The following article exclusively pertains to a Graylog Enterprise feature or functionality. To learn more about obtaining an Enterprise license, please contact the Graylog Sales team.
The Audit Log tracks changes made to the Graylog system by users, records all state changes into the database, and makes it possible to search, filter, and export all audit log entries.
The web interface can show current configurations.
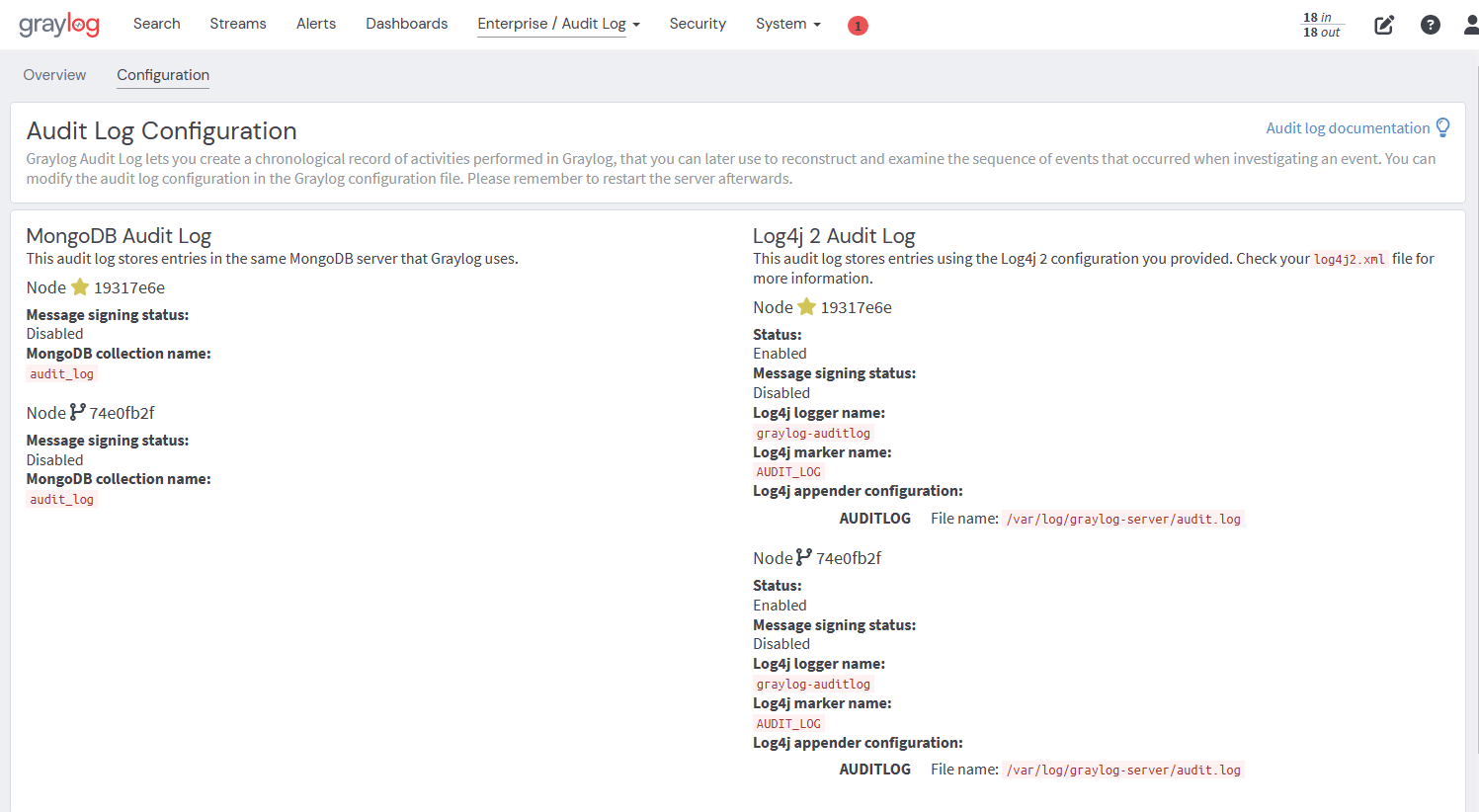
server.conf).
