normalized":40,"Label":"HIGH","Product":8},"UpdatedAt":"2025-11-21T14:01:40.823Z","WorkflowState":"NEW","AwsAccountId":"517803882956","Region":"us-east-1","Id":"arn:aws:guardduty:us-east-1:517803882956:detector/2ccd501f6c1ad78037a84d3fc2c7e8c9/finding/633b4b32bddc4195bffe43c03de41e02","Resources":[{"Partition":"aws","Type":"AwsRdsDbCluster","Details":{"AwsRdsDbCluster":{"EngineVersion":"13.6","VpcSecurityGroups":[],"DbClusterIdentifier":"GeneratedFindingDBClusterId","Engine":"GeneratedFindingEngine"}},"Region":"us-east-1","Id":"arn:aws:rds:us-east-1:517803882956:cluster:GeneratedFindingDBClusterId"}],"ProcessedAt":"2025-11-21T14:05:01.838Z"}]}}
Inspector
{"version":"0","id":"9adcea1c-0fc0-46d8-111b-c6a16612ab16","detail-type":"Security Hub Findings - Imported","source":"aws.securityhub","account":"517803882956","time":"2025-11-21T13:47:31Z","region":"us-east-1","resources":["arn:aws:securityhub:us-east-1::product/aws/inspector/arn:aws:inspector2:us-east-1:517803882956:finding/f1735a6942c98f2ff1b78e59f251b0a3"],"detail":{"findings":[{"ProductArn":"arn:aws:securityhub:us-east-1::product/aws/inspector","Types":["Software and Configuration Checks/Vulnerabilities/CVE"],"Description":"libxml2 before 2.12.10 and 2.13.x before 2.13.6 has a stack-based buffer overflow in xmlSnprintfElements in valid.c. To exploit this, DTD validation must occur for an untrusted document or untrusted DTD. NOTE: this is similar to CVE-2017-9047.","ProductName":"Inspector","FirstObservedAt":"2025-11-20T10:03:10.196Z","CreatedAt":"2025-10-27T10:58:32.876Z","LastObservedAt":"2025-11-21T11:02:08.890Z","Vulnerabilities":[{"ReferenceUrls":["https://alas.aws.amazon.com/AL2/ALAS2-2025-2794.html","https://explore.alas.aws.amazon.com/CVE-2025-24928.html","https://explore.alas.aws.amazon.com/cve/json/v1/CVE-2025-24928.json","https://alas.aws.amazon.com/AL2023/ALAS2023-2025-896.html","https://alas.aws.amazon.com/ALAS-2025-1965.html"],"Cvss":[{"Version":"3.1","BaseScore":7.8,"BaseVector":"CVSS:3.1/AV:L/AC:H/PR:N/UI:N/S:C/C:H/I:H/A:N","Source":"AMAZON_CVE"},{"Version":"3.1","BaseScore":7.7,"BaseVector":"CVSS:3.1/AV:L/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:N","Source":"NVD"},{"Version":"3.1","BaseVector":"CVSS:3.1/AV:L/AC:H/PR:N/UI:N/S:C/C:H/I:H/A:N","BaseScore":7.8,"Source":"AMAZON_CVE"}],"FixAvailable":"YES","ExploitAvailable":"NO","VulnerablePackages":[{"Architecture":"X86_64","PackageManager":"OS","Version":"2.10.4","Epoch":"0","FixedInVersion":"0:2.10.4-1.amzn2023.0.9","Remediation":"sudo dnf check-update","Release":"1.amzn2023.0.1","Name":"libxml2"}],"EpssScore":0.00023,"Id":"CVE-2025-24928","RelatedVulnerabilities":["ALAS2023-2025-896","ALAS2-2025-2794","ALAS-2025-1965"],"Vendor":{"VendorCreatedAt":"2025-02-18T00:00:00.000Z","VendorSeverity":"Important","Url":"https://explore.alas.aws.amazon.com/cve/json/v1/CVE-2025-24928.json","Name":"AMAZON_CVE","VendorUpdatedAt":"2025-02-24T00:00:00.000Z"}}],"CompanyName":"Amazon","FindingProviderFields":{"Types":["Software and Configuration Checks/Vulnerabilities/CVE"],"Severity":{"Normalized":70,"Label":"HIGH"}},"ProductFields":{"aws/inspector/ProductVersion":"2","aws/inspector/FindingStatus":"ACTIVE","aws/inspector/inspectorScore":"7.8","aws/inspector/instanceId":"i-0eef60192bcbea98a","aws/inspector/resources/1/resourceDetails/awsEc2InstanceDetails/platform":"AMAZON_LINUX_2023","aws/securityhub/FindingId":"arn:aws:securityhub:us-east-1::product/aws/inspector/arn:aws:inspector2:us-east-1:517803882956:finding/f1735a6942c98f2ff1b78e59f251b0a3","aws/securityhub/ProductName":"Inspector","aws/securityhub/CompanyName":"Amazon"},"Remediation":{"Recommendation":{"Text":"Remediation is available. Please refer to the Fixed version in the vulnerability details section above.For detailed remediation guidance for each of the affected packages, refer to the vulnerabilities section of the detailed finding JSON."