Database Configuration Options
The default MongoDB audit log has a few configuration options:
|
Name |
Description |
|---|---|
|
|
Deletes audit log entries older than configured interval. |
|
|
Interval of the audit log entry cleanup job. |
|
|
The MongoDB collection to store the audit log entries in. |
auditlog_mongodb_keep_entries
This configures the interval at which old audit log entries in the MongoDB database are deleted. Use values like 90d (90 days) to configure the interval. The default value for this is 365d.
Example:
auditlog_mongodb_keep_entries = 365d
auditlog_mongodb_cleanup_interval
This configures the interval of the background job that periodically deletes old audit log entries from the MongoDB database. Use values like 1h(1 hour) to configure the interval. The default value is 1h.
Example:
auditlog_mongodb_cleanup_interval = 1h
auditlog_mongodb_collection
This configures the name of the MongoDB collection where audit log entries will be stored.
The default value for this is audit_log.
Example:
auditlog_mongodb_collection = audit_log
Log4j2 Configuration Options
The optional log4j2 audit log appender has a few configuration options.
|
Name |
Description |
|---|---|
|
|
Whether the log4j2 appender is enabled or not. |
|
|
log4j2 logger name. |
|
|
log4j2 marker name. |
auditlog_log4j_enabled
The log4j2 audit log appender is disabled by default. To enable it, set this option to true.
The default value for this is false.
Example:
auditlog_log4j_enabled = true
auditlog_log4j_logger_name
This configures the log4j2 logger name of the audit log.
The default value for this is gl-org.graylog.plugins.auditlog.
Example:
auditlog_log4j_logger_name = graylog-auditlog
auditlog_log4j_marker_name
This configures the log4j2 marker name for the audit log.
The default value for this is AUDIT_LOG.
Example:
auditlog_log4j_marker_name = AUDIT_LOG
Log4j2 Appender Configuration
To write audit log entries into a file, enable the log4j2 appender in your Graylog configuration file and add configurations to the log4j2.xml file that is used by your server process.
The log4j2.xml file location depends on your deployment method. Please check the default file locations page to confirm file location.
An existing log4j2.xml <Logger/> statement in the <Loggers/> section and an additional appender in the <Appenders/> section of the file.
Example log4j2.xml file with audit log enabled:
<?xml version="1.0" encoding="UTF-8"?>
<Configuration packages="org.graylog2.log4j" shutdownHook="disable">
<Appenders>
<!-- Graylog server log file appender -->
<RollingFile name="rolling-file" fileName="/var/log/graylog-server/server.log" filePattern="/var/log/graylog-server/server.log.%i.gz">
<PatternLayout pattern="%d{yyyy-MM-dd'T'HH:mm:ss.SSSXXX} %-5p [%c{1}] %m%n"/>
<Policies>
<SizeBasedTriggeringPolicy size="50MB"/>
</Policies>
<DefaultRolloverStrategy max="10" fileIndex="min"/>
</RollingFile>
<!-- ##################################################### -->
<!-- Rotate audit logs daily -->
<RollingFile name="AUDITLOG" fileName="/var/log/graylog-server/audit.log" filePattern="/var/log/graylog-server/audit-%d{yyyy-MM-dd}.log.gz">
<PatternLayout>
<Pattern>%d - %m - %X%n</Pattern>
</PatternLayout>
<Policies>
<TimeBasedTriggeringPolicy />
</Policies>
</RollingFile>
<!-- ##################################################### -->
</Appenders>
<Loggers>
<Logger name="org.graylog2" level="info"/>
<!-- ##################################################### -->
<!-- Graylog Audit Log. The logger name has to match the "auditlog_log4j_logger_name" setting in the Graylog configuration file -->
<Logger name="graylog-auditlog" level="info" additivity="false">
<AppenderRef ref="AUDITLOG"/>
</Logger>
<!-- ##################################################### -->
<Root level="warn">
<AppenderRef ref="rolling-file"/>
</Root>
</Loggers>
</Configuration>
The configuration snippets between the <!-- ######### -->tags have been added to the existing log4j2.xmlfile.
Check that the namein the <Logger/> tag matches the configured auditlog_log4j_logger_namein your Graylog server configuration. Otherwise, you will not see any log entries in the log file.
Caveats
Ensure that the log4j2-related settings in the Graylog server configuration file and the log4j2.xml
Every Graylog server writes its audit log entries when the Graylog Operations plugin is installed, so the log files configured in the log4j2.xml
If you have more than one node, search in all configured files on all nodes to get a complete view of the audit trail.