}},"SchemaVersion":"2018-10-08","GeneratorId":"AWSInspector","RecordState":"ACTIVE","Title":"CVE-2025-24928 - libxml2","Workflow":{"Status":"NEW"},"Severity":{"Normalized":70,"Label":"HIGH"},"UpdatedAt":"2025-11-21T11:02:08.890Z","WorkflowState":"NEW","AwsAccountId":"517803882956","Region":"us-east-1","Id":"arn:aws:inspector2:us-east-1:517803882956:finding/f1735a6942c98f2ff1b78e59f251b0a3","Resources":[{"Partition":"aws","Type":"AwsEc2Instance","Details":{"AwsEc2Instance":{"KeyName":"webserver","Type":"t2.micro","VpcId":"vpc-073d578d9feb575b0","ImageId":"ami-0715c1897453cabd1","IpV4Addresses":["10.0.17.3","3.94.231.28"],"SubnetId":"subnet-01fcfc376d81dd3d5","LaunchedAt":"2024-03-18T12:52:51.000Z"}},"Region":"us-east-1","Id":"arn:aws:ec2:us-east-1:517803882956:instance/i-0eef60192bcbea98a","Tags":{"Name":"Mywebserver"}}],"ProcessedAt":"2025-11-21T13:47:23.962Z"}]}}
Macie
{"version":"0","id":"13ee7309-a1fd-58c8-33dd-55a607f85d67","detail-type":"Security Hub Findings - Imported","source":"aws.securityhub","account":"517803882956","time":"2025-11-21T14:19:22Z","region":"us-east-1","resources":["arn:aws:securityhub:us-east-1::product/aws/macie/44cd501f-8ff0-d324-48fc-d4d801d59957"],"detail":{"findings":[{"ProductArn":"arn:aws:securityhub:us-east-1::product/aws/macie","Types":["Software and Configuration Checks/AWS Security Best Practices/Policy:IAMUser-S3BucketEncryptionDisabled"],"Description":"Default encryption settings for the S3 bucket were reset to default Amazon S3 encryption behavior. Amazon S3 encrypts new objects automatically with an Amazon S3 managed key (SSE-S3).","SchemaVersion":"2018-10-08","ProductName":"Macie","GeneratorId":"aws/macie","Sample":true,"CreatedAt":"2025-11-20T07:51:22.849Z","RecordState":"ACTIVE","Title":"Default encryption settings were reset for the S3 bucket","Workflow":{"Status":"NEW"},"Severity":{"Normalized":1,"Label":"LOW"},"UpdatedAt":"2025-11-21T14:01:29.774Z","CompanyName":"Amazon","FindingProviderFields":{"Types":["Software and Configuration Checks/AWS Security Best Practices/Policy:IAMUser-S3BucketEncryptionDisabled"],"Severity":{"Normalized":1,"Label":"LOW"}},"WorkflowState":"NEW","ProductFields":{"S3Bucket.effectivePermission":"PUBLIC","aws/securityhub/FindingId":"arn:aws:securityhub:us-east-1::product/aws/macie/44cd501f-8ff0-d324-48fc-d4d801d59957","aws/securityhub/ProductName":"Macie","aws/securityhub/CompanyName":"Amazon"},"AwsAccountId":"517803882956","Region":"us-east-1","Id":"44cd501f-8ff0-d324-48fc-d4d801d59957","Resources":[{"Partition":"aws","Type":"AwsS3Bucket","Details":{"AwsS3Bucket":{"PublicAccessBlockConfiguration":{"RestrictPublicBuckets":false,"BlockPublicPolicy":false,"BlockPublicAcls":false,"IgnorePublicAcls":false},"OwnerName":"John Doe","OwnerId":"7009a8971cd538e11f6b6606438875e7c86c5b672f46db45460ddcd087d36c32","CreatedAt":"2025-11-21T14:01:29.774Z","ServerSideEncryptionConfiguration":{"Rules":[{"ApplyServerSideEncryptionByDefault":{"SSEAlgorithm":"NONE"}}]},"OwnerAccountId":"517803882956"}},"Region":"us-east-1","Id":"arn:aws:s3:::macie-sample-finding-bucket","Tags":{"Team":"Recruiting","Division":"HR"}}],"ProcessedAt":"2025-11-21T14:19:18.728Z"}]}}
Security Hub
{"version":"0","id":"e86883d9-b269-7893-60d6-67d53a1e6dea","detail-type":"Security Hub Findings - Imported","source":"aws.securityhub","account":"517803882956","time":"2025-11-21T08:47:46Z","region":"us-east-1","resources":["arn:aws:securityhub:us-east-1::product/aws/securityhub/arn:aws:securityhub:us-east-1:517803882956:security-control/CloudWatch.1/finding/c2d35028-f2b9-4ecb-8f0c-be15f5f2898b"],"detail":{"findings":[{"ProductArn":"arn:aws:securityhub:us-east-1::product/aws/securityhub","Types":["Software and Configuration Checks/Industry and Regulatory Standards"],"Description":"This control checks for the CloudWatch metric filters using the following pattern { $.userIdentity.type = \"Root\" && $.userIdentity.invokedBy NOT EXISTS && $.eventType != \"AwsServiceEvent\" } It checks that the log group name is configured for use with active multi-region CloudTrail, that there is at least one Event Selector for a Trail with IncludeManagementEvents set to true and ReadWriteType set to All, and that there is at least one active subscriber to an SNS topic associated with the alarm.","Compliance":{"Status":"FAILED","StatusReasons":[{"Description":"Multi region CloudTrail with the required configuration does not exist in the account","ReasonCode":"CLOUDTRAIL_MULTI_REGION_NOT_PRESENT"}],"SecurityControlId":"CloudWatch.1","RelatedRequirements":["CIS AWS Foundations Benchmark v1.2.0/1.1","CIS AWS Foundations Benchmark v1.2.0/3.3","CIS AWS Foundations Benchmark v1.4.0/1.7","CIS AWS Foundations Benchmark v1.4.0/4.3","PCI DSS v3.2.1/7.2.1"],"AssociatedStandards":[{"StandardsId":"ruleset/cis-aws-foundations-benchmark/v/1.2.0"},{"StandardsId":"standards/cis-aws-foundations-benchmark/v/1.4.0"},{"StandardsId":"standards/pci-dss/v/3.2.1"}]},"ProductName":"Security Hub","FirstObservedAt":"2023-06-07T16:13:52.356Z","CreatedAt":"2023-06-07T16:13:52.356Z","LastObservedAt":"2025-11-21T08:47:22.958Z","CompanyName":"AWS","FindingProviderFields":{"Types":["Software and Configuration Checks/Industry and Regulatory Standards"],"Severity":{"Normalized":1,"Label":"LOW","Original":"LOW"}},"ProductFields":{"aws/securityhub/ProductName":"Security Hub","aws/securityhub/CompanyName":"AWS","aws/securityhub/annotation":"Multi region CloudTrail with the required configuration does not exist in the account","Resources:0/Id":"arn:aws:iam::517803882956:root","aws/securityhub/FindingId":"arn:aws:securityhub:us-east-1::product/aws/securityhub/arn:aws:securityhub:us-east-1:517803882956:security-control/CloudWatch.1/finding/c2d35028-f2b9-4ecb-8f0c-be15f5f2898b","PreviousComplianceStatus":"FAILED"},"Remediation":{"Recommendation":{"Text":"For information on how to correct this issue, consult the AWS Security Hub controls documentation.","Url":"https://docs.aws.amazon.com/console/securityhub/CloudWatch.1/remediation"}},"SchemaVersion":"2018-10-08","GeneratorId":"security-control/CloudWatch.1","RecordState":"ACTIVE","Title":"A log metric filter and alarm should exist for usage of the \"root\" user","Workflow":{"Status":"NEW"},"Severity":{"Normalized":1,"Label":"LOW","Original":"LOW"},"UpdatedAt":"2025-11-21T08:47:22.958Z","WorkflowState":"NEW","AwsAccountId":"517803882956","Region":"us-east-1","Id":"arn:aws:securityhub:us-east-1:517803882956:security-control/CloudWatch.1/finding/c2d35028-f2b9-4ecb-8f0c-be15f5f2898b","Resources":[{"Partition":"aws","Type":"AwsAccount","Region":"us-east-1","Id":"AWS::::Account:517803882956"}],"ProcessedAt":"2025-11-21T08:47:37.769Z"}]}}
What Is Provided
-
Rules to parse, normalize, and enrich AWS Security Hub log messages.
-
A Dashboard that delivers an Overview and details related to GuardDuty, Inspector, and Security Hub logs.
Events Processed by This Technology Pack
The content pack supports the following log types.
-
GuardDuty
-
Inspector
-
Macie
-
Security Hub
GIM Categorization
AWS Security Hub GuardDuty and Inspector logs are always categorized as default detections.
Macie logs must have an alert_severity != "INFORMATIONAL" to be categorized as a default detection.
Security Hub logs must have a compliance_finding_status = "FAILED" to be categorized as a default detection.
| Vendor Subtype | GIM Category | GIM Subcategory | GIM Event Type |
|---|---|---|---|
| guardduty | detection | detection.default | detection_message |
| inspector | detection | detection.default | detection_message |
| macie | detection | detection.default | detection_message |
| security_hub | detection | detection.default | detection_message |
Message Fields Included in This Pack
General Parsing, Common Fields List
| Field Name | Example Value | Field Type | Description |
|---|---|---|---|
| alert_severity | high | keyword | The .Severity.Level key in the finding |
| alert_severity_level | 4 | long | The alert severity level associated with the alert_severity field |
| alert_signature | Potential credential compromise of IAMUser/john_doe indicated by a sequence of actions | keyword | The .Title of the finding |
| compliance_finding_* | compliance_finding_associated_standards | keyword | Specific compliance JSON keys from the finding |
| event_source_product | aws_security_hub | keyword | The default event_source_product for AWS Security Hub processed logs |
| file_hash_sha256 |
123456789abcdef123456789abcde f123456789abcdef123456789abcdef1200 |
keyword | The .FilePaths..Hash key in the finding |
| file_name | eicar.com | keyword | The .FilePaths..FileName key in the finding |
| file_path | tmp/eicar.com | keyword | The .Filepaths..FilePath key in the finding |
| resource_* | resource_tags | mixed | Specific resource JSON keys in the finding |
| security_finding_* | security_finding_id | mixed | Specific finding JSON keys in the finding |
| user_id | AIDA3UBBJ2K3TVEXAMPLE | keyword | User ID tied to the message pulled from the .AwsIamAccessKey.PrincipalID key in the finding |
| user_name | some.user | keyword | User name tied to the message pulled from the .AwsIamAccessKey.userName key in the finding |
| user_type | IAMUser | keyword | User type tied to the message pulled from the .AwsIamAccessKey.PrincipalType key |
| vendor_subtype | guardduty | keyword | The .Product key in the finding |
| vulnerability_finding_* | vulnerability_finding_cvss_base_score | keyword | Specific vulnerability JSON keys in the finding |
AWS Security Hub Content Pack
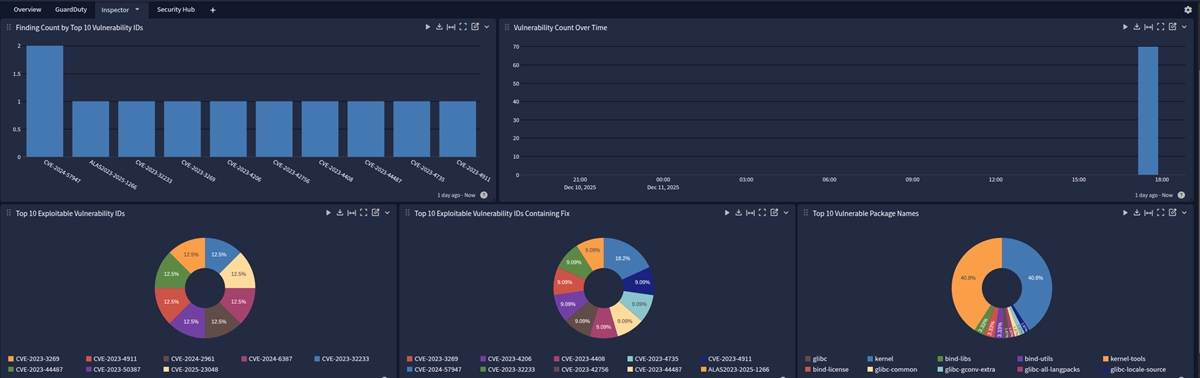
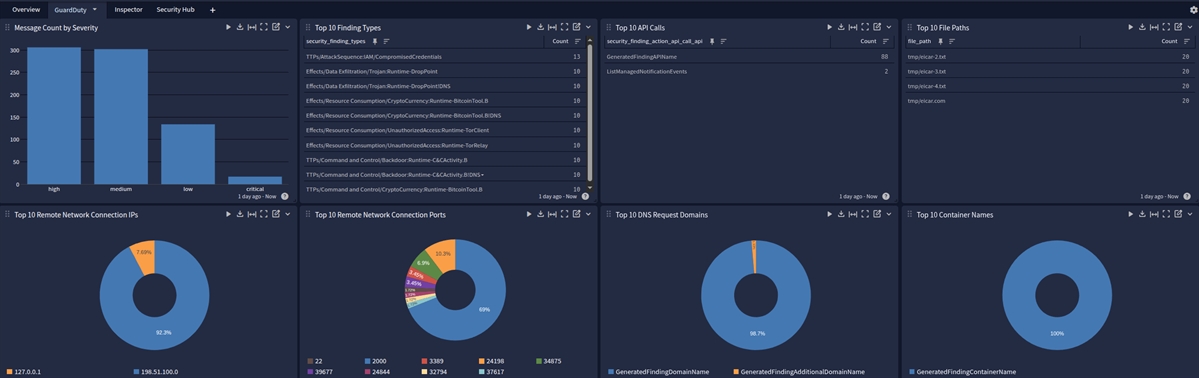
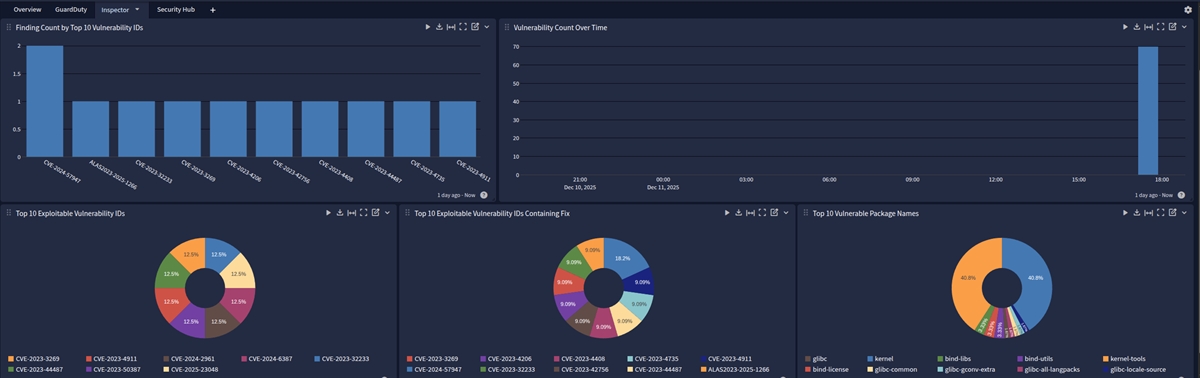
This spotlight offers a dashboard with 4 tabs:
Overview
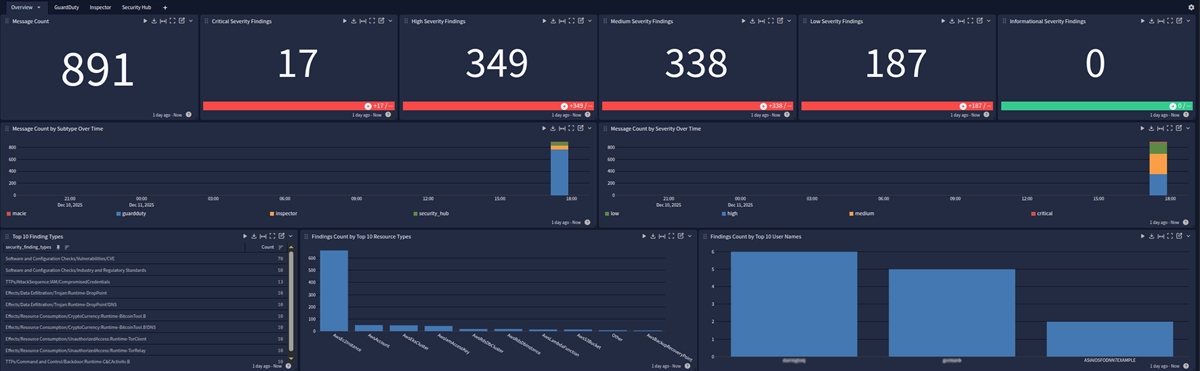
GuardDuty
Inspector
Security Hub